Researchers Find 3 New Malware Strains Used by SolarWinds Hackers
FireEye and Microsoft on Thursday said they discovered three more malware strains in connection with the SolarWinds supply-chain attack, including a “sophisticated second-stage backdoor,” as the investigation into the sprawling espionage campaign continues to yield fresh clues about the threat actor’s tactics and techniques.
Dubbed GoldMax (aka SUNSHUTTLE), GoldFinder, and Sibot, the new set of malware adds to a growing list of malicious tools such as Sunspot, Sunburst (or Solorigate), Teardrop, and Raindrop that were stealthily delivered to enterprise networks by alleged Russian operatives.
“These tools are new pieces of malware that are unique to this actor,” Microsoft said. “They are tailor-made for specific networks and are assessed to be introduced after the actor has gained access through compromised credentials or the SolarWinds binary and after moving laterally with Teardrop and other hands-on-keyboard actions.”
Microsoft also took the opportunity to name the actor behind the attacks against SolarWinds as NOBELIUM, which is also being tracked under different monikers by the cybersecurity community, including UNC2452 (FireEye), SolarStorm (Palo Alto Unit 42), StellarParticle (CrowdStrike), and Dark Halo (Volexity).
While Sunspot was deployed into the build environment to inject the Sunburst backdoor into SolarWinds’s Orion network monitoring platform, Teardrop and Raindrop have been primarily used as post-exploitation tools to laterally move across the network and deliver the Cobalt Strike Beacon.
Spotted between August to September 2020, SUNSHUTTLE is a Golang-based malware that acts as a command-and-control backdoor, establishing a secure connection with an attacker-controlled server to receive commands to download and execute files, upload files from the system to the server, and execute operating system commands on the compromised machine.
For its part, FireEye said it observed the malware at a victim compromised by UNC2452, but added it hasn’t been able to fully verify the backdoor’s connection to the threat actor. The company also stated it discovered SUNSHUTTLE in August 2020 after it was uploaded to a public malware repository by an unnamed U.S.-based entity.
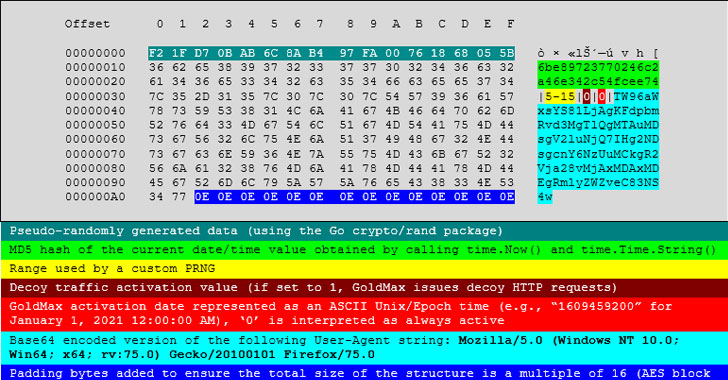
One of the most notable features of GoldMax is the ability to cloak its malicious network traffic with seemingly benign traffic by pseudo-randomly selecting referrers from a list of popular website URLs (such as www.bing.com, www.yahoo.com, www.facebook.com, www.twitter.com, and www.google.com) for decoy HTTP GET requests pointing to C2 domains.
“The new SUNSHUTTLE backdoor is a sophisticated second-stage backdoor that demonstrates straightforward but elegant detection evasion techniques via its ‘blend-in’ traffic capabilities for C2 communications,” FireEye detailed. “SUNSHUTTLE would function as a second-stage backdoor in such a compromise for conducting network reconnaissance alongside other Sunburst-related tools.”
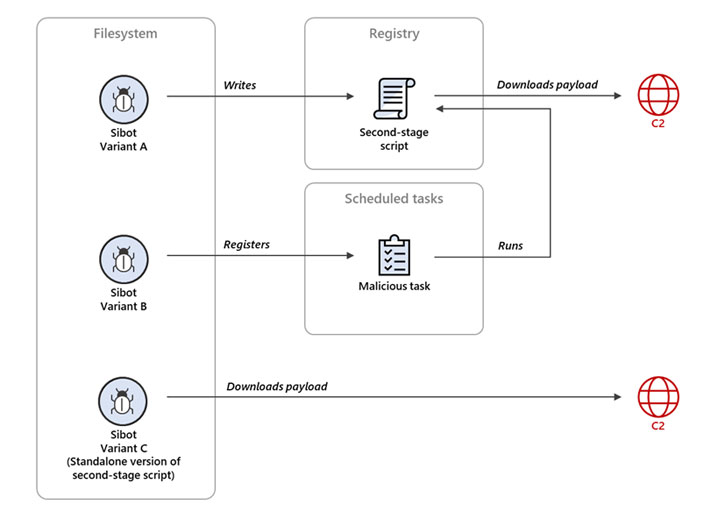
GoldFinder, also written in Go, is an HTTP tracer tool for logging the route a packet takes to reach a C2 server. In contrast, Sibot is a dual-purpose malware implemented in VBScript that’s designed to achieve persistence on infected machines before downloading and executing a payload from the C2 server. Microsoft said it observed three obfuscated variants of Sibot.
Even as the different pieces of SolarWinds attack puzzle fall into place, the development once again underscores the scope and sophistication in the range of methods used to penetrate, propagate, and persist in victim environments.
“These capabilities differ from previously known NOBELIUM tools and attack patterns, and reiterate the actor’s sophistication,” Microsoft said. “In all stages of the attack, the actor demonstrated a deep knowledge of software tools, deployments, security software and systems common in networks, and techniques frequently used by incident response teams.”