Ransomware-Wielding Gangs Love to Phish With Trojan Loaders
Fraud Management & Cybercrime
,
Fraud Risk Management
,
Next-Generation Technologies & Secure Development
Spearheaded by Ryuk and Vatet, Gangs Wield Commodity Downloaders, Researchers Warn
Criminals operating online continue to tap ransomware in their pursuit of an illicit payday.
See Also: Live Webinar | Mitigating the Risks Associated with Remote Work
That was the cybercrime reality throughout 2020, and unfortunately it still appears to be holding true in the first months of 2021, according to incident response engagements conducted by Cisco Talos.
“For the seventh quarter in a row, Cisco Talos Incident Response observed ransomware dominating the threat landscape,” with phishing remaining attackers’ top initial access vector, David Liebenberg and Caitlin Huey, threat intelligence researchers at Cisco Talos, say in a new research report.
The report describes attack trends primarily from November 2020 to January 2021, but with an eye toward recent attacks as well.
“Ransomware continued to comprise the majority of threats [we] observed,” Liebenberg and Huey say, noting that many attackers suddenly appeared to begin favoring phishing emails carrying malicious document attachments as an initial infection vector.
“Nearly 70 percent of ransomware attacks relied on commodity Trojans this quarter,” they say. If executed, the Trojanized documents would often run commodity malware “such as Zloader, BazarLoader and IcedID,” designed to load – aka install – attackers’ ransomware of choice.
“The top variants were Ryuk and Vatet,” the researchers say, noting that in preceding months Ryuk had been quiet. “We also observed variants of Egregor and WastedLocker continuing to target organizations across the globe.”
Human-Operated Ransomware
The increased use of phishing suggests that the tactic is working for attackers. This highlights defenders’ need to ensure they’re taking all technological and training steps possible to block such attacks.
More advanced gangs use so-called “human operated ransomware” tactics. Instead of relying on automated malware to crypto-lock systems, such attackers will instead employ more advanced network penetration skills to pivot across the network, identify and exfiltrate information of potential value and ultimately leave as many systems crypto-locked as possible.
The more large organizations that a ransomware operation can compromise, via so-called big game hunting, the greater their potential payday. Hence, many gangs continue to recruit specialists to maximize their chances. Experts say such specialists can include individuals well-versed in cloud environments as well as network penetration, malware development and “customer support” – aka ransom-payment negotiation – to help convert victims – or “prospects” as salespeople say – into paying customers (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
Fresh Tactics, Techniques, Procedures
Ransomware-wielding attackers continue to use a variety of tools and tactics, which organizations should keep in mind to help them block attacks outright or spot signs of intrusion before attackers have the opportunity to forcibly encrypt systems (see: Ransomware: Beware of 13 Tactics, Tools and Procedures).
Cisco says that some recent trends it has been tracking include the use of:
- Cobalt Strike: Use of this commercially available penetration-testing tool “was observed in half of all ransomware attacks” from November 2020 to January 2021, the researchers say.
- Open-source reconnaissance tools: Cisco says attackers have recently used ADFind, ADRecon and Bloodhound.
- Windows utilities: “PowerShell was observed in nearly 65% of all ransomware attacks, while PsExec usage was observed in more than 30%” of attacks. PowerShell can be used for multiple purposes, including encrypting files, while PsExec can be used to distribute malware.
- Dual-use tools: Attackers have been using the TightVNC remote-access tool to access networks.
- Compression tools: 7-Zip and WinRAR were among the tools most commonly used by attackers to compress data before they exfiltrated it.
Healthcare Strike
In one incident investigated by Cisco, a healthcare organization, which Cisco didn’t name, fell victim to an attack that used many of those tactics, beginning with a phishing attack involving a malicious Microsoft Excel document. The document instructed the recipient to enable macros and then forward the attachment to another colleague. That resulted in what appears to have been a version of Zloader customized for that environment being executed and providing remote access to the attacker, Cisco says.
“The adversary then pivoted in the environment, leveraging the Group Policy replication mechanism in Windows Active Directory to distribute Ryuk and using PsExec to move laterally and execute remote commands, in line with previous Ryuk behavior,” Cisco says (see: Why Hackers Abuse Active Directory). “The adversaries obtained domain administrator credentials and – besides encrypting systems on the network – also wiped backup indexes. More than 1,000 endpoints were encrypted, causing significant damage to the organization, affecting Active Directory, DHCP, DNS and antivirus software. “
Cisco says the healthcare sector in recent months has become the top target for all attackers, whether they’re wielding ransomware, running business email compromise scams or engaging in any other type of attack.
“There are many reasons why actors are continuing to target the healthcare industry, including the COVID-19 pandemic incentivizing victims to pay to restore services as quickly as possible,” Cisco says.
Other sectors being targeted, the company says, included business management, construction, education, energy and utilities, entertainment, financial, government, industrial distribution, legal, manufacturing and technology.
Attackers Continue to Hit RDP
For ransomware gangs, however, phishing isn’t the only tactic used to gain initial access in a victim’s network.
Ransomware incident response firm Coveware, for example, reports that of the thousands of cases it investigated in the last quarter of 2020, over 50% involved phishing, followed closely by attackers accessing poorly secured remote desktop protocol connections to gain entry.
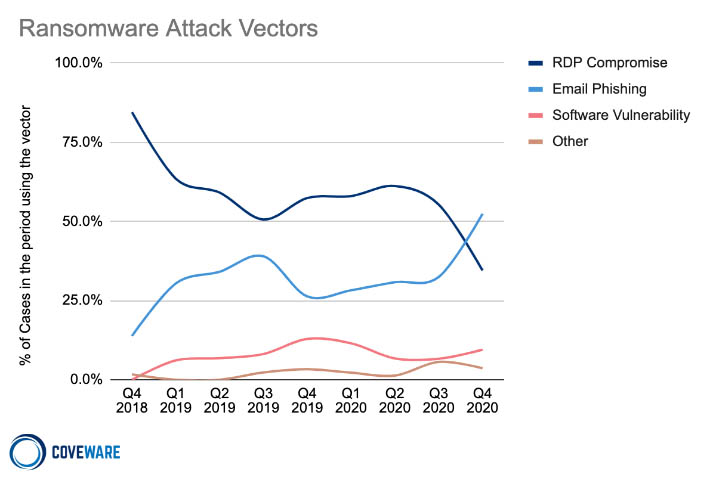
Cisco says that the use of RDP in incidents it investigated has recently increased.
In many cases, the company says, victims lacked effective monitoring and logging tools, which are essential for enabling incident response teams to determine how and when the victim got hit – including the initial access vector – as well as what attackers might have accessed and stolen.






