Ransomware Changes: DoppelPaymer Rebrands; Babuk Evolves
Business Continuity Management / Disaster Recovery
,
Cybercrime
,
Fraud Management & Cybercrime
New ‘Pay or Grief’ CryptoLocking Malware Is DoppelPaymer in Disguise, Experts Say
The ransomware landscape constantly changes, which can make it difficult to track which attackers are coming, going or simply rebranding.
See Also: Live Panel | How Organizations Should Think About Zero Trust
One example is the DoppelPaymer – aka DopplePaymer – ransomware-as-a-service operation, which has gone relatively quiet since early May, posting no victims to its data leak site since May 6 and no leaked files since June 25. But one expert says the operation appears to have been rebranded by its operator, Evil Corp, in an attempt to avoid sanctions imposed on the crime group in December 2019 by the U.S. Treasury Department’s Office of Foreign Assets Control.
The Babuk ransomware operation also recently appears to have altered its approach – if not splintered – following its late-April ransomware attack against the Metropolitan Police Department of Washington, D.C.
In fact, the fallout from numerous attacks – especially the Colonial Pipeline hit by DarkSide and the Kaseya strike by REvil, aka Sodinokibi – appear to have led at least some ransomware operations to stand down, at least temporarily, or alter their approach (see: ‘Fear’ Likely Drove Avaddon’s Exit From Ransomware Fray).
DoppelPaymer Rebrands
After a very brief lull, DoppelPaymer appears to be back, albeit in the guise of an operation called Grief, for “pay or grief,” security experts say.
“DoppelPaymer is a product of Evil Corp, and Evil likely launched and transitioned to the Grief brand either so organizations would not realize they are breaking OFAC sanctions when paying or, perhaps, to provide them with plausible deniability,” Brett Callow, a threat analyst at security firm Emsisoft, tells Information Security Media Group. If so, this wouldn’t be the first time that Evil Corp had rebranded its malware in an apparent attempt to evade sanctions (see: Evil by a Different Name: Crime Gang Rebrands Ransomware).
Like DoppelPaymer, Grief is a ransomware-as-a-service operation, which refers to a business model in which operators develop crypto-locking malware, which gets used by affiliates to infect victims. Both operators and affiliates then share any profits.
Fabian Wosar, CTO of Emsisoft, told Bleeping Computer last month, when Grief was first spotted in the wild, that DoppelPaymer and Grief encrypt files in the same manner and have also used the Dridex botnet for distribution.
More evidence they’re the same operation: A Grief ransomware executable first compiled on May 17 included Grief’s crypto-locking code and note but directed victims to DoppelPaymer’s payment portal, says Brett Stone-Gross, director of threat intelligence at cloud security firm Zscaler, in a blog post.
“This suggests that the malware author may have still been in the process of developing the Grief ransom portal. Ransomware threat groups often rebrand the name of the malware as a diversion,” he says, adding that the code has minor changes, while the ransomware sports “a new cosmetic theme.”
Since mid-May, Grief has been very active, even while being “successful in maintaining a low profile so far,” he says.
Grief’s dedicated data leak site, reachable only via the anonymizing Tor browser, listed 26 victims as of Friday.
One change from the DoppelPaymer days is that while the group previously demanded payment in bitcoins, Grief wants victims to pay in monero, which is a more privacy-preserving cryptocurrency. That may be because the FBI was able to successfully recover some of the bitcoins Colonial Pipeline paid to DarkSide, Stone-Gross says.
Babuk Apparently Splinters
The Babuk operation appears to have splintered in the wake of its attack against Washington’s metropolitan police force. But the cause of the rupture or change in approach isn’t clear.
In a May 13 post to Babuk’s data leak site, the author stated: “I handed over the source code to another team, which will continue to develop the product under a different brand, I remain the only owner of the domain and blog, my service will continue to develop,” according to Israeli threat intelligence firm Kela.
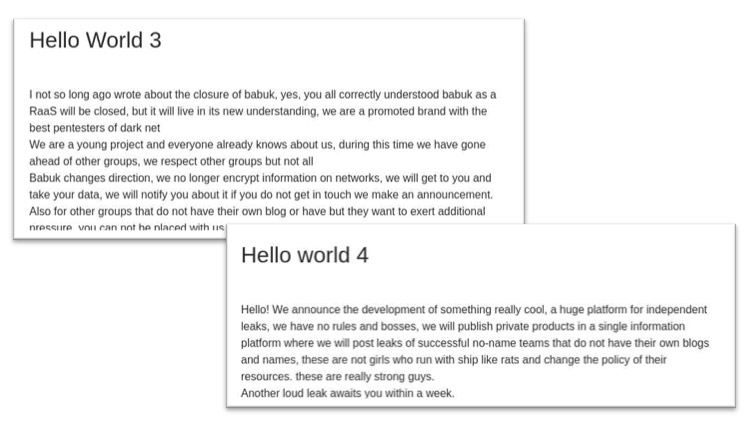
The author also appears to have then launched a leak site called Payload.bin and later a cybercrime forum called RAMP.
Security researchers Thibault Seret of McAfee and Noël Keijzer of Northwave say that the Babuk admin’s apparent move away from targeting organizations with ransomware to instead threatening to leak files may have been driven by an inability to develop malware that can successfully encrypt and decrypt non-Windows files types.
“Babuk announced on an underground forum that it was developing a cross-platform binary aimed at Linux/Unix and ESXi or VMware systems,” the researchers write in a technical analysis, noting that a long-dreaded capability – cross-platform ransomware – appeared to have finally come to pass.
Here’s the potential threat this evolution poses to businesses: “Many core backend systems in companies are running on these *nix operating systems or, in the case of virtualization, think about the ESXi hosting several servers or the virtual desktop environment,” they say.
McAfee doesn’t date that post. But Kela notes that those claims were made in a July 18 post to RAMP.
Crypto Problems
Babuk, however, didn’t appear to be able to deliver on the technical capabilities it boasted of developing, due to poorly built software.
“Even if a victim gave in to the demands and was forced to pay the ransom, they still could not get their files back,” Seret and Keijzer say.
Any affiliates of the operation, furthermore, might have been burned by the failure of the crypto-locking code to reliably decrypt files. “The affiliates are the ones performing the actual compromise and are now faced with a victim that cannot get their data back even if they pay,” the researchers say. “This essentially changes the crime dynamic from extortion to destruction which, from a criminal’s point of view, is much less profitable.”
Failed Reverse-Engineering of DarkSide?
How might Babuk’s inability to build malware to reliably encrypt Linux/Unix, ESXi or VMware systems have come to pass?
In a conversation with Kela – presumably operating undercover – the apparent administrator first of Babuk and then of the RAMP forum said the new crypto-locking capability was meant to be based on code developed by the DarkSide ransomware operation.
“A guy who made Babuk for me just took the DarkSide ESX locker and reversed it. I can’t tell if there is a problem with the ESX [version] because I’ve used it only for three companies,” the administrator told Kela.
Whether the RAMP administrator is part of the original, core team running Babuk remains unclear. Likewise, if the Babuk code got handed off to someone else, why was it still being developed to hit non-Windows systems?
Victoria Kivilevich, a threat intelligence analyst at Kela, says in a new report that RAMP’s administrator – first going by “TetyaSluha,” and now by “Orange” – also posted to RAMP the builder for Babuk, which is used to generate crypto-locking malware and a decryptor. The builder was also posted to VirusTotal on June 27, although it remains unclear who posted it.
Babuk’s dedicated data leak site was renamed on June 1 to Payload.bin, a leak site that said it would feature data stolen by other groups. On July 12, the site was renamed RAMP, short for Ransom Anon Market Place – also a reference to Russian Anonymous Marketplace, which closed in 2017, formerly led by an admin named “Orange” – and badged as being a cybercrime forum dedicated in part to ransomware-as-a-service operations, Kela says.
Who’s Running Babuk 2.0?
The URL for Babuk’s former data leak site later redirected to Payload.bin, and now redirects to RAMP, suggesting Orange has been in control of them all.
Orange now doesn’t appear to be connected with anything still calling itself the Babuk operation, Kela says.
But there’s another leak site for an operation calling itself Babuk 2.0, which posted its latest victim on Tuesday. Kela says that site launched on July 1, and its operators claimed the old version of Babuk ransomware was leaked, while the new version is being used in ongoing attacks.
As of Friday, Babuk 2.0’s dedicated data leak site, reachable only via the anonymizing Tor browser, listed five victims.
Spammers Hit RAMP
Could the failure of a previous version of Babuk ransomware to reliably encrypt non-Windows file types have driven the administrator now known as Orange to pursue other criminal business models, perhaps at the expense of former colleagues? Or is Orange still involved in everything with a Babuk name, and not just RAMP? The answers to these questions aren’t clear.
But all has not been smooth sailing for RAMP, which went offline on Tuesday. Chatter on underground forums, via cybercrime watcher “vx-underground” and others, is that RAMP on July 23 received a demand from an attacker to pay $5,000 or else face disruption. Subsequently, the site was flooded with porn GIFs, and Orange took it offline on Tuesday, promising to rebuild it from scratch and setting an Aug. 13 relaunch date, Kela reports.
Ransomware group drama.
RAMP, the forum started by Babuk ransomware group, has seen a surge of flooding and spamming. An unknown individual is stating they have 24 hours to pay $5,000 or else.
Ransomware actors are ransoming other ransomware actors. pic.twitter.com/Iu1vfQtBLL— vx-underground (@vxunderground) July 23, 2021
“The forum will be relaunched and registration will become available based on certain conditions,” Kela says.
As specified on RAMP’s Tor-based homepage, anyone who wants to register must demonstrate that they already have accounts with other acceptable Russian-language cybercrime forums – such as XSS and Exploit – and have been registered there for at least two months, posted at least 10 times and have a positive reputation score. Otherwise, new registrants will be required to pay $500.
Kela’s Kivilevich notes that compared to other forums, this amount seems excessive. “For example, a premium user on XSS costs $120 for a year,” she says. “Moreover, Russian cybercriminals are not used to paying money for registration on forums, especially such a – relatively – big sum.”
The homepage for RAMP currently features a timer counting down to its relaunch and a statement blaming the outage and need to rebuild the site on former co-workers. “The old team wants … to throw a stone on my back, initially we agreed that they would take their crooked code and I will take the blog – by right, it belongs to me,” the administrator states on the homepage, before threatening reprisal if the disruptions recur.
“Once again, if you try to interfere in my affairs, I will start working against you – I have insiders,” the admin says.






