Post Office is new prime target in UK parcel delivery phishing attacks
The coronavirus pandemic resulted in the closure of many bricks and mortar retail stores, forcing UK consumers to adopt online shopping more than ever before. This trend has largely continued in spite of many stores since reopening, as millions of consumers have become accustomed to the practical benefits of online shopping.
Along with this increased volume of online shopping came a new trend of phishing attacks where cybercriminals impersonate parcel delivery companies in an attempt to steal financial details from their victims. Royal Mail and Hermes were popular targets for these types of attack, but most new attacks now impersonate the Post Office.
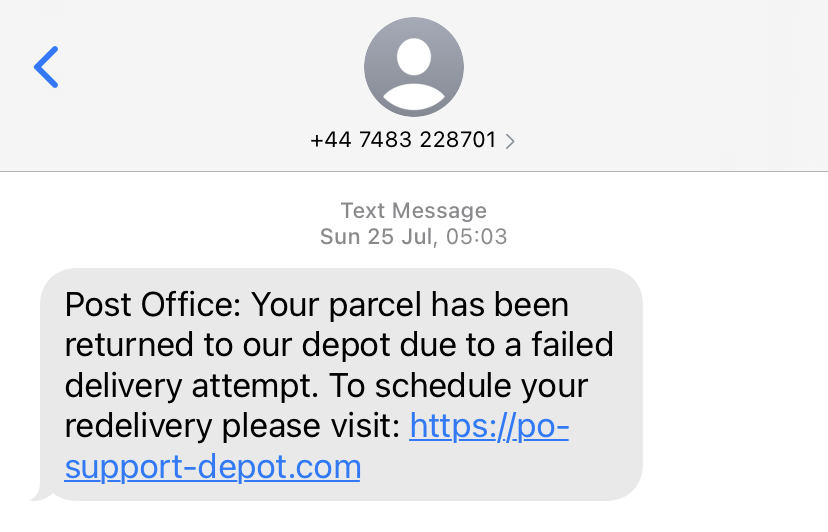
A typical text message used to lure victims to a phishing site that impersonates the Post Office.
These attacks are typically disseminated via text message, informing the victim that they have missed a delivery. Sometimes the messages say up front that the recipient must rebook the delivery by paying a small surcharge. The relatively small surcharge is often sufficient to trick victims into believing the phishing site is legitimate, or at least that any risk is minimal, allowing the phisher to obtain the victim’s details and potentially steal a much larger amount.
As most of the attacks are orchestrated via text message, the phishing sites are usually hosted with purpose-bought domain names that include the targeted company’s name in an attempt to be convincing. Some examples include:
- myhermes-youritem.com
- reschedule-postoffice.com
- royalmail-customer.com
- dpd.delivery.150227811923.com
Some messages instead use generic URL shorteners to take victims to the phishing sites, but this would not necessarily be viewed as suspicious by all recipients, as the use of URL shorteners is commonplace even in legitimate text messages.
Most of the phishing kits used in these attacks also attempt to evade detection by blocking unwanted clients such as bots and anti-phishing organisations, but Netcraft successfully circumvents these checks.
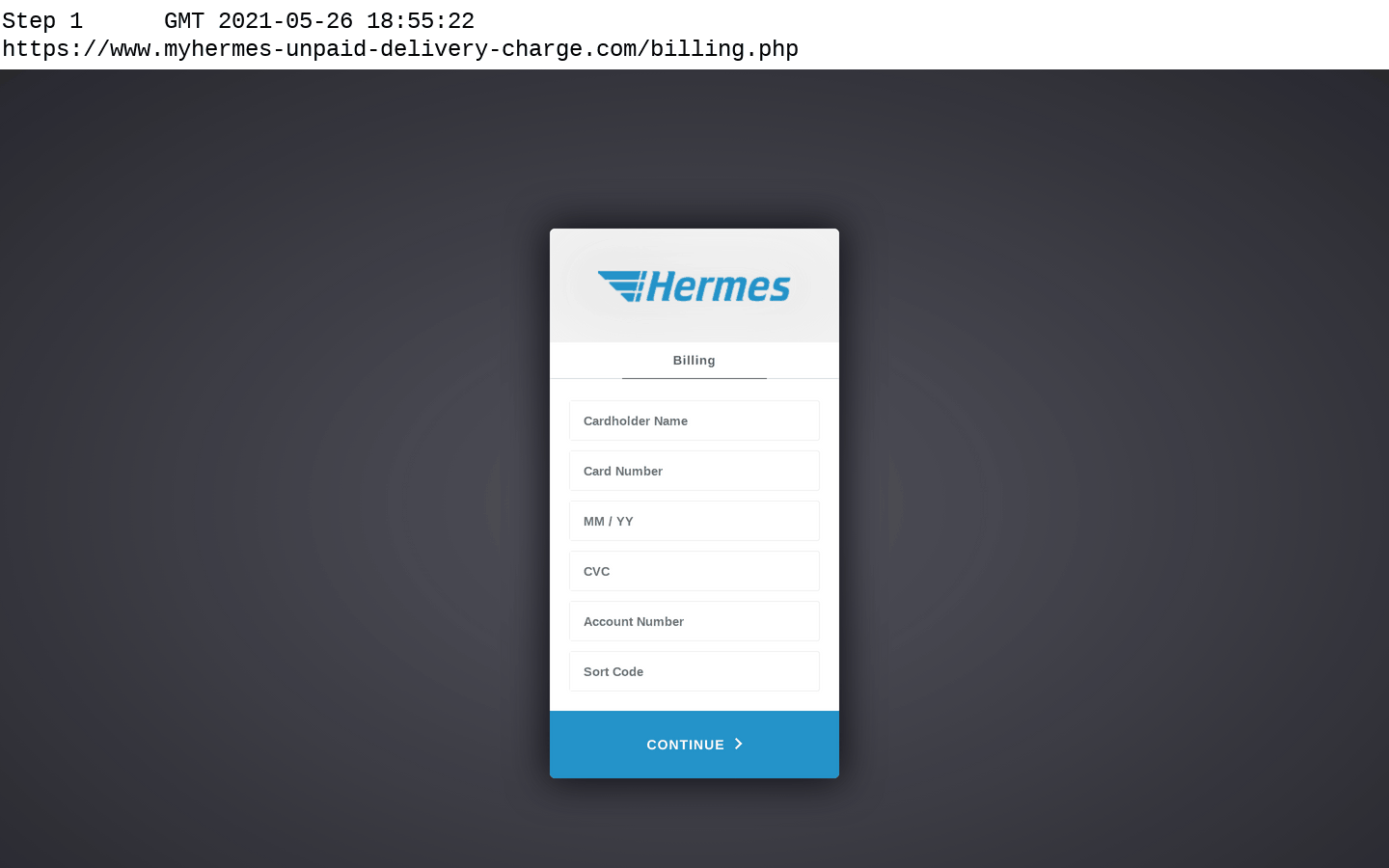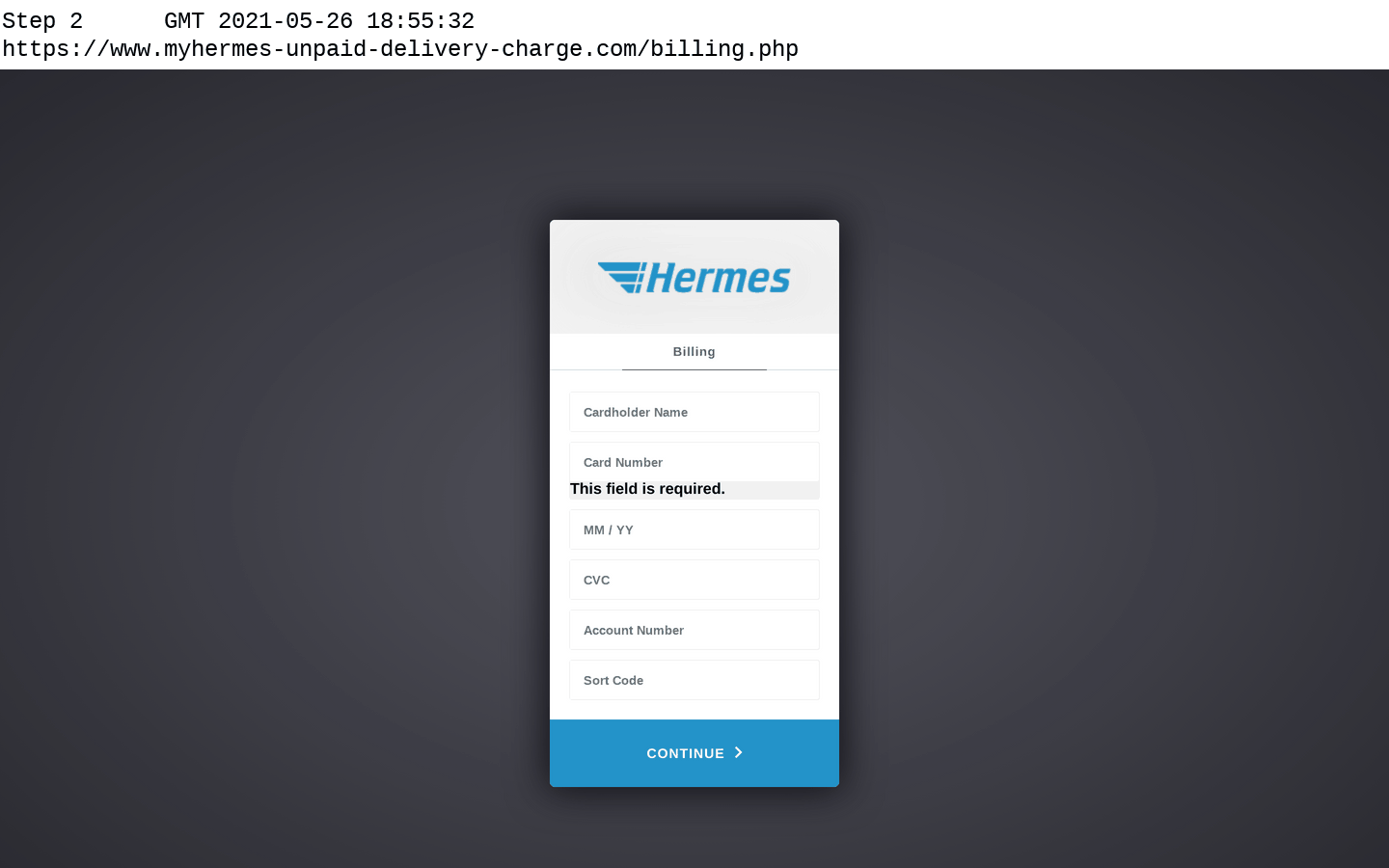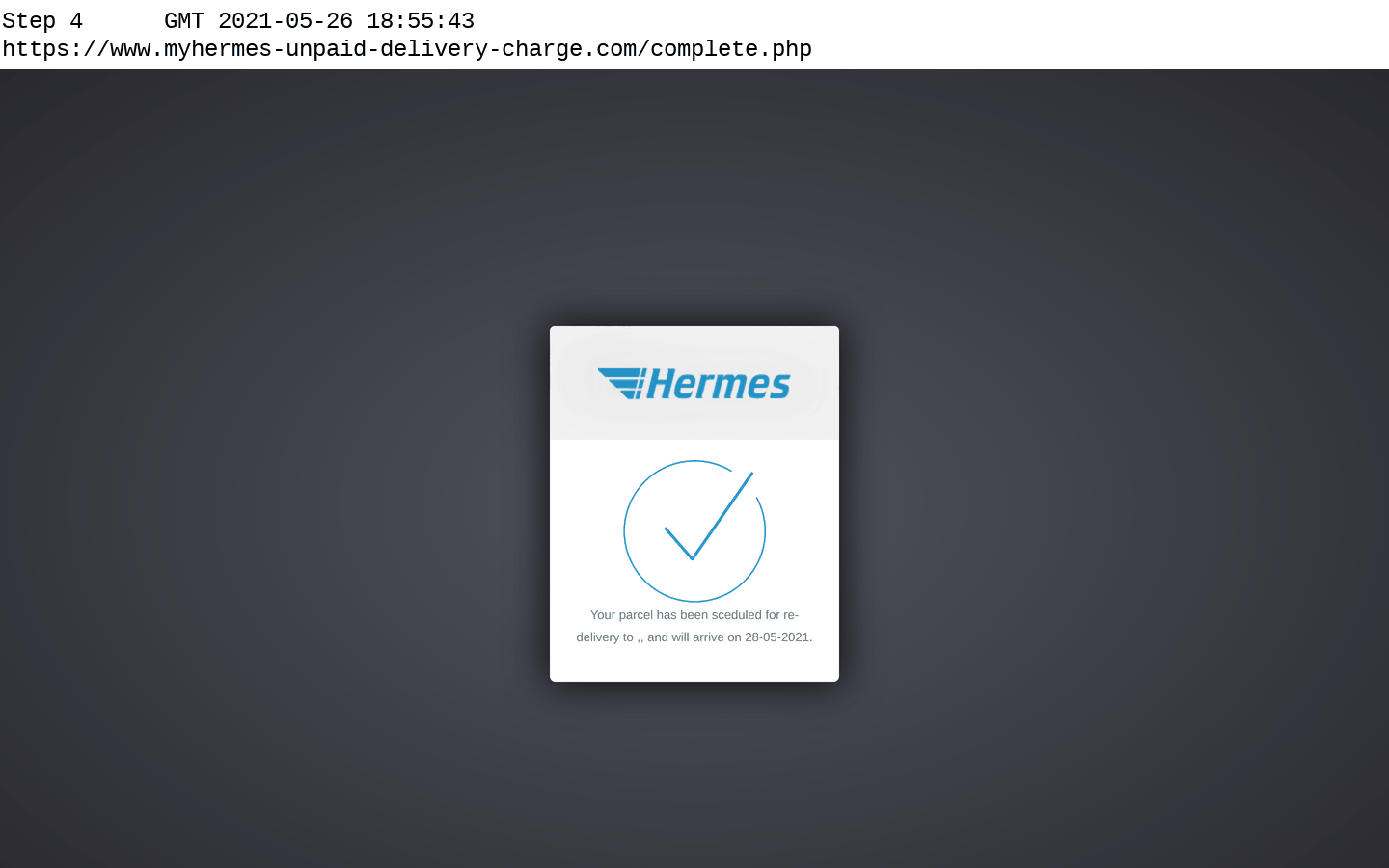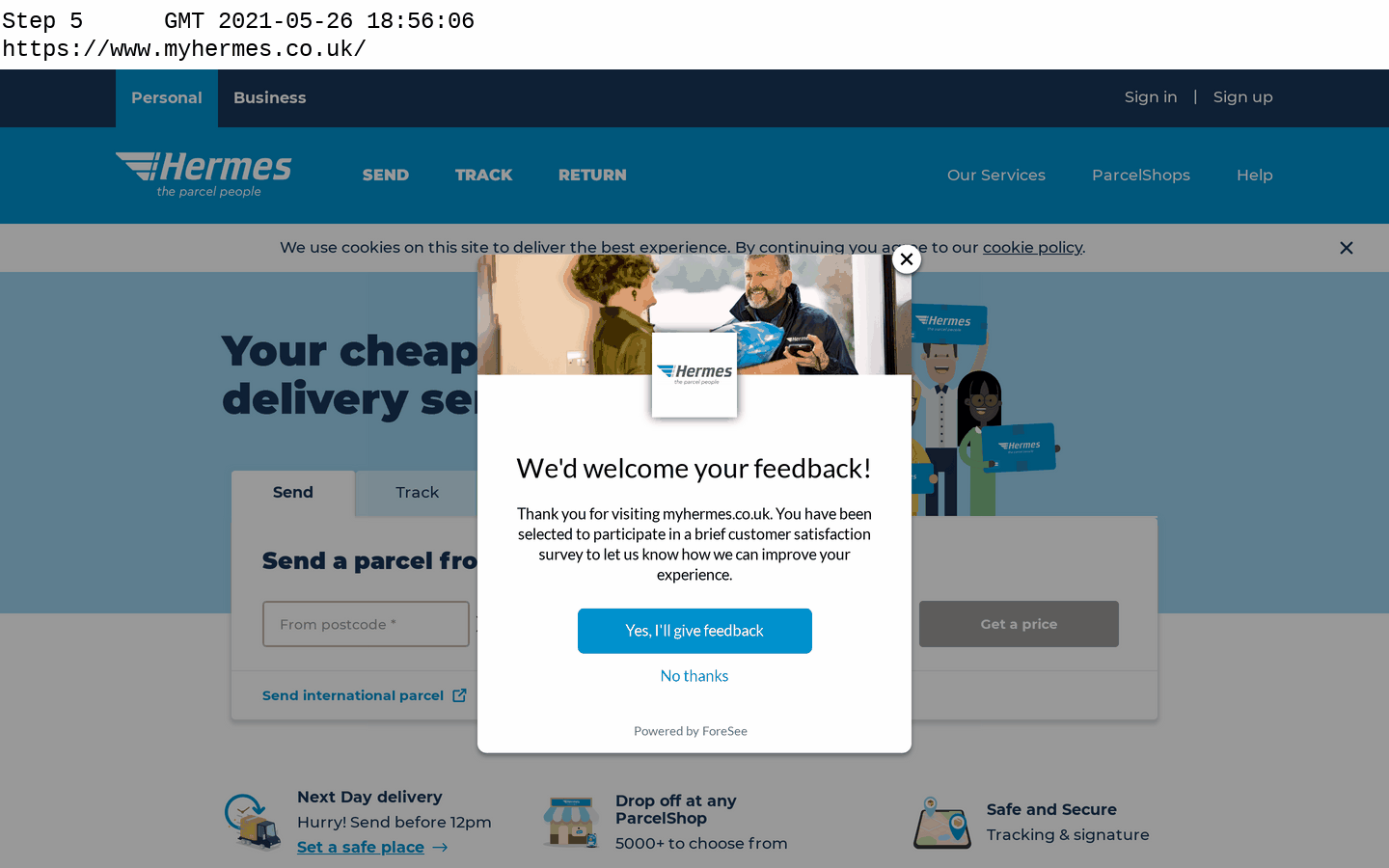
Navigating through a simple Hermes phishing site that is optimised for mobile devices. The victim is redirected to the real Hermes website after their details have been stolen.
After impersonating the delivery company, some of these phishing attacks proceed to also impersonate one of several UK banks. This gives the criminal an opportunity to steal additional credentials that are specific to each bank, such as online banking security codes and other tokens that would likely be used to gain unauthorised access to the victim’s bank account.
Some attacks – particularly those that do not use the phishing site to directly impersonate the victim’s bank – are followed up by a phone call from the cybercriminal, who will use the information stolen by the phishing site to convince the victim that it is a genuine call from their bank regarding the payment they just made. This provides a more interactive opportunity for the criminal to obtain the information required to gain access to the victim’s bank account, including time-sensitive OTP codes.
Example attack
The majority of these attacks follow the same pattern. Taking a Hermes phishing kit as a typical example, the victim is required to enter their postcode to view the tracking status for their parcel. When the victim clicks “View full tracking details”, they will be prompted to enter their name, date of birth, and address.
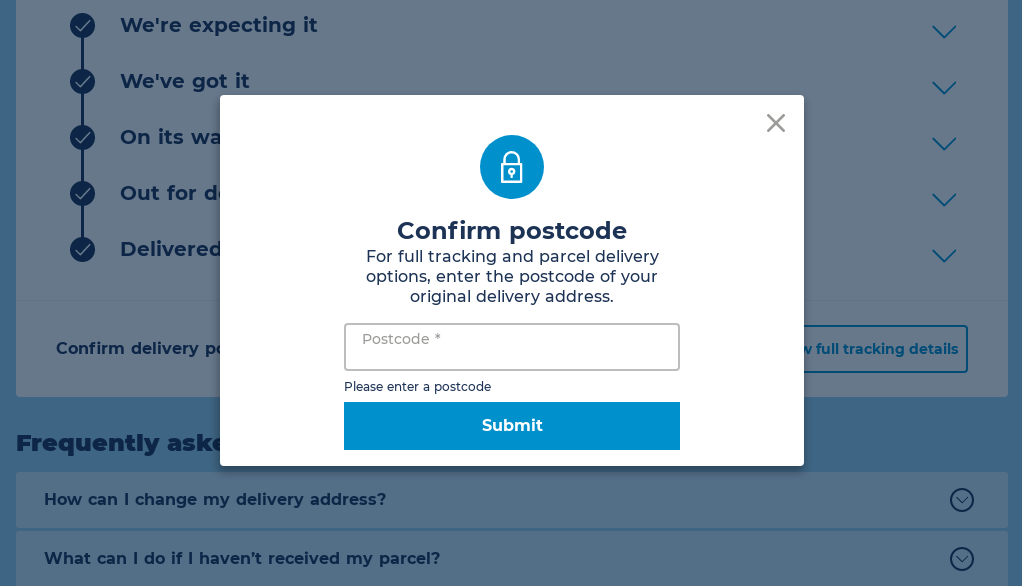
This Hermes phishing site was hosted at hermes-track.delivery prior to being taken down.
After submitting this information, the phishing site will state that there is a redelivery fee of 1.45 GBP to be paid, and asks the victim to provide their card details (cardholder’s name, card number, expiry date, CVV), bank account number, and sort code.
These stolen credentials are typically emailed to the phisher, and some are also saved to a text file on the phishing site. A few kits also transmit the stolen credentials to a remote website, also known as a “drop site”.
The victim’s sort code or card number is often used to automatically determine which bank the victim uses. The name and logo of the identified bank are displayed, along with a form whose fields depend on the chosen bank. For example, if the victim is a customer of Metro Bank, the form will request their Customer Number or Username, Password, and Security Number.
After this additional information has been emailed and logged, the victim is informed that their parcel redelivery has been scheduled successfully, but in reality the only delivery the victim is likely to receive is the bad news of their accounts being compromised.
Increased effectiveness
These attacks can be surprisingly effective, as when a consumer makes an online purchase, it is not always apparent who will be responsible for delivering it. This can also be true when placing repeat orders with the same company – for example, Amazon UK uses several different delivery companies but does not let the customer choose which one they want to use, nor does it indicate at the time of purchase which one will be used.
Hence when the customer receives an unsolicited text message regarding a parcel that could not be delivered, any victim who has recently placed an order online could easily regard it as an expected text message and fall for the attack regardless of which parcel company the phishing site impersonates.
In fact, such is the popularity of Amazon at the moment, some parcel delivery phishing sites count on the victim having bought something from Amazon recently. This is likely to increase the success rate of attacks against victims who are indeed regular Amazon shoppers.

This Hermes phishing site explicitly refers to a parcel from Amazon and includes the Amazon logo.
The relatively small redelivery fee asked for by these attacks also serves to reduce suspicion, increasing the chances of being able to steal the victim’s payment card or bank account details. Automatically identifying the victim’s bank and impersonating it accordingly – without ever explicitly asking the victim which bank they use – also increases the likelihood of online banking credentials being snared.
Criminals picking new brands to impersonate
The number of parcel delivery scams shot up noticeably in the second half of last year and the volume remains very high today, but behind the scenes the cybercriminals have been continually evolving their tactics and picking brands that are easier to target.
Royal Mail first saw a small spate of attacks in July 2020, and this was followed by a much larger spike in phishing attacks that impersonated DPD at the end of the year. By February 2021, Royal Mail had become the most impersonated brand again, but this rapidly declined as criminals instead switched to impersonating the courier company Hermes.
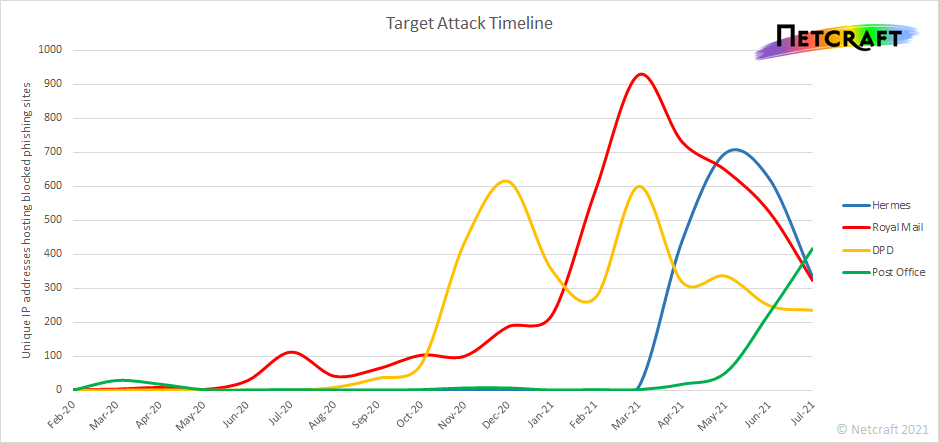
The rise and fall of parcel delivery scams. Attacks against DPD have persisted throughout the year, while the Post Office has quickly become the latest big target.
Just a few months later, Hermes attacks started to decline as criminals adapted their behaviour and instead launched increasing waves of phishing attacks that impersonated the Post Office. This has since become the most impersonated brand, suggesting that the Post Office is now the new easy target.
The Post Office does not deliver parcels, but does provide postal services on behalf of Royal Mail and Parcelforce. These services are usually for sending post and parcels, but parcels that cannot be delivered to a consumer may be left at a nearby Post Office for collection, and this makes the impersonation of the Post Office a viable alternative to impersonating Royal Mail.
Additionally, many consumers still believe Royal Mail and the Post Office are essentially the same company, despite the two organisations being independent of each other since 2012, so existing phishing kits that impersonate Royal Mail can be trivially modified to impersonate the Post Office.
Consumers can protect themselves from these types of phishing attacks by installing Netcraft’s mobile apps, and brand owners can use Netcraft’s malicious site takedown and countermeasures service to close down the phishing sites.