Phishing Sites Now Able To Detect Virtual Machines
Cybersecurity firms are usually using headless devices or virtual machines to determine if a website is used for phishing. In order to bypass detection, a phishing kit will make use of JavaScript to check whether a browser is running under a virtual machine or without an attached monitor, if the kit discovers any signs of analysis attempts, it will show a blank page instead of displaying the phishing page.
MalwareHunterTeam has discovered the script that checks the visitor’s screen’s width and height and uses the WebGL API to query the rendering engine used by the browser.
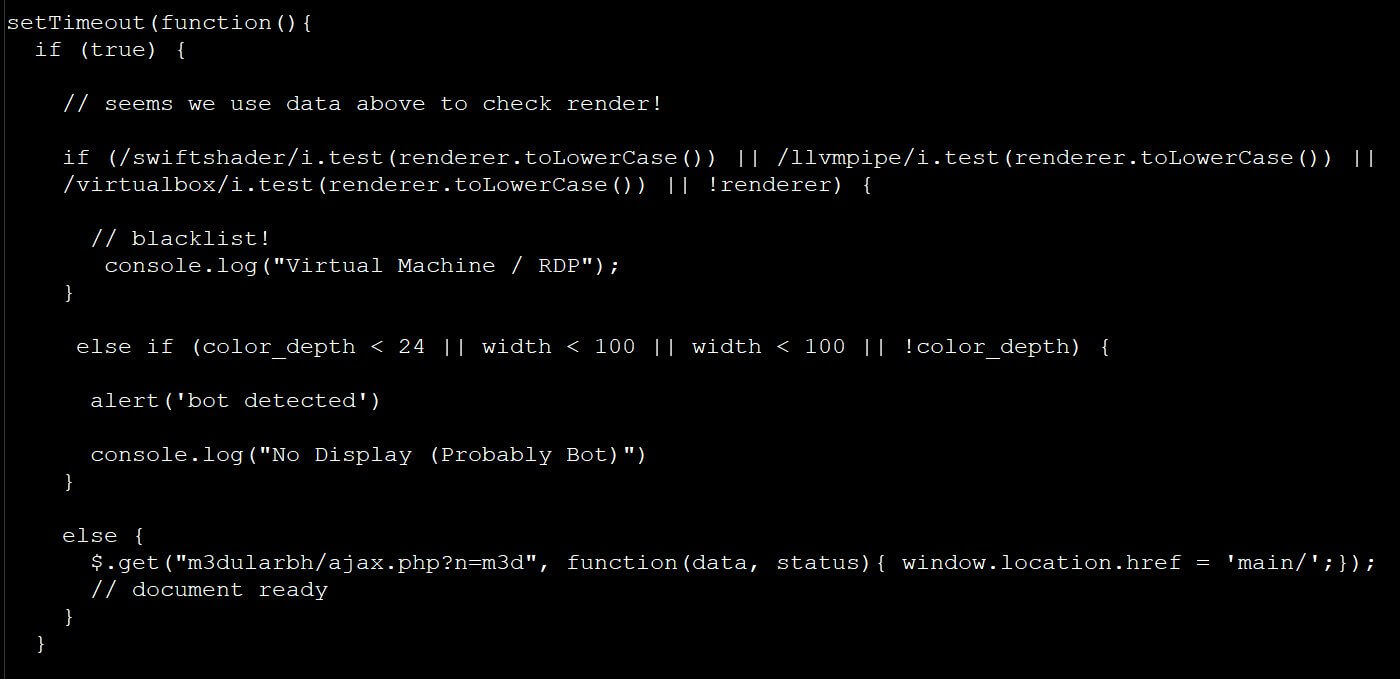
The script will be able to see first if the browser uses a software renderer, such as SwiftShader, LLVMpipe, or VirtualBox, if any software renderers are in place that is an indication the browser is running within a virtual machine, the script is also checking the visitor’s screen color depth, and if that is any less than 24-bits or if the screen height and width are less than 100 pixels.
If the script is detecting any of these conditions, the phishing page will display a message in the browser’s developer console whilst showing an empty page to the visitor.
Interestingly enough, if the browser is using a regular hardware rendering engine and a standard screen size, the script will display the phishing landing page.
It looks like an article from 2019 describing how JavaScript can be used to detect virtual machines, was the starting point in creating this script.
Your perimeter network is vulnerable to sophisticated attacks.
Heimdal™ Threat Prevention
– Network
Is the next-generation network protection and response
solution that will keep your systems safe.
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Fabian Wosar, the CTO of a known cybersecurity firm said that security software utilizes a variety of methods to scan for and detect phishing sites, including signature matching and visual machine using machine learning.
Code like the one above actually will work for some of these techniques. However, it is also trivial to prevent by just hooking a couple of JavaScript APIs and providing “fake” information.
It’s a daily task for researchers and security companies to harden their virtual machines to evade detection by malware and from now it seems that they will also have to better prepare them against phishing attacks.