Patching ProxyShell Flaws in Exchange Servers Is Urgent
Fraud Management & Cybercrime
,
Governance & Risk Management
,
Patch Management
Researchers Find Ransomware Gangs Now Exploiting the Vulnerabilities

The Cybersecurity and Infrastructure Security Agency is warning organizations to patch the ProxyShell vulnerabilities in Microsoft Exchange email servers because security researchers say ransomware gangs are exploiting these flaws.
See Also: Live Webinar | Password Management: Securing Hybrid Work for the Long Haul
Since April, security researchers have been warning about this new set of vulnerabilities in Exchange servers. Microsoft issued fixes and additional warnings about these flaws in May and July.
The warnings took on additional urgency over the weekend as researchers found an increase in activity by attackers looking to exploit the Exchange vulnerabilities. In a blog post published Saturday, Kevin Beaumont, head of the security operations center for London-based fashion retail giant Arcadia Group, noted that his honeypots had started to see increased activity from certain malicious IP addresses in recent days.
“These vulnerabilities are worse than ProxyLogon, the Exchange vulnerabilities revealed in March. They are more exploitable, and organizations largely haven’t patched,” Beaumont says.
Meanwhile, Symantec researchers warned in a report that a recently discovered ransomware gang called LockFile appears to have exploited the ProxyShell flaws to launch attacks.
To date, Symantec estimates that LockFile has targeted least 10 organizations in the U.S. and Asia, although it’s not clear if all of these incidents involved ProxyShell exploits.
Added Warnings
In its Saturday alert, CISA urged organizations to check for vulnerable versions of Exchange servers on their networks and to apply Microsoft’s patches for the ProxyShell flaws.
“CISA strongly urges organizations to identify vulnerable systems on their networks and immediately apply Microsoft’s Security Update from May 2021 – which remediates all three ProxyShell vulnerabilities – to protect against these attacks,” according to the alert.
Rob Joyce, the director of cybersecurity for the U.S. National Security Agency, took to Twitter to urge organizations to apply patches after Huntress Labs published a report that found more than 140 malicious web shells on more than 1,900 vulnerable Exchange servers. The researcher found that attackers were using the vulnerabilities to conduct ransomware attacks as well as plant cryptominers in vulnerable systems.
New surge in Microsoft Exchange server exploitation underway. You Must ensure you are patched and monitoring if you are hosting an instance. https://t.co/HzqlQxvSZC
— Rob Joyce (@NSA_CSDirector) August 21, 2021
ProxyShell
The ProxyShell vulnerabilities were discovered by Devcore security researcher Cheng-Da Tsai – also known as Orange Tsai – who demonstrated an exploit at the Pwn2Own contest in April. Earlier, Orange Tsai had uncovered the ProxyLogon and ProxyOracle flaws in Exchange servers.
The ProxyLogon vulnerabilities in Exchange prompted alerts in March and April from CISA. Those flaws affected on-premises versions of the email servers that are primarily used by smaller businesses and local government agencies. In July, the Biden administration attributed some of the initial attacks exploiting ProxyLogon to China’s Ministry of State Security, aka MSS (see: Can the US Curb China’s Cyber Ambitions?).
Family of Flaws
The ProxyShell flaws include:
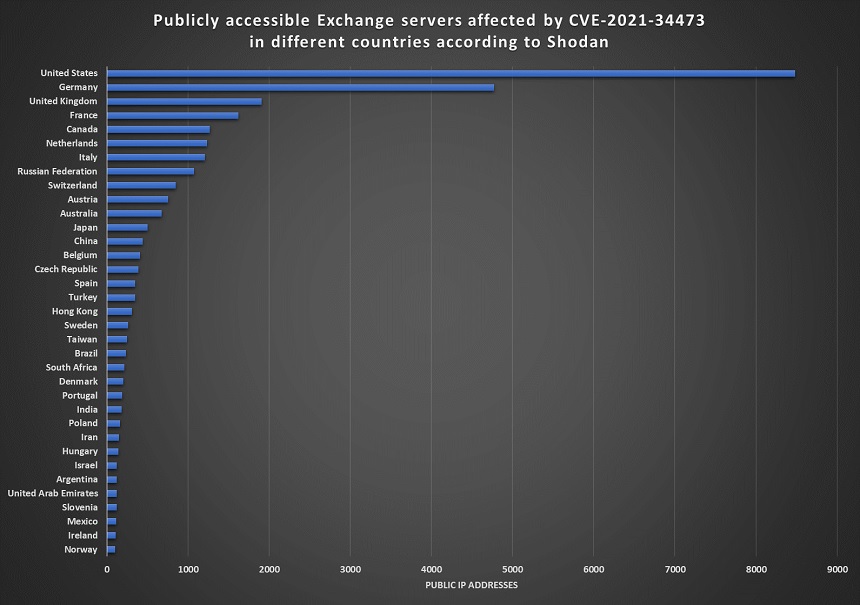
- CVE-2021-34473: This vulnerability can allow attackers to perform pre-authentication remote code execution within a vulnerable server;
- CVE-2021-34523: This vulnerability can give an attacker elevation of privileges within the Exchange PowerShell back end;
- CVE-2021-31207: This vulnerability can enable attackers to execute arbitrary file writes in post-authentication that can lead to the remote code execution.
This month, researchers began finding proof-of-concept exploit code in the wild for the ProxyShell vulnerabilities. Despite Microsoft’s issuance of patches in May, on Aug. 9, Jan Kopriva, a researcher with the SANS Institute, found more than 30,000 vulnerable Exchange servers during a worldwide internet scan of 100,000 systems that were still exposed to the ProxyShell flaws.
Yaniv Bar-Dayan, CEO and co-founder of security firm Vulcan Cyber, notes that besides patches, Microsoft is also offering mitigation tools that organizations can use if they are unable to apply the fixes right away.
“It’s important to remember that the mitigations suggested are not substitutes for installing the updates, and the patches should be deployed as soon as possible,” Bar-Dayan says. “A ransomware attack almost always takes advantage of known, yet unaddressed, security vulnerabilities.”
Ransomware
Over the weekend, researchers began to warn that ransomware gangs were now trying to use the ProxyShell vulnerabilities as a way to gain a foothold in vulnerable networks.
In the cases Symantec uncovered, the LockFile ransomware group appeared to have exploited ProxyShell flaws to gain access to victims’ networks. Later, the group deployed another attack method called PetitPotam, which allowed them to take over the Windows domain controller and use that access to deploy the ransomware code, Symantec says.
The researchers also found that the attackers behind the LockFile ransomware use a ransom note with a design similar to that used by the LockBit ransomware gang and also make reference to the Conti gang in the email address (see: Ransomware: LockBit 2.0 Borrows Ryuk and Egregor’s Tricks).
“LockFile appears to be a new threat on the already crowded ransomware landscape. The investigation into this threat, and whether it may have links to any previously seen or retired ransomware threats, continues,” the Symantec researchers note.