NSA Discovers New Vulnerabilities Affecting Microsoft Exchange Servers
In its April slate of patches, Microsoft rolled out fixes for a total of 114 security flaws, including an actively exploited zero-day and four remote code execution bugs in Exchange Server.
Of the 114 flaws, 19 are rated as Critical, 88 are rated Important, and one is rated Moderate in severity.
Chief among them is CVE-2021-28310, a privilege escalation vulnerability in Win32k that’s said to be under active exploitation, allowing attackers to elevate privileges by running malicious code on a target system.
Cybersecurity firm Kaspersky, which discovered and reported the flaw to Microsoft in February, linked the zero-day exploit to a threat actor named Bitter APT, which was found exploiting a similar flaw (CVE-2021-1732) in attacks late last year.
“It is an escalation of privilege (EoP) exploit that is likely used together with other browser exploits to escape sandboxes or get system privileges for further access,” Kaspersky researcher Boris Larin said.
NSA Found New Bugs Affecting Exchange Server
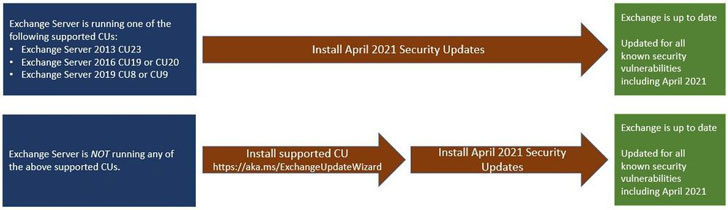
Also fixed by Microsoft are four remote code execution (RCE) flaws (CVE-2021-28480 through CVE-2021-28483) affecting on-premises Exchange Servers 2013, 2016, and 2019 that were reported to the company by the U.S. National Security Agency (NSA). Two of the code execution bugs are unauthenticated and require no user interaction, and carry a CVSS score of 9.8 out of a maximum of 10.
While the Windows maker said it had found no evidence of any active exploits in the wild, it’s recommended that customers install these updates as soon as possible to secure the environment, in light of the widespread Exchange Server hacks last month and new findings that attackers are attempting to leverage the ProxyLogon exploit to deploy malicious cryptominers onto Exchange Servers, with the payload being hosted on a compromised Exchange Server.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also revised the emergency directive it issued last month, stating “these vulnerabilities pose an unacceptable risk to the Federal enterprise and require an immediate and emergency action,” while cautioning that the underlying flaws can be weaponized by reverse-engineering the patch to create an exploit.
FBI Removed Backdoors From Hacked MS Exchange servers
What’s more, the U.S. Federal Bureau of Investigation (FBI) carried out a “successful action” to “copy and remove” web shells planted by adversaries on hundreds of victim computers using the ProxyLogon flaws. The FBI is said to have wiped the web shells that were installed by Hafnium that could have been used to maintain and escalate persistent, unauthorized access to U.S. networks.
“The FBI conducted the removal by issuing a command through the web shell to the server, which was designed to cause the server to delete only the web shell (identified by its unique file path),” the Justice Department said in a statement detailing the court-authorized operation.
27 RCE Flaws in Windows RPC and Other Fixes
Microsoft also said four additional vulnerabilities were publicly known at the time of release but not exploited —
- CVE-2021-28458 – Azure ms-rest-nodeauth Library Elevation of Privilege Vulnerability
- CVE-2021-27091 – RPC Endpoint Mapper Service Elevation of Privilege Vulnerability
- CVE-2021-28437 – Windows Installer Information Disclosure Vulnerability
- CVE-2021-28312 – Windows NTFS Denial of Service Vulnerability
In addition, April’s Patch Tuesday update also addresses a whopping 27 RCE flaws in Remote Procedure Call (RPC) runtime, a Hyper-V security feature bypass vulnerability (CVE-2021-28444), and multiple privilege escalation flaws in Windows Speech Runtime, Windows Services and Controller App, Windows Secure Kernel Mode, Windows Event Tracing, and Windows Installer.
Software Patches From Other Vendors
Besides Microsoft, a number of other vendors have also released a slew of patches on Tuesday —