FireEye, CISA Warn of Critical IoT Device Vulnerability
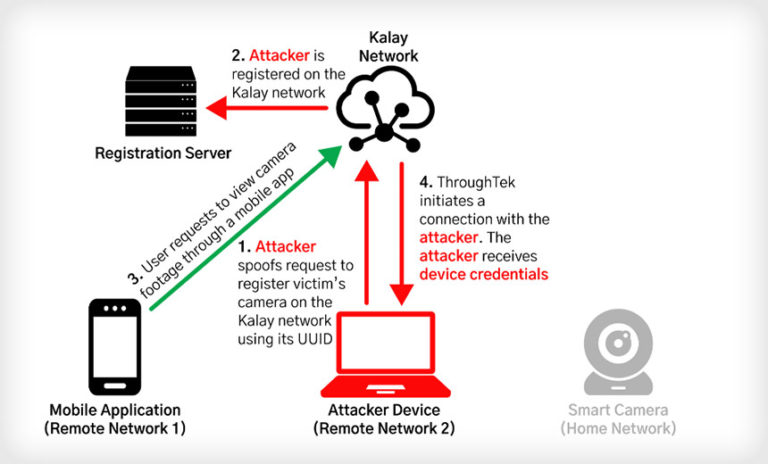
Endpoint Security , Internet of Things Security Researchers: Kalay Protocol Flaw Could Affect Millions of Connected Devices Scott Ferguson (Ferguson_Writes) • August 17, 2021 Example of how an attacker could exploit a vulnerability in ThroughTek’s Kalay protocol (Source: FireEye) FireEye researchers and the U.S. Cybersecurity and Infrastructure Security Agency are warning about a…