New malware “BlackRock” disguised as Android Clubhouse app
The malware can also intercept text messages regardless of the fact that SMS-based two-factor authentication may be in use.
A Trojan malware dubbed “BlackRock” is disguising as an Android version of the invite-only audio chat app called Clubhouse. It is worth noting that the app has no Android version at this moment.
The cybersecurity researchers at ESET have revealed that the malware was created for the purpose of stealing the victims’ login information for a total of 458 online services.
The list of targeted apps includes all sorts of financial and shopping apps, cryptocurrency exchanges as well as social media and messaging platforms such as:
- Amazon
- Netflix
- Outlook
- eBay
- Coinbase
- Plus500
- Cash App
- BBVA
- Lloyds Bank
BlackRock uses an overlay attack that allows it to steal victims’ credentials whenever one of the targeted apps is launched. Following the overlay, the user is asked to enter their login information which is a neat trick of letting the attackers gain access to their credentials.
SEE: Fake Cyberpunk 2077 Android App Delivering Ransomware
The main concern over here is the fact that the malware can also intercept text messages regardless of the fact that SMS-based two-factor authentication may be in use.
Lastly, the malicious app also requests the victim to enable accessibility services which would give the cyber-criminals direct control of the device.
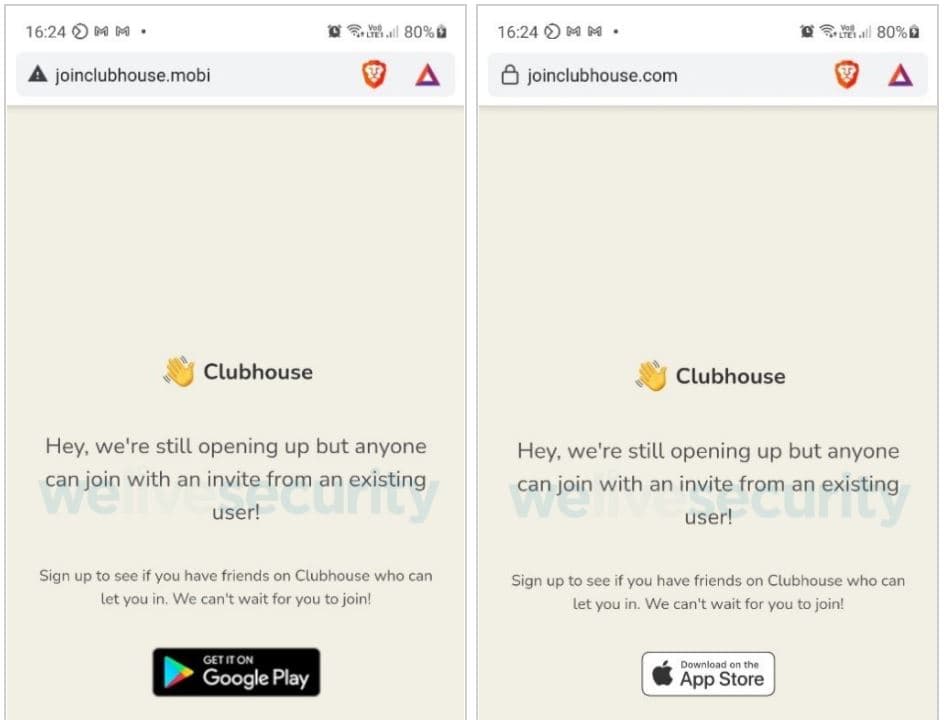
As stated by ESET’s Lukas Stefanko, the website looks as real as it gets. It is “a well-executed copy of the legitimate Clubhouse website” but there are a few differences. If a user downloads an app from a legitimate website, it would always redirect the user to Google Play instead of directly downloading an Android Package Kit. The fake version obviously automatically downloads the app on the user’s device as soon as the user clicks on ‘Get it on Google Play.’
Another key difference to note is that when using fake websites, there are signs that the connection is not secure (HTTP instead of HTTPS) or that the site is using the “.mobi” top-level domain (TLD) instead of “.com” that is used by legitimate websites.
However, the biggest red flag is probably the fact that even though Clubhouse is indeed planning to launch the Android version of its app, the platform is only available for iOS users currently.
In order to avoid becoming victims of such attacks by Trojan malware, there are a few mobile security practices that users can follow. They should only use official stores to download apps to their devices and once downloaded, they should be wary of what kinds of permissions they are granting to the applications.
SEE: Fake Coronavirus apps hit Android & iOS users with spyware, adware
Moreover, they should keep their device up-to-date by setting it to patch and update automatically. If possible, they should use software-based or hardware token one-time password (OTP) generators instead of SMS.
Lastly, they should always do some research on the developer and the app’s ratings and user reviews before installing an application.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.