Millions of Dell Devices Vulnerable to Update Driver Flaw
Endpoint Security
,
Governance & Risk Management
,
Patch Management
Dell Has Patched Driver Issue Found by SentinelOne

Dell has patched five flaws in a vulnerable firmware update driver that has shipped in millions of laptops, tablets and desktops since 2009.
See Also: Live Webinar | Software Security: Prescriptive vs. Descriptive
The vulnerabilities have been assigned a single CVE, CVE-2021-21551, and they have a CVSS score of 8.8. Dell has wrapped the vulnerable driver, which is dbutil_2_3.sys, in BIOS update utility, writes Kasif Dekel, a senior security researcher at SentinelOne.
“These multiple high-severity vulnerabilities in Dell software could allow attackers to escalate privileges from a non-administrator user to kernel mode privileges,” Dekel writes in a blog post. “While we haven’t seen any indicators that these vulnerabilities have been exploited in the wild up till now, with hundreds of millions of enterprises and users currently vulnerable, it is inevitable that attackers will seek out those that do not take the appropriate action.”
The vulnerabilities are not remotely exploitable, however, and exploiting them requires local authenticated access, according to Dell’s advisory.
“A malicious actor would first need to be granted access to your PC, for example through phishing, malware or by you granting remote access. To help protect yourself from malicious actors, never agree to give remote control to your computer to any unsolicited contact (such as from an email or phone call) to fix an issue.” Dell says. “Dell is not aware of this vulnerability having been exploited by a malicious actor to date.”
Proof of Concept Held Back
Dekel writes that he’s not releasing the proof-of-concept code for his attack until June 1 to give enough lead time for systems to be patched. But he did publish a brief demo video.
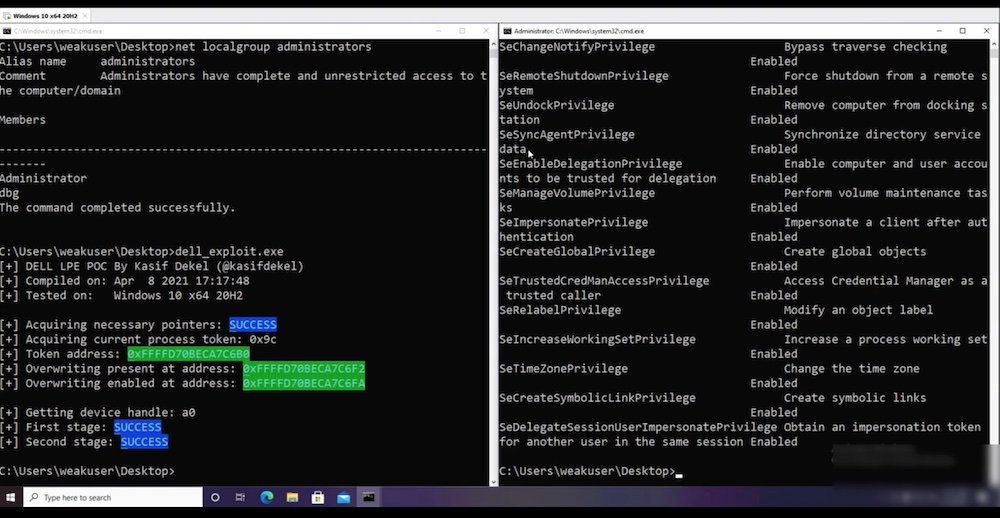
One problem with the firmware update driver is that it can be accessed by nonprivileged users, and it accepts Input/Output Control (IOCTL) requests without any ACL requirements, Dekel writes.
“Allowing any process to communicate with your driver is often a bad practice since drivers operate with the highest of privileges,” Dekel adds.
Another issue is that the driver file is located in “C:WindowsTemp, which is also a bug itself and opens the door to other issues,” Dekel writes. “The classic way to exploit this would be to transform any BYOVD (Bring Your Own Vulnerable Driver) into an elevation of privileges vulnerability, since loading a (vulnerable) driver means you require administrator privileges, which essentially eliminates the need for a vulnerability. “Thus, using this side noted vulnerability virtually means you can take any BYOVD to an elevation of privileges.”
Although Dell has released a fixed driver, Dekel writes that the signing certificate has not been revoked. “This is not considered best practice, since the vulnerable driver can still be used in a BYOVD attack as mentioned earlier,” he notes.
Although the flaws are not remotely exploitable, Dekel writes that they’re certainly still useful to attackers for achieving lateral movement.
“An attacker with access to an organization’s network may also gain access to execute code on unpatched Dell systems and use this vulnerability to gain local elevation of privilege,” Dekel writes. “Attackers can then leverage other techniques to pivot to the broader network, like lateral movement.”