Microsoft issues emergency patch to address PrintNightmare
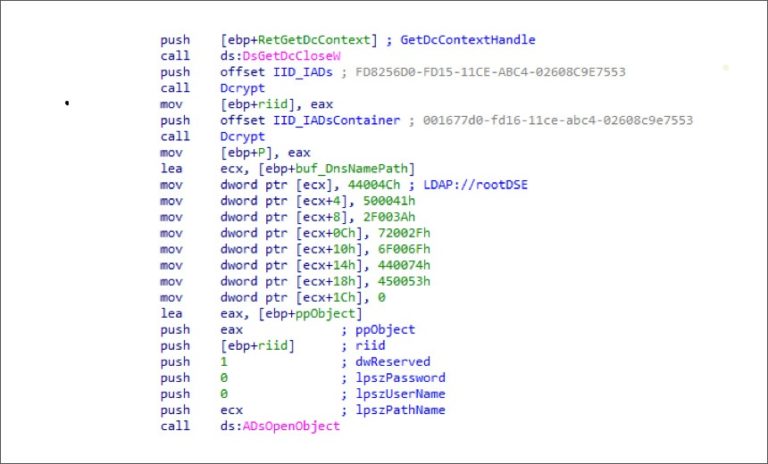
Last week a vulnerability made its way to the internet after researchers accidentally published a proof of concept. That proof of concept exploited a series of vulnerabilities in the Windows Print Spooler service.
The vulnerability was dubbed PrintNightmare and until now the best way to avoid it was to disable the Print Spooler service which isn’t really a solution for folks who need to print.
“A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” explains Microsoft.
For once, we agree with the name given to a vulnerability because this truly sounds like a nightmare.
Thankfully, Microsoft has issued an out-of-band update to address the vulnerability.
KB5005010 is now available to download and install and Microsoft recommends installing it as soon as possible.
“We recommend that you urgently install the July 2021 Out-of-band updates on all supported Windows client and server operating systems, starting with devices that currently host the print spooler service. In addition, optionally configure the RestrictDriverInstallationToAdministrators registry value to prevent non-administrators from installing printer drivers on a print server,” writes Microsoft.
The firm explains in detail how to configure RestrictDriverInstallationToAdministrators registry values here.
If you are able to install this update, we highly recommend you do. Just maybe don’t use it as an excuse to miss a meeting.
[Image – CC 0 Pixabay]