LockFile Ransomware Using New Techniques to Evade Detection
Fraud Management & Cybercrime
,
Next-Generation Technologies & Secure Development
,
Ransomware
Sophos: Methods Include ‘Intermittent Encryption’
The operators of LockFile ransomware have adopted new techniques, including “intermittent encryption,” to help evade detection, according to cybersecurity firm Sophos.
See Also: Threat Briefing: Ransomware
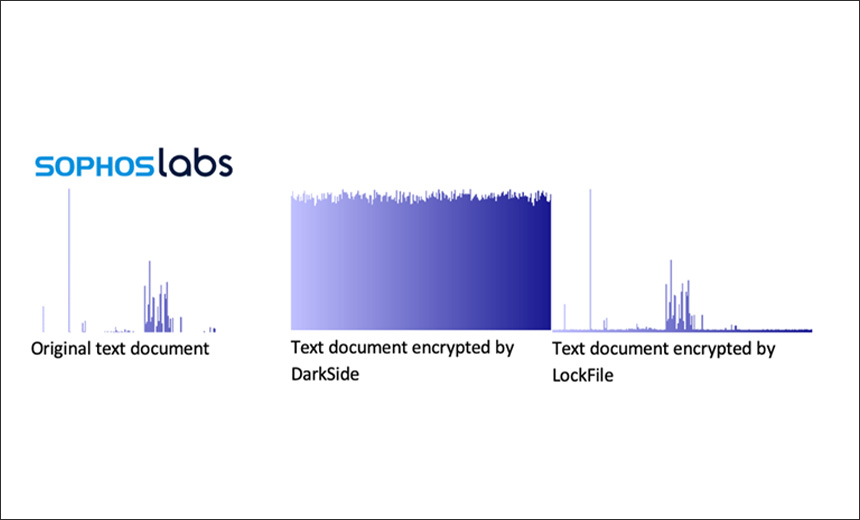
For example, the ransomware gang is only partially encrypting documents. Partial encryption is generally used by ransomware operators to speed up the encryption process; this technique has previously been implemented by BlackMatter, DarkSide and LockBit 2.0, says Mark Loman, director of engineering at Sophos and the author of the research report.
“What sets LockFile apart is that, unlike the others, it doesn’t encrypt the first few blocks. Instead, LockFile encrypts every other 16 bytes of a document. This means that a file such as a text document remains partially readable and looks statistically like the original,” Loman says.
The technique, dubbed “intermittent encryption,” apparently hasn’t been used in other ransomware attacks, Sophos reports.
This approach can prove effective in evading detection by software that relies on inspecting content using statistical analysis to detect encryption, the researchers say.
Sophos detected the new technique while analyzing a file on VirusTotal. VirusTotal allows users to analyze suspicious files and URLs to detect malware and share it with the security community.
LockFile was first detected in April, when it exploited ProxyShell vulnerabilities in on-premises Microsoft Exchange servers, reported researchers from Trend Micro. It also deployed a PetitPotam NTLM relay attack to seize control of the domain.
Other New Evasion Techniques
The LockFile ransomware also uses a relatively uncommon process known as “memory mapped input/output” to encrypt a file, the Sophos report points out.
“This technique allows the ransomware to invisibly encrypt documents that are cached in the computer’s memory without creating additional input/output telematic traffic that detection technologies will spot,” the report says.
This technique has previously been used by WastedLocker and Maze ransomware.
LockFile also doesn’t need to connect to a command-and-control center to communicate, which reduces traffic and helps keep the attack activity under the detection radar, the Sophos report states.
“Once the ransomware has encrypted all the documents on the machine, it deletes itself. This means that, after the attack, there is no ransomware binary for incident responders or endpoint protection software to find or clean up,” according to the report.
LockFile also avoids encrypting some 800 different filetypes by extension, further confusing certain anti-ransomware protections, the report adds.
Mitigation
To help mitigate risks, Sophos recommends separating critical servers from each other and from workstations by putting them into separate VLANs, regularly auditing Active Directory to ensure that no one have more access than is needed for their purpose, and double-checking that the patches applied have been installed correctly and are in place for critical systems such as internet-facing machines or domain controllers.
Although previous malware attacks have used some of the techniques that the gang behind LockFile is now using, it’s unusual to see all these techniques implemented in the same ransomware campaign, says Sean Nikkel, senior cyberthreat intel analyst at cybersecurity firm Digital Shadows.
“It puts the onus on defenders to also investigate more system processes that are performing this kind of behavior, which potentially means an increase in false positives and time to investigate,” he says.
Attackers can use any additional time before detection to increase their chances of success, Nikkel says.
“Some malware may only need seconds to minutes to be successful, but quieter attacks like [LockFile] may increase potential dwell time for an attacker to be in a network,” he says. “This, in turn, may allow more time to reconnoiter the network and attack more critical data.”
Oliver Tavakoli, CTO of cybersecurity company Vectra AI, says the encryption phase of a ransomware attack is often very quick, taking anywhere from a few minutes to a few hours.
Most attacks, Tavakoli says, get all the pieces in place before beginning simultaneous encryption of files from all the commandeered machines.
“Many of the elements of ransomware attacks are detectable well before the encryption phase – or the exfiltration phase, which precedes encryption – kicks into action,” he says.
That’s why organizations should build endpoint and network detection and response capabilities with a focus on reconnaissance, lateral movement and command-and-control activity, he adds.