LockBit 2.0 Ransomware Rep ‘Tells All’
Business Continuity Management / Disaster Recovery
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Attacker Extols the Malware While Also Advising Would-Be Victims on Optimal Defenses

Want to take information security defense advice from a ransomware-wielding attacker?
See Also: New Priorities for IT Operations: Be Ready for Whatever Comes Next
Here goes: “Employ a full-time red team, regularly update all software, perform preventive talks with a company’s employees to thwart social engineering and … use the best ransomware-fighting antivirus.”
So says “LockBitSupp,” a representative of the LockBit 2.0 ransomware group, in a Russian-language interview with the Russian OSINT YouTube channel posted Monday, and translated into English by Israeli threat intelligence firm Kela. The BlackBerry Research & Intelligence Team says that whoever is behind the LockBitSupp handle claims to be based in China and is active on the Russian-language XSS cybercrime forum.
Ransomware-as-a-service operators as well as their affiliates – referring to the independent contractors who take the ransomware code, infect victims and share the profits with the operators – don’t seem to shy away from delivering tell-all interviews (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
Obviously, anything these criminals claim in the course of the interviews should be taken with a large dose of salt. For example, when researchers at Cisco Talos previously interviewed a LockBit individual they’ve called “Aleks,” he portrayed himself as a good guy, operating with a strict moral code, including never targeting healthcare entities (see: Secrets and Lies: The Games Ransomware Attackers Play).
“Now, the reality was, we knew the entire time that he was targeting healthcare,” Craig Williams, director of outreach at Cisco Talos, has told me. “But it was really interesting to see that he wanted to convey this almost Robin Hood-type view of himself – that he was really a good guy that was misunderstood and that had to struggle in life and feed his family.”
Moral Codes Abound
LockBitSupp, who’s a spokesman for LockBit 2.0 and is perhaps one of its core operators, also claims to have a moral code. “We do not attack healthcare, education, charitable organizations, social services – everything that contributes to the development of personality and sensible values from the ‘survival of the species’ perspective,” he tells Russian OSINT. “Healthcare, medicine, education, charitable organizations and social services remain intact.”
Of course they do. Unfortunately, as the hit by the Conti group on Ireland’s health service has demonstrated, ransomware-wielding attackers tend to hit whoever they can. If this sparks some type of outcry, then they may give the victim a “free decryptor.” But restoring systems, even with a decryptor or via backups, can be a time- and labor-intensive process. In Ireland’s case, for example, the attack disrupted healthcare operations across the country for many weeks.
Interview: 9 Takeaways
With those caveats in mind, what does LockBitSupp have to say about the state of ransomware attacks, as well as the new LockBit 2.0 operation?
Beyond the defensive advice noted above – including the benefits of employing in-house red teams, aka offensive security engineers – here are top takeaways from the interview:
- Why the U.S. and EU remain top targets: “The largest number of the world’s wealthiest companies is concentrated there,” the representative says, adding that those regions also have “more developed” cyber insurance.
- The pandemic has been a boon: “Many employees started working remotely from personal computers, which are easier to infect with a virus and steal account information used to access the companies,” LockBitSupp says.
- Why victims choose to pay a ransom: He says “potential loss” appears to be the overriding calculation for victims as they weigh potential risks and benefits from paying a ransom. “However, sometimes you stumble on guys with principles.”
- Expect more supply chain attacks: Asked about REvil’s massive ransomware attack, which used Kaseya’s remote management software to hit about 1,500 organizations, the LockBit 2.0 representative says REvil likely had an affiliate who specialized in such attacks, and that supply chain attacks remain an obvious target. “Such attacks for sure will be carried out in the future since there is no flawless software,” he says. “Vulnerabilities are endless and everywhere.”
- Victims without backups are more likely to pay: It might sound obvious, but another major factor in whether an organization pays a ransom is whether it has working backups. “The victims who are paying are the ones who do not make backups and poorly protect sensitive information, regardless of the industry,” LockBitSupp says.
- Ransomware “bans” haven’t disrupted established operations: After the White House announced a ransomware crackdown earlier this year, some cybercrime forums claimed to be banning all ransomware discussions, although enforcement appears to have been scattershot. Regardless, LockBitSupp says the impact on LockBit 2.0’s operations was minimal, because the group is already an established operator. “For new affiliate programs, it will be harder to announce themselves and earn a reputation during the information blockade,” he says. “So, this taboo on forums did us a favor. … It is easy to open an affiliate program but it is an art to keep it open.”
- Multiple cryptocurrencies are accepted: The representative says that unlike how Avaddon, DarkSide or REvil operated, LockBit 2.0 leaves it to affiliates to communicate directly with victims whose systems they’ve encrypted, as well as to choose what cryptocurrency to accept for payments, including bitcoin, monero or even dogecoin. “Payments are carried out exclusively to our clients’ wallets, and then they transfer to us 20% of the ransom,” he says.
- Criminals prefer public silence: Ransomware-wielding attackers have historically preferred victims to pay a ransom without telling anyone, because it makes tracking such attacks more difficult for law enforcement agencies – and LockBit 2.0 is no different. “A lot of noise around the attack is bad,” the representative says. “A silent attack no one knew about is good for the company’s reputation, and our income.”
- Attacks are now more automated: One of LockBit’s selling points has been the speed and reliability of its crypto-locking code, and LockBitSupp says development of LockBit 2.0 has focused on reliably encrypting as many files as possible in the shortest amount of time. “The faster the attack is carried out, the less the risk that the attack will be repelled,” he says. As security firm Trend Micro recently described, LockBit 2.0 has provided more automated ways for affiliates to access a victim’s network, and it also provides affiliates with a Trojan called StealBit to automatically steal data. The representative says this eliminates the need for affiliates to manage servers or cloud services and instead routes stolen data directly to LockBit 2.0’s blog and automatically indexes them.
Relentless Self-Promotion Continues
LockBit affiliates such as Aleks have said they work with the operation because they get a good share of profits whenever a victim pays and also because of the quality of the ransomware executable. Poorly written software can shred files when forcibly encrypting them before deleting the original. This makes recovering those files impossible, unless they can be restored from backups – and that makes victims less interested in paying.
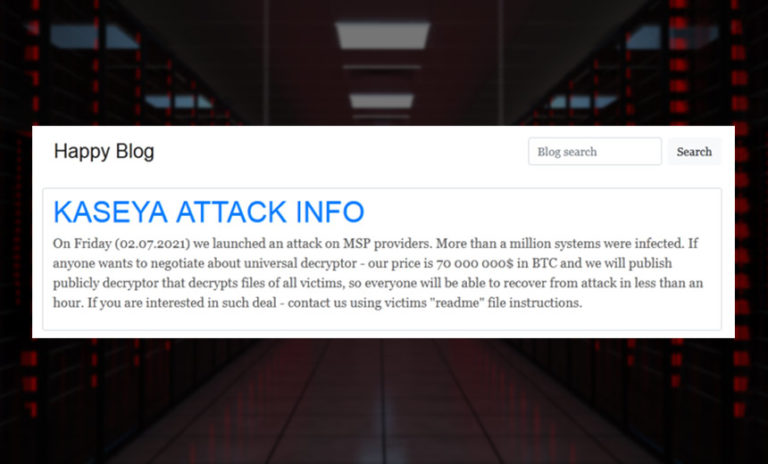
LockBit, however, had a reputation for not only rapidly encrypting files, but also doing so in a reliable manner, and the LockBit 2.0 representative says the focus on writing clean code continues. “Few can write the fastest encryption algorithm in the world; the software always requires support and innovation, so technical savviness is extremely important,” he says.
One crucial point to remember whenever a ransomware-as-a-service operator grants an interview is that they’re always on the lookout for new affiliates. Such interviews give them free advertising, and LockBitSupp doesn’t shy away from selling his product.
“We are in the first place in terms of the encryption speed and the speed of dumping the company data,” he claims. “The distribution and encryption processes are automated,” and after a malware payload executes and hits the domain controller, “after the shortest period of time, the entire corporate network is encrypted.”
Because operators get a cut of every ransom paid, successful operations have been raking in the profits, helped by tactics such as so-called double extortion, which includes shaking down victims to get them to pay for a decryptor as well as promising to delete stolen data.
The LockBit 2.0 representative, however, declines to name a dollar figure for what he’s earned in recent years. “Enough for a comfortable life,” he says. “Money loves silence.”
Apparently, even tell-all interviewees have their limits.