Leak of 50,000 Contact Details Tied to Spyware Targeting
Cyberwarfare / Nation-State Attacks
,
Endpoint Security
,
Fraud Management & Cybercrime
‘Pegasus Project’ Says List Used to Coordinate Attacks Using NSO Group’s Spyware
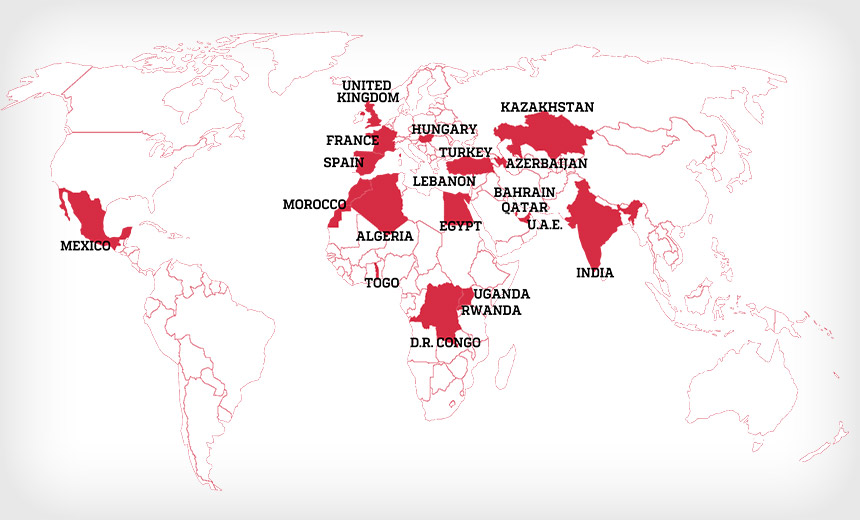
A leak of 50,000 telephone numbers and email addresses led to the “Pegasus Project,” a global media consortium’s research effort that discovered how Pegasus spyware developed by NSO Group is being used in the wild.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
The list of contact details was obtained by French nonprofit journalism group Forbidden Stories and human rights group Amnesty International. They say it appears to have been used to identify individuals of interest across 50 countries – including 1,000 individuals in Europe – who were to be potentially targeted with Pegasus spyware.
Investigating who is on the targeting list – and whether they were targeted – is the raison d’être of the Pegasus Project consortium of 17 media organizations, which have been engaged in months of research and on Sunday began to publish their findings. Amnesty International has not said how it came to be in possession of the apparent targeting list.
Pegasus is a remote-access tool built to infect both Android and Apple devices, sometimes via zero-day exploits in ether platform. Developed and sold by Israeli software developer NSO Group, the Pegasus spyware – like rival Candiru, developed by an Israeli firm of the same name – can only be exported to countries after approval from Israel’s defense ministry.
Forbidden Stories says that connecting the names on the list of leaked data with subsequent Pegasus infections can only be done after conducting a digital forensic analysis on an individual’s smartphone. When Amnesty International’s technical team performed digital forensic analysis on 67 smartphones, it found that more than half of them appeared to have been infected by Pegasus, some as recently as this month, via a “zero click” vulnerability in Apple’s iOS mobile operating system (see: Spyware Exposé Highlights Suspected Apple Zero-Day Flaws).
Spyware built by NSO Group has previously made use of zero-day flaws in Apple and Android mobile operating systems to help infect targets’ devices with the software, for example, via apps such as WhatsApp and iMessage. Once on the device, the spyware has access to all functionality, including the ability to use the microphone, camera and GPS to track and watch targets in real time. All information stored on a device, including photographs and contacts, can also be exfiltrated.
Experts say Pegasus seems to be used in only highly targeted attacks. For targets, however, that doesn’t lessen the risk they might face. “The minimal spread of the spyware doesn’t make it less dangerous, for each individual being under surveillance the scope of privacy damage is certainly very high,” says Jakub Vavra, a mobile threat analyst at security software vendor Avast, which develops antivirus tools.
The Power of Spyware
Such spyware gets pitched to regulators, lawmakers and officials as being necessary for combating criminals, such as drug dealers, illicit hackers, child sexual abusers and terrorists. Firms such as NSO Group also say they require customers to agree to terms and conditions that restrict how software gets used to only combating “serious crime and terrorism.”
But research by Amnesty International as well as the University of Toronto’s Citizen Lab, which tracks illegal hacking and surveillance, suggests that while many governments use the software for its stated purpose, some also appear to be also using it to target other individuals, including business executives, journalists, activists and human rights advocates.
These long-standing allegations have been levied against firms, including NSO Group, that sell spyware to intelligence agencies. But NSO Group has continued to vigorously deny that its software is being misused.
On Monday, NSO Group released a statement in response to the Forbidden Stories research. “After checking their claims, we firmly deny the false allegations made in their report,” it says.
Many governments, meanwhile, seem reluctant to overtly curtail the use of such software. Two years ago, then UN special rapporteur on freedom of opinion and expression, David Kaye, called for a moratorium on exporting such software until better controls could be put in place.
“The private surveillance industry is a free-for-all,” that had led to the distribution “of technology that is causing immediate and regular harm to individuals and organizations that are essential to democratic life – journalists, activists, opposition figures, lawyers and others,” Kaye said. “It is time for governments and companies to recognize their responsibilities and impose rigorous requirements on this industry, with the goal of protecting human rights for all.”
But no international standards or controls have come to pass. The EU, however, has been moving to institute export-control rules on such technology.
Politicians, Journalists, Activists Included in List
The leaked list of contact details obtained by Forbidden Stories and Amnesty International includes details on numerous activists, government critics, politicians, business leaders as well as 180 journalists from nearly two dozen countries.
According to the media consortium behind the Pegasus Project, analyzing the data suggests that at least 10 governments appear to have submitted names to the list: Azerbaijan, Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, and the United Arab Emirates.
The Guardian says that some individuals’ smartphones are known to have been infected with Pegasus just seconds after being added to the leaked list.
Journalists on the list include the editor of Britain’s Financial Times, as well as individuals working for Agence France-Presse, Al Jazeera, Associated Press, CNN, the Economist, Le Monde, the New York Times, Reuters, the Wall Street Journal and Voice of America, the Guardian reports.
Other individuals featured on the list include India Prime Minister Narendra Modi’s chief rival, Rahul Gandhi; Mexican journalist Cecilio Pineda Birto – murdered just one month after his phone number appeared on the list; as well as business leaders, lawyers, academics and government officials, including cabinet officials and heads of state, which the Pegasus Project partners say they plan to name in coming days.
In its statement, NSO Group says that it had nothing to do with the alleged target-selection list, and it says the list of 50,000 telephone numbers and email addresses appears to have been obtained from legitimate lookup services, such as HRL Lookup.
“Such services are openly available to anyone, anywhere, and anytime, and are commonly used by governmental agencies for numerous purposes, as well as by private companies worldwide,” NSO Group says.
The company tells the Guardian: “It is also beyond dispute that the data has many legitimate and entirely proper uses having nothing to do with surveillance or with NSO, so there can be no factual basis to suggest that a use of the data somehow equates to surveillance.”
Terms and Conditions
NSO Group’s most recent “transparency and responsibility report,” released in June, says the company has 60 customers across 40 countries. An unnamed source told the Guardian that NSO has about 45 Pegasus customers, with each targeting, on average, about 112 devices per year.
How many of the individuals named in the list of leaked contact details might have been targeted using Pegasus remains an open Pegasus Project question. But Amnesty International’s tests on a small number of devices owned by individuals named on the list found that just over half had been infected. Amnesty International’s technical findings were independently confirmed by Citizen Lab.
NSO Group says it does not have insights into how “vetted government customers” use its technology. “NSO does not operate the systems that it sells to vetted government customers, and does not have access to the data of its customers’ targets. NSO does not operate its technology, does not collect, nor possesses, nor has any access to any kind of data of its customers,” it tells the Guardian.
The company tells Forbidden Stories that it investigates all reports of its software being misused and has previously revoked certain clients’ ability to use the software. Evidence that such actions have been taken, however, appear caught in a catch-22 scenario. “Due to contractual and national security considerations, NSO cannot confirm or deny the identity of our government customers, as well as identity of customers of which we have shut down systems,” the company says.
In the wake of the Pegasus Project findings, Amnesty International has called on NSO Group to crack down on governments using Pegasus in a manner that violates human rights.
“NSO Group must carry out adequate human rights due diligence and take steps to ensure that human rights defenders and journalists do not continue to become targets of unlawful surveillance,” Amnesty International says.






