Lazarus Group Targets Freight Logistics Firm
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
,
Governance & Risk Management
ESET Report Ties ‘Vyveva’ Backdoor to North Korean APT Group
The Lazarus Group, a North Korean-linked advanced persistent threat group also known as Hidden Cobra or Zinc, has recently deployed a previously undocumented backdoor called “Vyveva” to target a freight logistics firm based in South Africa, according to the security firm ESET.
See Also: Webinar | Attacks on Cloud Infrastructure
Vyveva, which has multiple components, communicates with its command-and-control server through the anonymous Tor network, ESET notes. The backdoor was first spotted in the wild in June 2020, when it was used against two devices belonging to the same freight logistics firm. The researchers, however, believe the malware may have been in active use since 2018.
ESET says it’s likely that the backdoor has been used to target other organizations throughout the globe.
“Vyveva constitutes yet another addition to Lazarus’s extensive malware arsenal,” says Filip Jurčacko, an ESET researcher. “Attacking a company in South Africa also illustrates the broad geographical targeting of this APT group.”
ESET says the initial attack vector Lazarus uses to target victims and plant the Vyveva backdoor is not known. But the researchers believe the malware is likely used for cyberespionage.
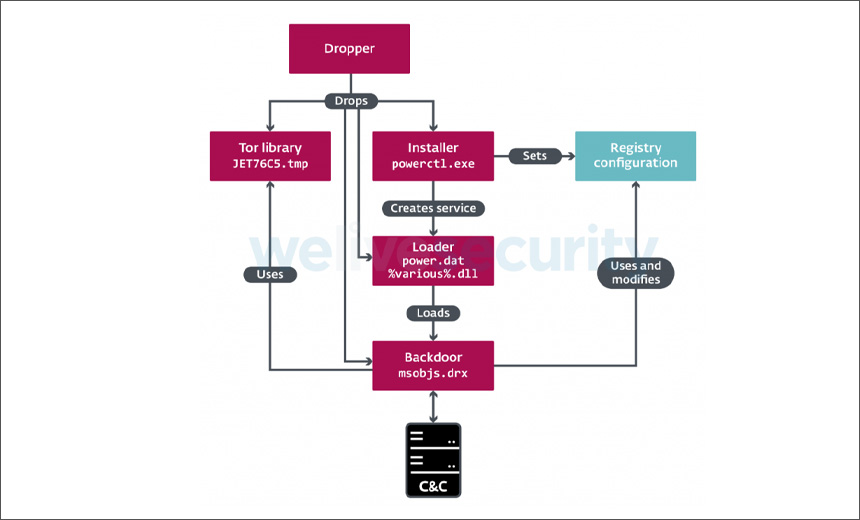
How Vyveva Works
Vyveva has several components, including an installer, a loader and the backdoor.
In the early stages of an attack, the loader works to decrypt the backdoor using an XOR-based algorithm. The installer then works to ensure persistence for the backdoor. The installer will also embed a default backdoor configuration file in the targeted device’s registry, which contains information such as a list of encrypted command-and-control servers, according to the report.
After these initial stages are complete, the backdoor is installed. It then attempts to connect to one of the command-and-control servers using the Tor network, sending out a signal every three minutes. Vyveva also deploys what ESET calls “watchdogs,” which monitor the device to see if other components are connected and check the number of active sessions, i.e., how often a user logs into the compromised device.
“The drive watchdog monitors newly inserted drives and notifies attackers. It allows them to exfiltrate files from the drive which are only temporarily available. This feature isn’t usually found in Lazarus backdoors,” Jurčacko says.
Thus, he notes, Vyveva appears to be much more sophisticated than other Lazarus tools.
Once installed, Vyveva can also exfiltrate files, gather information about the targeted device and its drives and run arbitrary code deployed by its operators. The malware can also perform timestomping, an anti-forensic technique used to alter or erase timestamps on files, the report notes.
Ties to Lazarus Group
The ESET researchers were able to tie the Vyveva backdoor to the Lazarus Group because it has features similar to other malware the group uses.
For example, Vyveva shares code similarities with a malware family known as NukeSped, a group of remote access Trojans. NukeSped has been previously linked to Lazarus in reports published by ESET and FortiGuard Labs.
Also, Vyveva deploys fake Transport Layer Security – TLS – protocols for network communication. The malware uses command line execution chains as well as encryption and Tor services, which are all hallmarks of Lazarus Group campaigns, according to the report.
“We can attribute Vyveva to this APT group with high confidence,” the report notes.
Frequent Malware Updates
Over the years, researchers have found that the Lazarus Group, which is called Hidden Cobra by U.S. government agencies, frequently updates its malware.
In March, security firm Sygnia reported the group was deploying the TFlower ransomware variant to target a dozen victims for data exfiltration or extortion (see: Lazarus Group Tied to TFlower Ransomware ).
In July 2020, Kaspersky found the group using a previously undetected malware framework called MATA to spread ransomware and steal databases. Another report by Kaspersky said the group was deploying a ransomware variant called VHD to target victims in Europe (see: Lazarus Group Reportedly Now Wielding Ransomware ).