Just 10 Vendors List 46% of All Offers
Cybercrime as-a-service
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Researchers Say Small Number of Core Individuals Selling Access to Hacked Networks
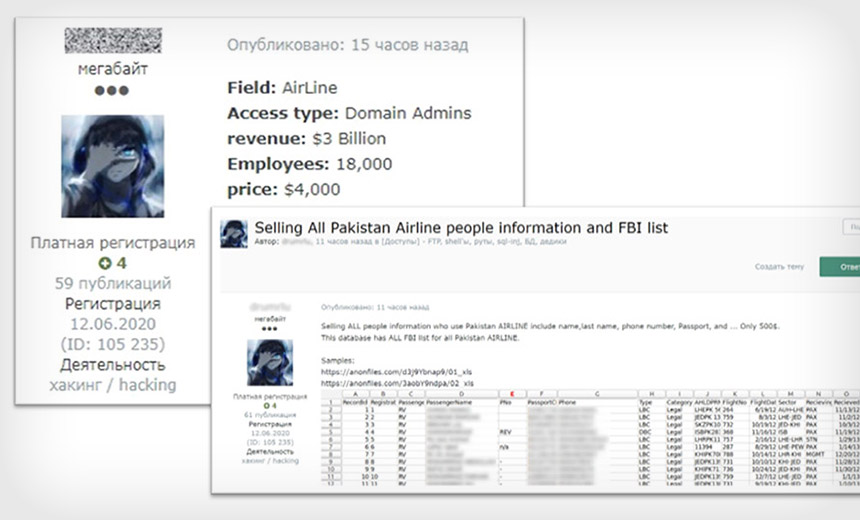
Initial access brokers continue to provide attackers with easy access to networks.
See Also: Lessons Learned: How IT SecOps Can Improve Risk Posture and Readiness in 2021
For a price – $5,400 is the average, while the median is $1,000, according to Israeli threat intelligence firm Kela – criminals can choose from a menu of victims, buy system access and then monetize their purchase by deploying ransomware or pursuing other types of attacks (see: 10 Initial Access Broker Trends: Cybercrime Service Evolves).
“As we noted for Q4 2020, the core of the most active initial access brokers again consisted of only around 10 actors.”
Given the reliance that many ransomware operations in particular appear to place on such “accesses,” one surprise might be just how few individuals appear to be serving as initial access brokers.
“As we noted for Q4 2020, the core of the most active initial access brokers again consisted of only around 10 actors,” Victoria Kivilevich, a threat intelligence analyst at Kela, tells me, comparing new research to research she published in January. These 10 actors “were responsible for selling 46% of all analyzed accesses, which comprised more than 1,000 listings.”
Kivilevich says the relatively low number of core brokers continues to surprise her, as does the difference between the average and median prices of the access being sold. “A lot of expensive offers highly influence the average price, but in reality, 50% of accesses cost less than $1,000,” she says, noting that this more accurately reflects “the price that many cybercriminals are ready to pay.”
Not All Listings Are Public
One caveat with counting listings is that threat intelligence analysts are only able to analyze what brokers list for sale, for example, on Tor-based cybercrime markets or forums. But this doesn’t provide a full picture, for numerous reasons:
- Vetting: Some brokers vet would-be buyers before showing them a more full menu.
- Obscuring victims: Listings might include a victim’s industry and approximate revenue and size. But victims rarely get named in advertisements, lest it tip off law enforcement authorities or the threat intelligence firms who keep close tabs on darknet sites that could then inform a victim.
- Actual sales: Whatever the sales price attached to a listing, how many of them sell, and for what final price, is not known.
- Private communications: How much remote access gets sold privately also is unclear.
- Partnerships: Some initial access brokers partner with ransomware operations or other crime groups, giving those groups either exclusive access or right of first refusal, again via private communications.
From what Kela has been able to see, however, demand for initial access brokers’ offerings has surged over the past 12 months.
But Kivilevich says that seeing so few individuals handle so much of the publicly listed initial access market “illustrates that no matter that a lot of new actors are continuing to enter the scene, most of them probably do not succeed at becoming prominent sellers.” Either that, she says, or “the most successful ones move quickly to private deals.”
Police Seek Cybercrime Ecosystem Disruption
Kela’s findings are a reminder that the cybercrime-as-a-service economy isn’t filled with untold numbers of suppliers. Of course, if law enforcement authorities could somehow arrest or disrupt this relatively small number of individuals, then they could take a big bite out of the access market, disrupting the wider cybercrime ecosystem.
In fact, that’s precisely the strategy police pursue, says cybercrime expert Alan Woodward, who’s a professor of computer science at England’s University of Surrey.
“There’s a misconception about how broad the base is when people talk about online organized crime,” he tells me. “It’s very dependent on relatively few things. First, the people with the technical skills – there are not that many of them who’ve gone to the dark side.”
Having relatively few core players makes them obvious law enforcement targets. “The bottom line is, if you could get to them, then obviously, you could stop anything new happening,” he says. “But also, it’s rather like the bulletproof hosters – it doesn’t happen by magic. There has to be infrastructure working somewhere for this to happen, including for ransomware. And a lot of effort has gone into trying to identify that and take it out, basically.”
Of course, such efforts can take time. That’s because cybercrime policing is often a waiting game, as in waiting for criminals to make a mistake. “The dark web is not as dark as it used to be – there are techniques being developed to try and identify these people,” he says. “I saw one the other day where they used an open URL, as well as their own Tor .onion URL. It’s a simple mistake – and like that, you were able to correlate the two. You can then start doing all the usual things on the IP addresses and geolocating them and all the rest of it. So you do catch a break every now and again, but you’ve got to keep watching.”
Looking specifically at initial access brokers, Woodward says he’s not surprised that so few individuals appear to dominate the market because it takes specialized skills. “Like any market, it ends up being dominated by relatively few people who – no pun intended – have the access, and the capability that goes with it, because it takes some doing and setting up.”
Such brokers often operate in a manner akin to fencing – dealing in stolen goods – because they have suppliers giving them access to victims to sell to, and they have customers buying this access, he says, meaning these brokers are acting as middlemen.
Shine a Light on Darknets
While not all access to victims gets sold in publicly accessible forums, monitoring such forums can give victims a heads-up that they’ve been breached before that access gets sold to others, or perhaps because stolen data is showing up for sale.
“Forewarned is forearmed,” Woodward says. “I’ve been involved in expert cases before where people have been breached for months and haven’t known, until a third party comes along and informs them.” One example is British Airways – not a case in which he was involved – which in 2018 got tipped off by a third party that credit card data was being routed from its site to a dodgy-looking website. After getting the alert, he said, the company was able to verify within about 90 minutes that it indeed had a problem, having previously failed to spot the breach for two months.
Numerous threat intelligence firms sell monitoring services to comb through forums looking for signs that an organization has been breached or its data has ended up in the wrong hands. Would paying for such services be valuable?
“The short answer is ‘Yes, I think it is,'” Woodward says. “Whether it’s actually value for money, I couldn’t say. But is it valuable? Yes … because they’re scuttling around in those dark recesses, and they might well come across something that you just have no idea left your company. And at that point, you need to know what you’ve lost, and how you lost it, because somebody might be coming in and taking even more. How do you know they’re not still there? It’s things like that, that you need to be sure of; you need to act.”





