House SolarWinds Hearing Focuses on Updating Cyber Laws
Lawmakers and Witnesses See Expanded Role for CISA Following Attack

A pair of U.S. House committees held their first public hearings Friday into the SolarWinds attack, with lawmakers and witnesses offering support for expanding federal cybersecurity laws to address the security failures.
The U.S. House Oversight and Reform Committee and the House Homeland Security Committee held joint hearings Friday and heard testimony from top executives of three tech and security firms affected by the hacking – FireEye, Microsoft and SolarWinds. Many of the same executives spoke earlier this week in front of the Senate Intelligence Committee, which is conducting its own investigation into the attack (see: Senators Grill Cybersecurity Execs on SolarWinds Attack).
See Also: Live Webinar | SolarWinds Breach: If Cyber Companies Can Get Hit, Do You Stand A Chance?
The committees also heard from Kevin Thompson, the former CEO of SolarWinds, who had not testified at the Senate hearing earlier this week.
During his opening statement, Rep. Bennie G. Thompson, D-Miss., the chair of the Homeland Security Committee, noted that the nation’s laws need to be updated to address the concerns raised by the attack. This includes sharing threat intelligence across the federal government and private enterprises and increasing the ability for agencies such as the U.S. Cybersecurity and Infrastructure Security Agency to conduct more extensive threat hunting across federal networks.
“My goal in our joint investigation is to move beyond admiring the complexities of this campaign and the challenges associated with stopping one like it and start charting a path forward,” Thompson said. “In the 15 years I have served on the Homeland Security Committee, one thing has become clear: We can’t become so consumed by preventing the last attack that we’re blind to the threats of the future. Instead, we must identify systemic opportunities to improve our ability to prevent, defend against, mitigate and raise the costs of all malicious cyber activity.”
Rep. John Katko, R-N.Y., the ranking member of the Homeland Security Committee, also noted during his opening remarks that while CISA had been given expanded authority to conduct threat hunting under the 2021 National Defense Authorization Act, added resources and authority are needed.
“CISA still does not have the proper authorities, resources or holistic visibility into the federal networks enterprise to effectively defend, and nimbly respond to, attacks,” Katko said.
While several lawmakers talked about expanding breach reporting laws or giving additional oversight to agencies such as CISA, no specifics were discussed, although Katko said he’s working with others on various proposals.
Several executives who testified at the hearing also advocated for stronger federal laws when it comes to disclosing breaches and the ability to share intelligence and data with federal agencies such as CISA. Microsoft President Brad Smith noted that while companies such as his came forward after the SolarWinds hack was disclosed in December 2020, others might be hesitant for fear of exposing themselves to possible legal actions.
Smith stressed that private companies and federal agencies should be able to share cybersecurity intelligence, but that the country’s breach disclosure laws should also be tightened to encourage targeted organizations to come forward.
“Silence is not going to make this country stronger, Smith said. “So I think we have to encourage, and I think even mandate, that certain companies do this kind of reporting.”
Unanswered Questions
While some lawmakers focused on laws that could address some of the cybersecurity concerns raised by the SolarWinds hack, others focused on how the incident occurred.
As he did in his testimony earlier this week in front of the Senate committee, FireEye CEO Kevin Mandia explained how his company’s investigation into their breach led back to the Trojanized software update that was sent to customers of SolarWinds’ Orion network monitoring platform over three months in 2020 (see: Senate SolarWinds Hearing: 4 Key Issues Raised).
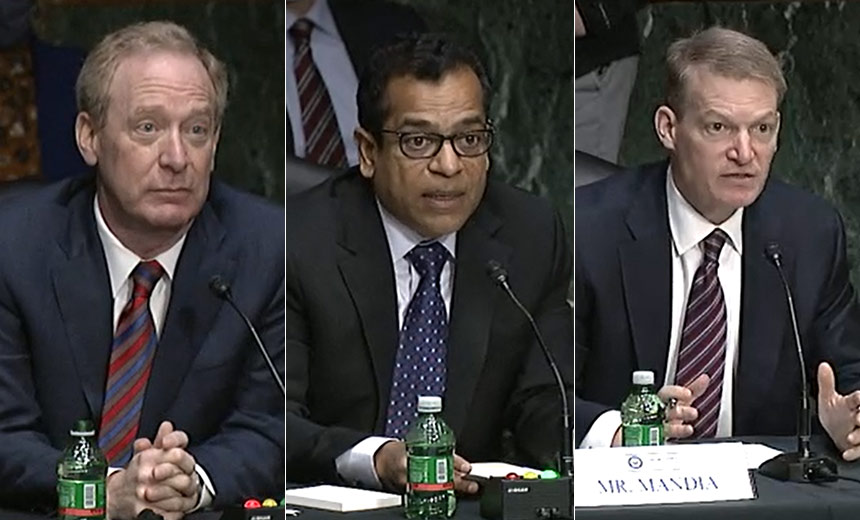
Mandia also stressed that once the backdoor called “Sunburst” was sent as part of the software update to about 18,000 SolarWinds Orion customers, the attackers almost immediately went after the organizations’ keys and tokens to begin to escalate privileges within the network, access other systems and remain hidden from various security tools.
As he noted earlier, Mandia testified that the attackers conducted a “dry run” of the attack in October 2019, before actual hacking started between March and June 2020. What made the attack so sophisticated is that the hackers were able to plant their malware into the very end of the software update build process to alter the production environment, which made the hack much harder to detect.
“When we investigated that and started pulling the thread, the earliest evidence of compromise kept going back to the SolarWinds server,” Mandia said. “And the reason I’m sharing this story with you is there is no magic wand on finding implant. People trust the third-party software that you are buying and relying on.”
How the initial intrusion into SolarWinds and its software production environment happened remains under investigation by both federal agencies and the companies affected. When questioned by Rep. Jim Langevin, D-R.I., SolarWinds CEO Sudhakar Ramakrishna noted that the attackers likely used one of three methods to gain the initial entry. These methods include a possible password spraying attack to guess usernames and passwords or the theft of employee credentials. Ramakrishna also left open the possibility that third-party software used internally by SolarWinds could have been compromised by the hackers.
“We are evaluating several terabytes of data and sifting through all this in the hopes that we can pinpoint ‘Patient Zero’ in this context,” Ramakrishna said.
Security Methods Questioned
During the opening of Friday’s joint hearing, Rep. Carolyn Maloney, D-N.Y., who is the chair of the House Oversight and Reform Committee, noted that the committee had obtained a 23-page PowerPoint presentation from a former SolarWinds employee who in 2017 had urged the company to develop better security practices.
When questioned about the presentation, Thompson, who retired from SolarWinds in December 2020, told lawmakers that members of his executive team had seen the presentation and had hired additional security and technology experts over the years and made investments in cybersecurity since that time.
“In fact, we spent more than the average technology company of our size over the last four years on security,” Thompson said on Friday. “So we have taken security very seriously … we knew security was important before that [presentation], and we were focused on it.”
Russia Still Suspected
During the joint hearing, the lawmakers and the tech executives reiterated that a nation-state hacking group, with possible connections to Russia, was likely behind the attack.
After the initial Trojanized software update was sent to SolarWinds customers, the hackers are believed to have specifically targeted at least 100 private companies and nine federal agencies with additional, secondary malware that allowed them to conduct a cyberespionage campaign that includes accessing and stealing email accounts as well as source code and other data (see: White House Preparing ‘Executive Action’ After SolarWinds Attack).
Smith and Mandia testified that the hack was likely tied to an intelligence agency with advanced capabilities and skilled personnel who were able to pull off such an attack. The two also noted that the attack that targeted SolarWinds is likely one of several operations that have been conducted by this hacking group.
“So this was the varsity team on offense. All the signs and all the digital fingerprints that our company cataloged proves that this was a foreign intelligence service,” Mandia said.