HolesWarm crypto malware hits unpatched Linux, Windows servers
Researchers are calling the HolesWarm the “king of vulnerability exploitation” as the malware has already exploited 20 known Linux and Windows vulnerabilities in just a month.
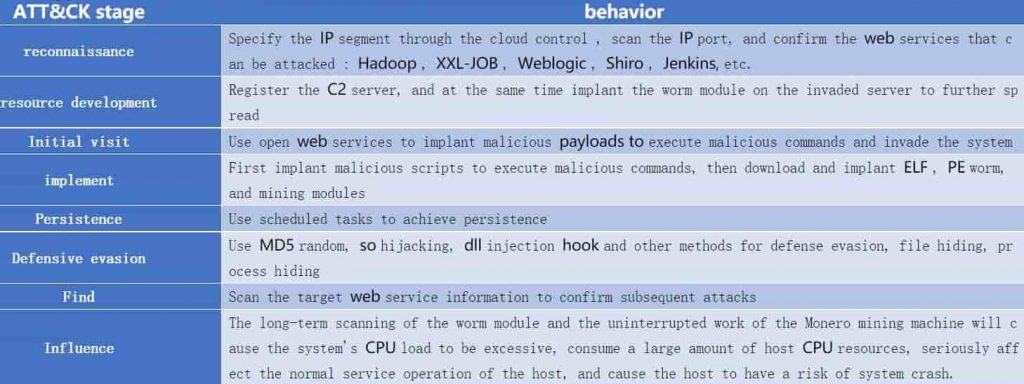
The IT security researchers at Tencent have disclosed details of a newly discovered malware with cryptomining capabilities leveraging over 20 known vulnerabilities, mainly in unpatched Windows and Linux servers.
Dubbed the HolesWarm cryptominer; the malware has invaded more than 1,000 cloud hosts since June 2021. HolesWarm tries to break into cloud hosts and has been so successful at infiltrating systems that Tencent researchers have declared it the “king of vulnerability exploitation.”
SEE: Unpatched MS Exchange servers hit by cryptojacking malware
Tencent researchers have warned governments and organizations to beware of HolesWarm and implement patches as soon as possible to prevent the malware from infecting their systems.
“Tencent security experts recommend that the operation and maintenance personnel of government and enterprise organizations actively repair high-risk vulnerabilities in related network components to avoid servers (becoming) a broiler controlled by hackers,” Tencent’s report read.
Malware quickly change its attack method
Considering that the malware has changed over twenty attack methods within such a short period, and the number of targeted cloud hosts is still rising, Tencent analysts concluded that the attackers are constantly improving their attack tactics.
Moreover, their analysis revealed that HolesWarm uses high-risk vulnerabilities in standard office server components such as:
- Jenkins
- Structs2
- Shiro
- Weblogic
- UFIDA
- Zhiyuan
- XXL-JOB
- Spring boot
- Apache Tomcat
They also noted that the malware could record the configuration’s version information with the same name text when it installs the malicious module by pulling or updating other malicious modules. Conversely, when the cloud configuration is relatively new, the virus will end the corresponding module process and be updated automatically.
Botnet Mines for Monero Cryptocurrency
Using the infected systems, HolesWarm looks to mine for Monero, so it seems that cryptominers have launched it to make money through cryptomining. But they can only earn a profit if many machines are counting as many strings of blockchain.
For your information, cryptominers invade a system and make it part of a larger army of bots to mine for Monero utilizing the computer’s resources. Some of the known cryptomining malware include VictoryGate, PBot, LemonDuck, and Crackonosh. However, HolesWarm is different from other cryptominers as it also gives attackers control over the victim’s server and password information.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.