Heimdal Security Blog | Bombardier data posted on ransomware leak site following FTA hack
At the beginning of the week, Accellion File Transfer Appliance (FTA) was subject to a security breach and extortion campaign orchestrated by the FIN11 group. Following the attacks, Accellion issued an official statement announcing that they have patched four FTA vulnerabilities that were known to be exploited by the threat actors, and incorporated new monitoring and alerting capabilities to flag any suspicious behavior.
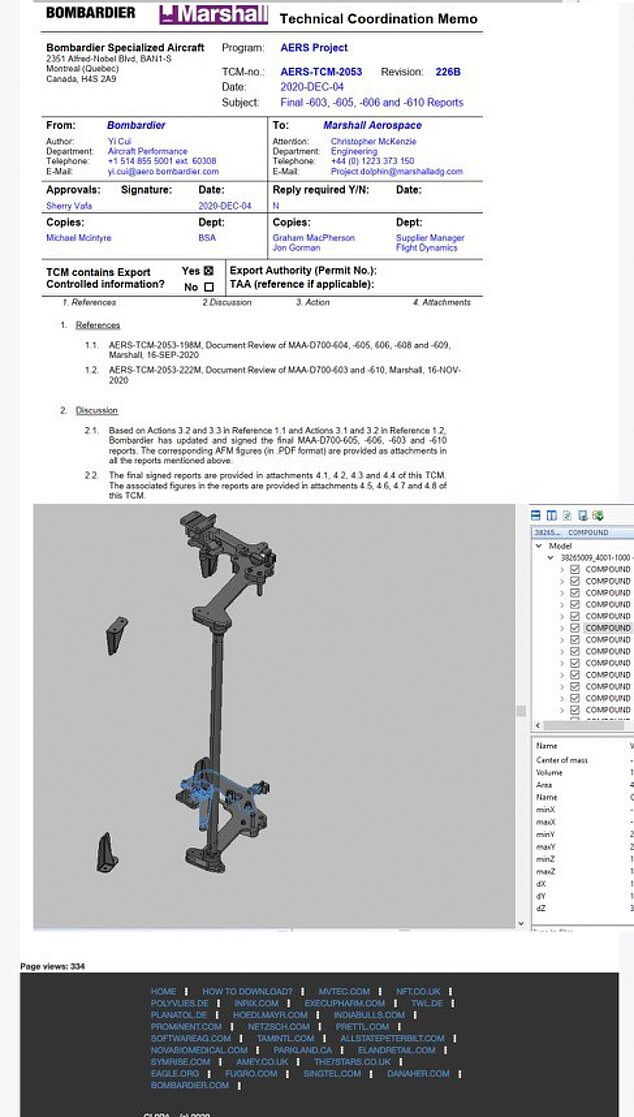
Regrettably, sensitive information for Canadian jet manufacturer Bombardier has been leaked on the dark web by hackers as it is believed the company refused to pay a ransom. Thus, Bombardier was among various corporations using Accellion’s FTA software, which was exploited to steal documents. A vulnerability in the application was revealed in December 2020, and it appears hackers were fast enough to make hay before developers found a way around their deployments.
Bombardier, whose Global 6000 jet is used for Swedish defense company Saab’s GlobalEye spy plane system, announced via a press release that it was recently subject to “a limited cybersecurity breach.” In its statement, Bombardier did not directly comment on Clop’s leak of the plane schematics.
In accordance with established cybersecurity procedures and policies, Bombardier promptly initiated its response protocol upon detection of the data security incident. As part of its investigation, Bombardier sought the services of cybersecurity and forensic professionals who provided external confirmation that the company’s security controls were effective in limiting the scope and extent of the incident. Bombardier also notified appropriate authorities, including law enforcement, where required and will continue to work with the authorities as the investigation continues.
However, the leak appears to disclose specifications and mechanics for the GlobalEye airborne early warning and control platform. The leak also included confidential information about customers, suppliers, and employees, as well as flight test reports and parts blueprints.
Bombardier stated that around 130 employees located in Costa Rica were affected by the data breach and the company has been contacting stakeholders including customers and employees whose data was potentially compromised.
Other companies that had their data listed on the CLOP site so far are Fugro, Danaher, Singapore’s largest telco, Singtel, and Law firm Jones Day.
Additionally, The Reserve Bank of New Zealand, The Australian Securities and Investments Commission (ASIC), Law firm Allens, The University of Colorado, The Washington State Auditor Office, QIMR Berghofer Medical Research Institute, and US retail store chain Kroger have all reported security breaches due to attacks on their FTA servers without having their data leaked on the CLOP site.
The FIN11 group is known for targeting prominent companies for its ransomware extortion activities, which include infiltrating businesses’ networks, withdrawing and encrypting files, and demanding payment to not only restore the tangled data but also to not publicly release the sensitive pilfered information.






