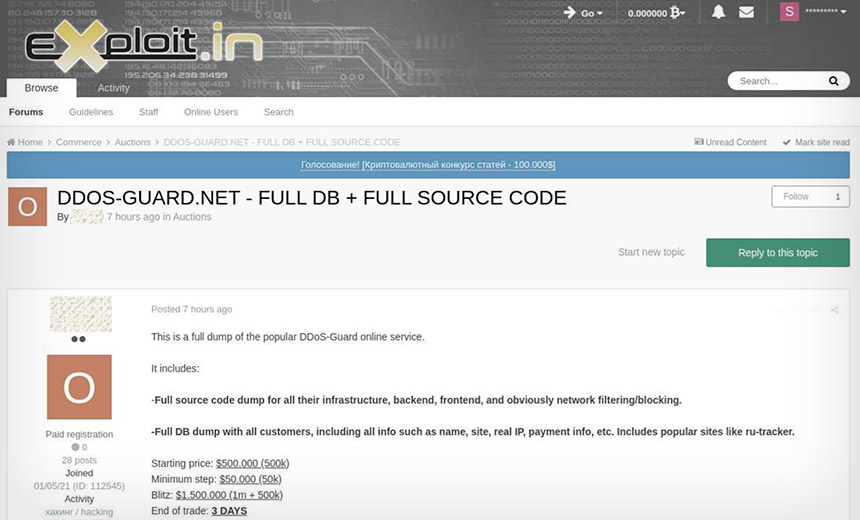
‘Full Source Code Dump’ of DDoS-Guard Service
Cybercrime
,
Fraud Management & Cybercrime
,
Fraud Risk Management
DDoS-Guard Disputes Exploit.in Listing for Customer Data. But What’s the Risk to Users?
Leaked data getting offered for sale via cybercrime forums and markets seems so commonplace as to be virtually unremarkable, save perhaps for the choice of a victim.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
But these leaks can, of course, indicate that a site or service got breached – perhaps without its operators being any the wiser.
“DDoS-Guard … obstructs the identification of website owners of hundreds of shady resources that are engaged in illicit goods sale, gambling and copyright infringements.”
One such potential victim: DDoS-Guard, an apparently Russia-based company that offers defenses against distributed denial-of-service attacks. Alleged customer data from the company has been offered for sale on a cybercrime forum.
On Exploit.in, a user on May 26 listed for sale “a full dump of the popular DDoS-Guard online service,” with a starting price for the auction set at $500,000, or a “blitz” price – think “buy it now” – set at $1.5 million. But the starting price for the auction was later reduced to $350,000.
Is the data offered for sale even real? Or might this be an attempt to smear DDoS-Guard – based on its customer base – or a rival seeking to disrupt its business?
DDoS-Guard, which bills itself as being “one of the leading service providers on the global DDoS protection and content delivery markets since 2011,” has a questionable reputation.
Singapore-based cybersecurity firm Group-IB reports that beyond DDoS defenses, “DDoS-Guard also provides computing capacities and obstructs the identification of website owners of hundreds of shady resources that are engaged in illicit goods sale, gambling and copyright infringements.”
“We’ve seen a number of rogue websites hosted by DDoS-Guard,” says Reza Rafati, a senior analyst at Group-IB’s CERT-GIB incident response unit in Amsterdam. “They were almost impossible to take down. Their answer to our numerous complaints on them protecting illegal resources is that they are not the owners of these websites. Such a safe environment for illicit online activity doesn’t do any good for the global effort against cybercrime.”
What’s for Sale?
The Exploit.in dump allegedly included a full customer DDoS-Guard database listing “all info such as name, site, real IP, payment info, etc.” The user claimed that the customer list included a number of well-known sites, such as RuTracker.org, which is a Russian-language BitTorrent tracking site.
The listing states that the sale also includes a “full source code dump” for DDoS-Guard’s “infrastructure, backend, frontend, and obviously network filtering/blocking.”
A spokesman for DDoS-Guard has dismissed the Exploit.in seller’s claims. “We are aware that malefactors are trying to sell a certain database. Our company has not experienced any data leaks,” Ruvim Shamilov, DDoS-Guard’s PR manager, tells me. “It is not the first time they threaten us, try to sell nonexistent data and make a profit on our company’s name.”
Indeed, whether any real data is being offered for sale remains an open question.
“The threat actor didn’t provide a sample of the database, which makes it impossible to verify the authenticity of the reported stolen database and the source code,” says Oleg Dyorov, a threat intelligence analyst at Group-IB.
Target: DDoS-Guard
That DDoS-Guard would be a target isn’t surprising.
Customers attributed to DDoS-Guard by the domain and IP address data service SecurityTrails include Hamas – the Palestinian militant group that rules Gaza – as well as massive numbers of sites with scammy-looking names that are potentially used by fraudsters, such as “bitdefender-centrals.com,” “nortoncomsetupz.com” and “garmin-express.support.”
DDoS-Guard gained extra notoriety last year for hosting far-right forums such as 8chan, which is filled with conspiracy theories promoting racism and anti-Semitism, and QAnon, which is based on the thoroughly disproven conspiracy theory that a group of Satanic-worshipping pedophiles – who also practice cannibalism – traffic in stolen children and conspired to disrupt Donald Trump’s presidency.
The service also hosted the right-leaning social network Parler after Apple and Google booted the mobile app from their app stores and Amazon barred Parler from using its hosting services.
Where the company is based, and from whom it procures hosting resources, is not clear. As cybersecurity blogger Brian Krebs reported in January, security researcher Ron Guilmette investigated the internet addresses assigned to DDoS-Guard Corp., finding that it appears to mostly operate from Russia, although it’s officially based in Belize, with an arm of the business called Cognitive Cloud LLP based in Edinburgh, Scotland.
Risk to Customers: Unclear
Regardless of the locations from which it operates, if DDoS-Guard did get breached and customer data was stolen, what’s the risk posed to users of the service?
For DDoS-Guard users, depending on who gets their hands on the customer database dump – and if it’s legitimate – anyone who’s been running sites hosted on its service could soon be identified.
But law enforcement agencies likely already have this information, says cybersecurity expert Alan Woodward, who notes that police have historically paid close attention to services – and customers of services – that may be tied to anything in the crime-as-a-service ecosystem. “Anything that is done at scale, and particularly where it is crime as a service, is bound to attract the attention of the police,” says Woodward, who’s a visiting professor of computer science at the University of Surrey.
As countless takedowns have demonstrated, law enforcement agencies regularly look for ways not just to disrupt services tied to any illicit activities but also to track users of the service.
As demonstrated by encrypted messaging service takedowns – including EncroChat, Sky Global and more recently Anom – police don’t hesitate to try to gain access to networks allegedly used by criminals – and to watch what they’re doing before trying to pull the plug.
Woodward says police prioritize this type of one-two punch whenever possible.
“Cutting the head off the snake gives some respite,” he says. “But catching those who would use such a service helps suppress the ‘market’ and hence there is less reason for someone to start a replacement.”