FireEye, CISA Warn of Critical IoT Device Vulnerability
Endpoint Security
,
Internet of Things Security
Researchers: Kalay Protocol Flaw Could Affect Millions of Connected Devices
FireEye researchers and the U.S. Cybersecurity and Infrastructure Security Agency are warning about a critical vulnerability that could allow an attacker to gain remote access to potentially millions of compromised IoT devices, such as connected security cameras.
See Also: Live Webinar | Password Management: Securing Hybrid Work for the Long Haul
The flaw, tracked as CVE-2021-28372, is found in ThroughTek’s Kalay protocol, which the FireEye researchers estimate is used in some 83 million IoT and connected devices worldwide, although it’s not known how many of these devices might be affected.
So far, however, there has been no exploit of the vulnerability detected, according to CISA.
A newer version of the Kalay protocol addresses the flaw and can secure devices against an attack. CISA is also offering other risk mitigation tips.
Kalay
Kalay is a network protocol that helps devices easily connect to a software application. In most cases, the protocol is implemented in IoT devices through a software development kit that’s typically installed by original equipment manufacturers. That makes tracking devices that use the protocol difficult, the FireEye researchers note.
The Kalay protocol is used in a variety of enterprise IoT and connected devices, including security cameras, but also dozens of consumer devices, such as “smart” baby monitors and DVRs, the FireEye report states.
“Because the Kalay platform is intended to be used transparently and is bundled as part of the OEM manufacturing process, [FireEye] Mandiant was not able to create a complete list of affected devices and geographic regions,” says Dillon Franke, one of the three FireEye researcher who conducted the research on the vulnerability.
FireEye’s Mandiant Red Team first uncovered the vulnerability in 2020. If exploited, the flaw can allow an attacker to remotely control a vulnerable device, “resulting in the ability to listen to live audio, watch real-time video data and compromise device credentials for further attacks based on exposed device functionality,” the security firm reports.
Critical Vulnerability
The bug has been assigned a CVSS score of 9.6, making the vulnerability critical. FireEye, CISA and ThroughTek are urging users and OEMs to upgrade to a newer version of the Kalay protocol to mitigate the risk.
In its alert issued Tuesday, CISA notes that organizations can also mitigate possible threats by disconnecting devices that use the vulnerable Kalay protocol from the public internet, placing these devices behind a firewall or isolating them from the business network and deploying a VPN to connect to these IoT devices.
“Organizations observing any suspected malicious activity should follow their established internal procedures and report their findings to CISA for tracking and correlation against other incidents,” the CISA alert notes.
Kalay Protocol Flaw
Over several months in 2020, the FireEye researchers used two methods to check for vulnerabilities in ThroughTek’s offerings, including the Kalay protocol.
The first involved downloaded and disassembled applications from both the official Google Play Store and Apple App Store that included ThroughTek libraries. The second included researchers buying connected devices that utilized the Kalay protocol and performing “local and hardware-based attacks to obtain shell access, recover firmware images and perform additional dynamic testing,” according to the FireEye report.
The FireEye researchers eventually developed a fully functional implementation of the Kalay protocol, which enabled the team to perform several actions on networks, including device discovery, device registration, remote client connections and authentication of devices as well as the ability to process audio and video data, according to the report.
Once the researchers created their own interface for manipulating the Kalay protocol requests and responses, the team began identifying logic and flow vulnerabilities, including the ability to identify, access and register devices that use the vulnerable protocol.
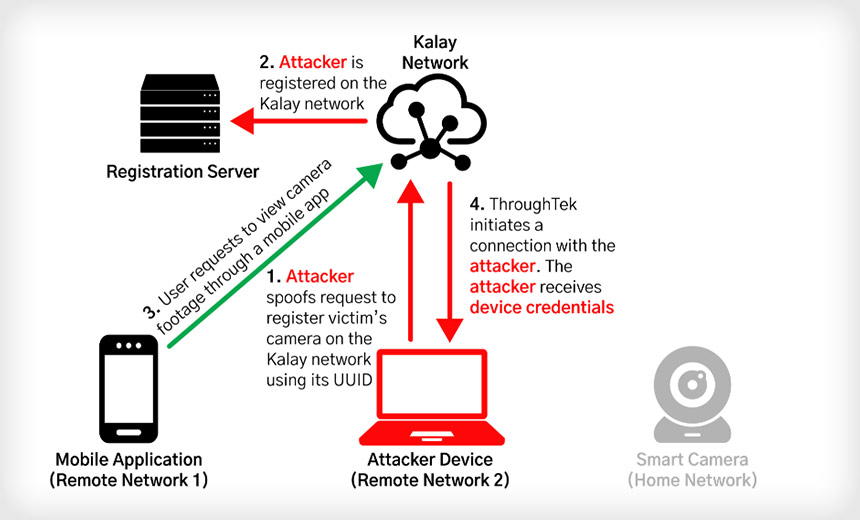
The FireEye team found it could obtain a Kalay-enabled device’s uniquely assigned identifier – aka UID – through a web API, such as a mobile application, the report notes.
https://www.youtube.com/watch?v=PBiW-rg8-LE
“If an attacker obtains a UID of a victim Kalay device, they can maliciously register a device with the same UID on the network and cause the Kalay servers to overwrite the existing Kalay device,” according to the report. “Once an attacker has maliciously registered a UID, any client connection attempts to access the victim UID will be directed to the attacker.”
From there, an attacker could capture other device user details, such as username and password, allowing the attacker to further manipulate a vulnerable device, the researchers note.
“With the compromised credentials, an attacker can use the Kalay network to remotely connect to the original device, access data and execute [Remote Procedure Call] calls. Vulnerabilities in the device-implemented RPC interface can lead to fully remote and complete device compromise,” according to the report.
The FireEye team developed a proof-of-concept attack based on its discovery of the vulnerability in the Kalay protocol, but the company did not publish the exploit code.
Franke notes that this type of vulnerability, which affects so many different types of IoT devices and can also give an attacker remote access, is one that cybercriminals and nation-state groups might want to exploit.
“Mandiant envisions cybercriminals and nation-state actors alike being interested in this vulnerability,” Franke says. “Cybercriminals could use a working exploit to steal sensitive data from victims or extort them into paying money, while nation-state actors could potentially use this vulnerability to perform mass surveillance of Kalay network users.”
In June, researchers from Nozomi Networks published their own report about vulnerabilities in ThroughTek’s peer-to-peer protocol used to power connected security cameras. In that case, however, attackers attempting to exploit the vulnerability could not gain remote access.
Another IoT Concern
German security firm IoT Inspector on Monday published an advisory noting its researchers had found vulnerabilities affecting Wi-Fi-enabled devices using an SDK from Realtek that could affect hundreds of thousands of devices.
As with the vulnerability in the Kalay protocol, there is no known public exploit of the Realtek flaw, and the company has now issued patches for the bug.
The researchers found flaws in the Realtek RTL819xD chipset. By exploiting these vulnerabilities, unauthenticated remote attackers could compromise the target device and execute arbitrary code with the highest level of privilege, the German researchers say.
Principal Correspondent Prajeet Nair contributed to this report.






