Feds Charge Verkada Camera Hacker With ‘Theft and Fraud’
Application Security
,
Cybercrime
,
Device Identification
Swiss Citizen Allegedly Leaked Victims’ Stolen Data, Including Source Code

A Swiss national who recently highlighted flaws in internet-connected Verkada surveillance cameras has been charged with hacking.
See Also: Top 50 Security Threats
A federal grand jury indictment returned Thursday in U.S. District Court in Seattle charges Tillie Kottmann, 21, with “computer intrusion and identity and data theft activities spanning 2019 to the present,” the Justice Department says.
Last week, Kottmann released pictures obtained from some of Silicon Valley startup Verkada’s 150,000 internet-connected cameras, showing the interiors of offices and U.S. technology firms and footage from an apparent interrogation that took place earlier this month at the Stoughton Police Department in Massachusetts, as well as the inside of a Shanghai factory owned by carmaker Tesla, among other locations (see: Startup Probes Hack of Internet-Connected Security Cameras).
On March 12, Swiss authorities executed search warrants and seized devices from Kottmann’s apartment in Lucerne, Switzerland, as part of the investigation, which is being led by the FBI’s cyber task force in Seattle. Officials say Kottmann remains in Lucerne.
According to the indictment, Kottmann – aka “Tillie Kottmann,” “deletescape” and “tillie crimew,” among other monikers – “is a member of a group of cybercriminal actors engaged in the hacking of protected computers of corporate and government entities and the theft and public dissemination of confidential and proprietary information, including source code and internal data.”
Kottmann’s group calls itself APT 69420, aka “Arson Cats,” which is a tongue-in-cheek riff on the names cybersecurity firms assign to nation-state and cybercrime hackers they track.
No other members of Arson Cats have been named in the indictment, which charges Kottmann with:
- One count of conspiracy to commit computer fraud and abuse – punishable by up to five years in prison;
- Multiple counts of wire fraud and one count of conspiracy to commit wire fraud – punishable by up to 20 years in prison;
- One count of aggravated identity theft – punishable by a mandatory minimum 24 months in prison, which would run consecutively following any other sentence being served.
Accused of Hacking ‘Dozens of Companies’
The indictment states that “as of March 2021, Kottmann has hacked dozens of companies and government agencies and purportedly has published internal files and records of more than 100 entities for public review and download.”
“Stealing credentials and data, and publishing source code and proprietary and sensitive information on the web is not protected speech – it is theft and fraud,” says acting U.S. Attorney Tessa M. Gorman. “These actions can increase vulnerabilities for everyone from large corporations to individual consumers. Wrapping oneself in an allegedly altruistic motive does not remove the criminal stench from such intrusion, theft and fraud.”
The indictment describes nine hacked organizations, but names only one of Kottmann’s alleged victims: the Washington State Department of Transportation, from which web application source code was stolen. But other organizations for which Arson Cats has publicly claimed to have accessed systems, or has released data, include Intel, the U.S. government’s National Reconnaissance Office and carmaker Nissan North America.
The release of the Verkada systems and publishing of surveillance camera footage is not mentioned in the indictment. But additional evidence could later be submitted to the court – for example, in the form of a superseding indictment – or used if the case goes to trial.
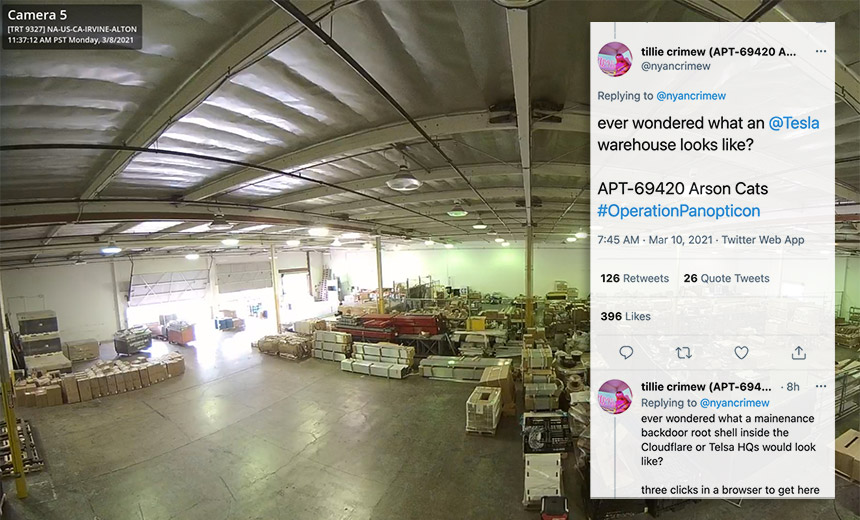
Verkada’s cameras are used by a number of large companies, schools, local government agencies and healthcare institutions. Kottmann earlier this month tweeted that Arson Cats gained access to multiple Verkada cameras, from March 7 to 9, after the surveillance firm left a Jenkins build server open to the internet, which allowed for the capture of “super admin” credentials. Those credentials facilitated the viewing of live feeds from the cameras, including at locations operated by Tesla, Okta and Cloudflare.
The indictment accuses Kottmann of regularly targeting code repositories, also known as gits, as well as copying and cloning source code repositories and confidential and proprietary files, some of which contained administrative credentials and access keys. “Kottmann then used such means of access to further infiltrate the internal infrastructure of victims and copy additional files, records, and information,” according to the indictment.
“To recruit others, grow the scheme, and further promote the hacking activity and Kottmann’s own reputation in the hacking community, Kottmann actively communicated with journalists and over social media about computer intrusions and data theft,” the Justice Department say (see: Verkada’s Camera Debacle Traces to Publicly Exposed Server).
Kottmann allegedly published some of this data on the git.rip website, which was registered in November 2019 and recently seized by the Justice Department.
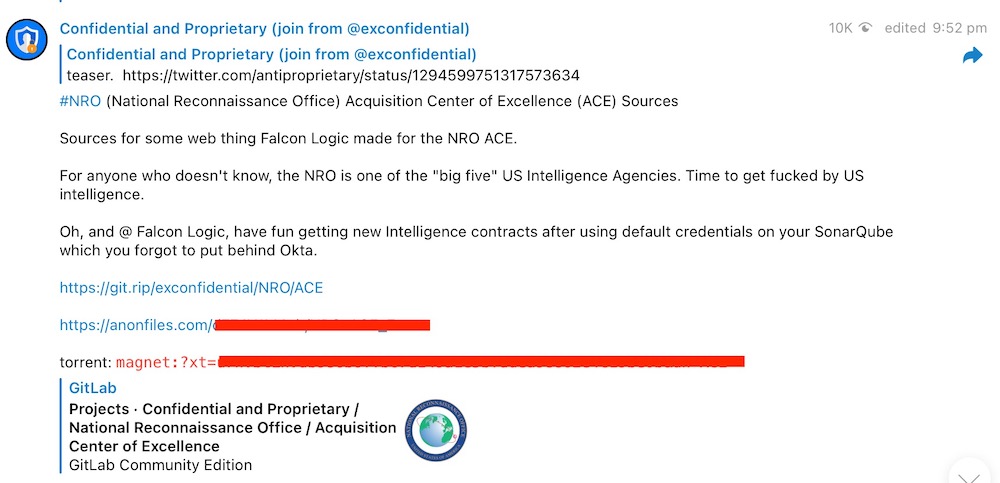
The indictment also accuses Kottmann of publishing stolen data – including from “other actors’ hacking conduct” – on a Telegram channel called “ExConfidential” as well as to an unnamed, “foreign-based file-sharing service.” It also alleges that as part of the conspiracy to commit computer fraud and abuse, Kottmann benefited financially by designing clothing and paraphernalia tied to “computer hacking activity and anti-intellectual-property ideology.”
List of Alleged Victims
Kottmann previously also ran a Telegram channel called “Confidential & Proprietary.” The indictment lists dates when Kottmann allegedly publicly posted data, making it possible to deduce victims compared to what Kottmann posted around the same time via the Telegram channel, as well as via details furnished in press reports or media interviews.
Thus, other victims referenced in the indictment appear to be security device manufacturer React Mobile; tactical equipment manufacturer Tactical Electronics; “a microchip and processor manufacturer” that appears to be Intel; a U.S. government agency – the National Reconnaissance Office; investment platform Axial; and Nissan North America.
Ethical Disclosure Questions
The case seems sure to shine a light on so-called ethical disclosure. Kottmann previously stated in media interviews that Arson Cats made no effort to notify organizations of any vulnerabilities they may have found in advance of leaking data or information the group had obtained.

Many individuals who undertake security research, by comparison, engage in coordinated disclosure with organizations. Google, for example, typically gives an organization 90 days to fix a flaw, before publicly describing it. Some researchers report flaws instead via bug-bounty programs run either by companies themselves or other organizations. These may carry different notification terms and conditions and provide cash compensation for researchers’ efforts.
As with the Verkada breach, Kottmann often publicly detailed exactly which security problems Arson Cats had found, allowing it to access systems. Misconfigured gits and servers were a common culprit, and the group on numerous occasions reported success with using specialized search engines such as Shodan to identify misconfigured or poorly secured internet-connected devices and applications.
Beyond using Shodan to search for such devices, attempting to exploit any potential misconfiguration issues is a step that many security experts and analysts avoid, for fear of violating computer security laws.
FBI Flash Alert: SonarQube Hacks
Kottmann’s previous alleged efforts had already garnered a response from U.S. officials, although Kottmann was not named.
In October 2020, the FBI published an advisory warning that hackers were targeting misconfigured instances of SonarQube, which is software for auditing code and discovering bugs (see: Federal Source Code Accessed Via Misconfigured SonarQube).
The FBI warned that hackers were scanning the internet for SonarQube instances exposed to the internet via the default 9000 port and then using default administrator credentials to try and access SonarQube instances.
Kottmann has previously cited SonarQube instances as the source for Arson Cats data leaks tied to several companies.
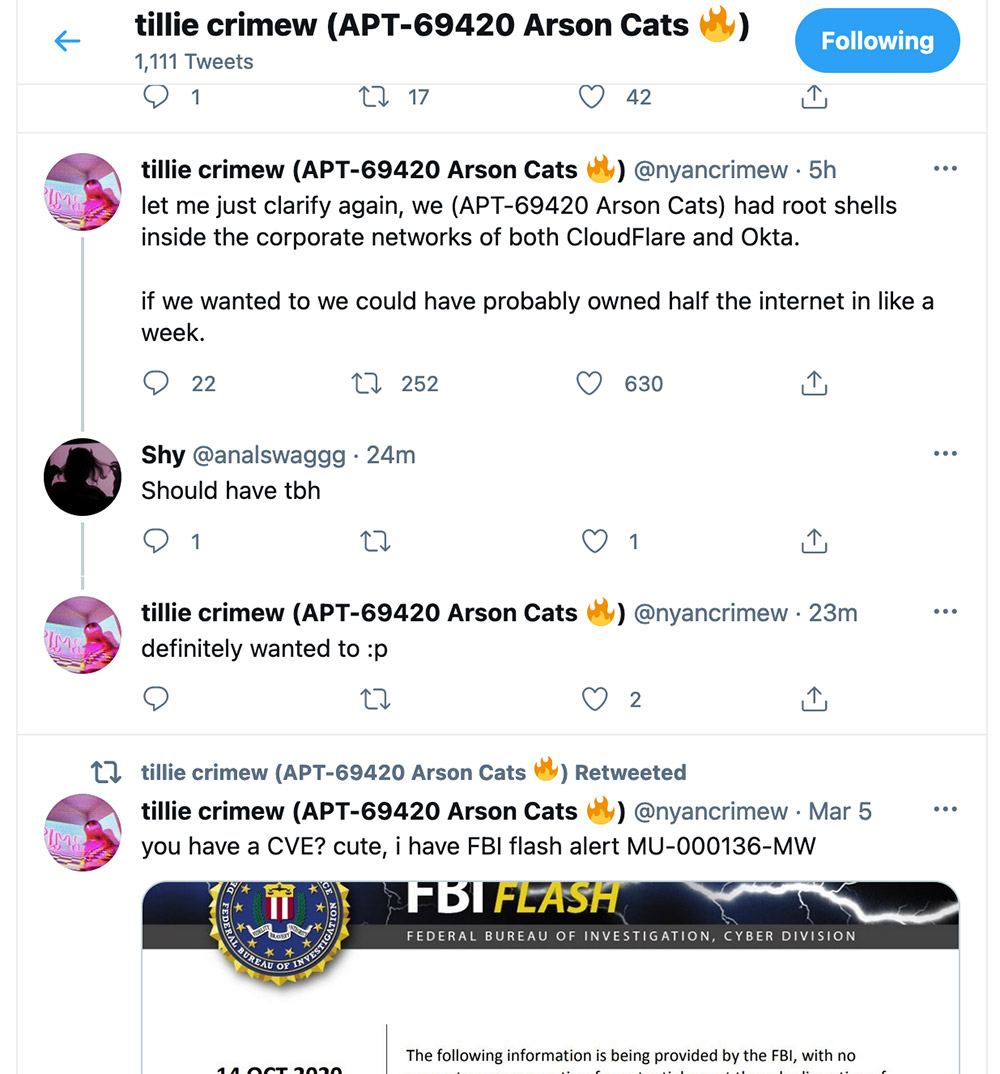
Last week, via Twitter, Kottmann also took credit for being the focus of the FBI’s October 2020 SonarQube alert.