Espionage Is Goal of Iranian Phishing Campaign
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
,
Next-Generation Technologies & Secure Development
Researchers: Hackers Exploit Remote Admin Tools
Hackers with suspected ties to Iran are continuing to wage a cyberespionage campaign against government agencies, academia and tourism organizations in the Middle East and nearby, according to a report by Trend Micro.
See Also: Top 50 Security Threats
The spear-phishing campaign, dubbed Earth Vetala, which is designed to steal data, exploits remote admin tools such as ScreenConnect and Remote Utilities that allow system administrators to remotely manage their enterprise systems, Trend Micro says.
“We believe, with moderate confidence, that this newly identified activity is connected to [the threat group] MuddyWater, also known as TEMP.Zagros, Static Kitten and Seedworm,” the researchers note.
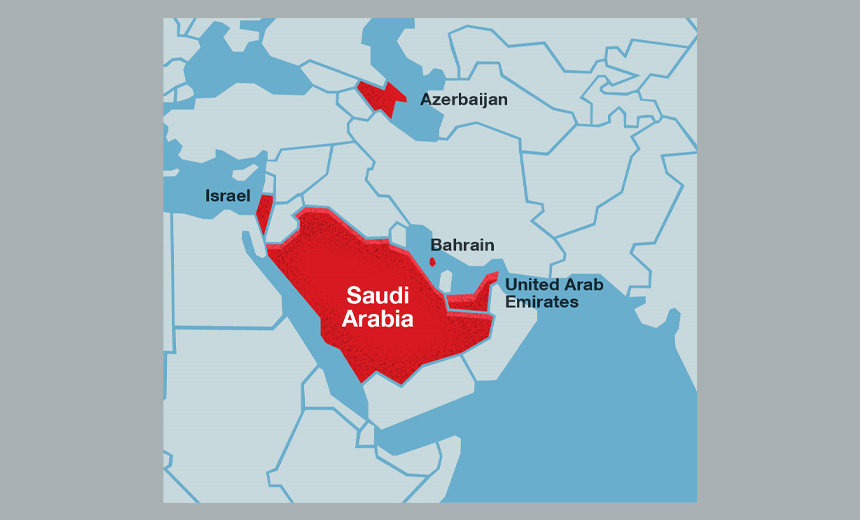
The Earth Vetala attacks have been observed in Azerbaijan, Bahrain, Israel, Saudi Arabia and the United Arab Emirates, Trend Micro reports.
First spotted in 2017, MuddyWater has used spear-phishing to target government agencies, military institutions, telecommunications companies and universities throughout the Middle East, according to a previous analysis by Kaspersky. The group has also attempted cyberespionage operations in the U.S. and Europe, that report found.
Trend Micro was tipped off to the group’s latest activities by research from Anomali, which also identified a campaign targeting similar victims.
Attack Analysis
The Earth Vetala attacks use spear-phishing emails alleging to come from a government agency, with embedded links to a legitimate file-sharing service that eventually distributes malware, including password/process-dumping utilities, reverse-tunneling tools and custom backdoors. They then initiate communications with additional command-and-control infrastructure to execute obfuscated PowerShell scripts and establish a persistent presence within targeted hosts and environments, the researchers say.
Trend Micro researchers analyzed a spear-phishing email that attempted to persuade recipients to click a URL and download a malicious file. These files are mainly .PDF or .RTF files.
“As with the spear-phishing email, the lure documents’ content attempts to convince the victim to click on another malicious URL and download a .ZIP file,” the researchers note.
The .ZIP file contains a copy of legitimate remote administration software developed by Remote Utilities and allows downloading and uploading of files, grabbing screenshots, browsing files and directories, and executing and terminating processes, Trend Micro reports.
“We were able to discover multiple .ZIP files used to distribute the RemoteUtilities remote administration software in the manner above, with all of these distributing the same RemoteUtilities sample,” the researchers note. “The use of this tool differentiates this particular campaign from earlier [ones]; in previous attacks, ScreenConnect was used. Otherwise, the tactics, techniques and procedures in use remain broadly similar.”
Whenever the Remote Utilities software is executed, it launches msiexec.exe, researchers state. This installs a service on the victim machine called Remote Utilities – Host. The service then communicates with the domain id.remoteutilities.com, which belongs to Remote Utilities.
“This connection is related to one of its features called Internet-ID Connection. This feature allows an intermediary Internet server to broker the connection, similar to a proxy server. This allows the threat actor to connect to the internet-ID server, which then connects to the actual RemoteUtilities host,” the researchers note.
Shortcomings
Although this campaign uses remote access capabilities, the attackers seem to lack the expertise to use all of these tools correctly, Trend Micro reports. “This is unexpected since we believe this attack is connected to the MuddyWater threat actors – and in other connected campaigns, the attackers have shown higher levels of technical skill.”
Lewis Jones, threat intelligence analyst at the security firm Talion, says the targets and malware functionality of MuddyWater attacks have been expanding in recent years.
“The attackers seem to be reasonably well-equipped for their goals, with relatively simple and expendable tools to infiltrate victims and exfiltrate data, predominantly via Python and PowerShell-based tools,” Jones says. “In relation to this specific attack, the initial method is to use phishing attacks to target organizations before delivering the final payload. Phishing attacks continue to be popular among APT groups, with a significant increase over the past 12 months.”
Risk Mitigation
Javvad Malik, security awareness advocate at the security firm KnowBe4, says this ongoing campaign in the Middle East showcases yet again that spear phishing is hackers’ most favored attack technique.
As a result, it’s essential to have technical protections in place and to educate users on how to spot and report potential phishing attacks, he says.