eCh0raix Ransomware Variant Targets QNAP, Synology NAS Devices
eCh0raix Ransomware Variant Targets QNAP, Synology NAS Devices


Business Continuity Management / Disaster Recovery , Fraud Management & Cybercrime , Governance & Risk Management Director of HSE, Nation’s Healthcare System, Describes the Costs Akshaya Asokan (asokan_akshaya) • June 24, 2021 The recovery costs for the May ransomware attack on Health Service Executive, Ireland’s publicly funded healthcare system, is likely to total…

Business Continuity Management / Disaster Recovery , Fraud Management & Cybercrime , Fraud Risk Management Palo Alto Networks Report Describes Tactics of Group Leveraging Open-Source Tools Dan Gunderman (dangun127) • July 16, 2021 Illustration: Palo Alto Networks The gang behind ransomware known as Mespinoza, aka PYSA, is targeting manufacturers, schools and others, mainly…

The Boston Public Library (BPL) has disclosed today that its network was hit by a cyberattack on Wednesday, leading to a system-wide technical outage. BPL serves almost 4 million visitors per year through its central library and twenty-five neighborhood branches, as well as millions more online. It is the third-largest public library in the United States behind the…

The latest edition of the ISMG Security Report features an analysis of ongoing investigations into how NSO Group’s Pegasus spyware is allegedly being used to spy on dissidents, journalists, political rivals, business leaders and even heads of state – and a discussion of whether the business model should be banned. In this report, you’ll hear…
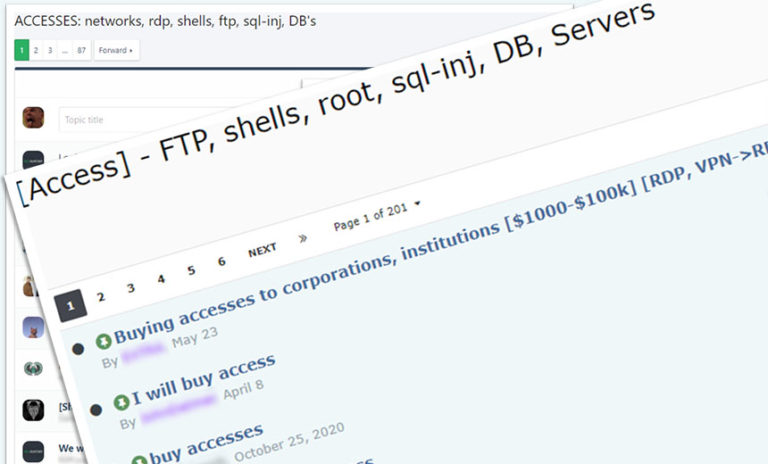
Cybercrime , Cybercrime as-a-service , Endpoint Detection & Response (EDR) Revenue, Size, Geography and Level of Access Help Determine Sale Price for Access Mathew J. Schwartz (euroinfosec) • September 6, 2021 Sections on the XSS and Exploit cybercrime forums that are dedicated to accesses (Source: Kela) The most sought-after type of victim for…

Thank you for registering with ISMG Complete your profile and stay up to date Title LevelAnalytics/Architecture/EngineeringAttorney / General Counsel / CounselAVPBoard of DirectorC – levelC Level – OtherCCOCEO / PresidentCFOChairpersonCIOCISO / CSOCISO/CSO/CIOCOOCROCTODirectorEVP / SVP / FVPHeadHealthcare ProfessionalManager / SupervisorPartnerSpecialist/OtherStaffVP–Other Title Level– Job FunctionAnti-Money Laundering (AML)AuditBSABusiness Continuity/Disaster RecoveryBusiness DevelopmentCashier / Customer Service / AdministrativeClinical Healthcare ProfessionalCloud…