DearCry Ransomware is Targeting Microsoft Exchange Servers
After Microsoft warned its customers against a Chinese nation-state cyberattack that is targeting the tech giant’s “Exchange Server” software, ransomware gangs have started to target vulnerable instances.
Microsoft has confirmed that a new strain of ransomware is targeting vulnerable on-premise Microsoft Exchange Servers through ProxyLogon vulnerabilities as cybercriminal groups focus on those who haven’t (or were unable to) apply the recommended patches.
We have detected and are now blocking a new family of ransomware being used after an initial compromise of unpatched on-premises Exchange Servers. Microsoft protects against this threat known as Ransom:Win32/DoejoCrypt.A, and also as DearCry.
According to Microsoft Security Intelligence, Microsoft Defender users who receive automatic updates are protected against this ransomware without having to take any further actions.
Microsoft guided on-premises Exchange Server users to prioritize security updates released this week for customers who are unable to update their Exchange environment to a version where Microsoft already has patches available. According to Palo Alto Networks, there are around 80,000 older servers that cannot apply Microsoft’s recent security updates directly.
DearCry seemed to be common ransomware, but it appears to contain no flaws that would allow victims to decrypt their data without payment, writes Lawrence Abrams.
As always, it’s easier to stop something happening in the first place than to repair the damage after it has happened, but in the event of an attack, you’ll wish you’d have off-site backups secured and put a disaster recovery plan in place.
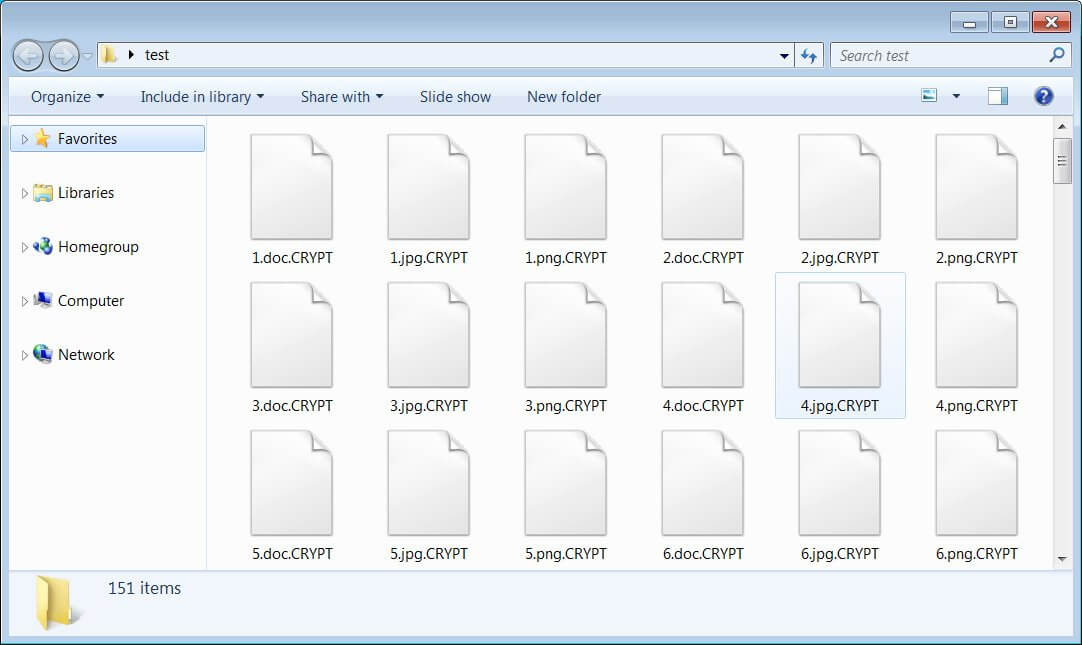
DearCry uses a combination of AES-256 and RSA-2048 encryption, and encrypted files are given the .CRYPT extension. Once encryption takes place, the inevitable ransom note is deployed, as a file called readme.txt.
Your file has been encrypted!
If you want to decrypt, please contact us.
■■■■■■■■■@airmail.cc or ■■■■■■■■■@memail.com
And please send me the following hash !
■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■
If you have a backup plan to restore the files, you can choose to ignore the attackers and carry on as usual. Nevertheless, copies of the compromised files may still remain in the hands of the hackers and could be leaked.
Bleeping Computer reported that a demand for $16,000 was made to one victim for a decryptor. However, this request is not enough to determine if $16,000 is the “market price” for DearCry attacks, or if they’re asking for even larger amounts. We can be certain of one thing, though – other ransomware groups will happily charge you greater sums, and if it proves that Microsoft Exchange exploitation is easier than RDP access, they will have no hesitation in using it.
So, if you haven’t patched your systems yet, I advise you to do so as soon as possible following Microsoft’s series of security updates and check your systems for any signs of compromise.