Data Breaches Tied to Ransomware: Look Harder
Breach Notification
,
Fraud Management & Cybercrime
,
Incident & Breach Response
Australia Regulator Says Such Breaches Are Likely Underreported

Australia’s data protection regulator says organizations hit by ransomware may be underreporting data breaches because they haven’t thoroughly figured out if data was taken.
See Also: Live Webinar | Password Management: Securing Hybrid Work for the Long Haul
That’s no excuse. The “absence of evidence” of a data breach in a ransomware attack isn’t sufficient to declare that no data was taken, says the Office of the Australian Information Commissioner.
“The nature of these attacks can make it difficult for an entity to assess what data has been accessed or exfiltrated, and because of this, we are concerned that some entities may not be reporting all eligible data breaches involving ransomware.”
The message here is” “Look harder.” But the OAIC says it in a softer way, acknowledging that evidence may be difficult to find, but that organizations also need to have the right procedures in place prior to make such detections.
“The nature of these attacks can make it difficult for an entity to assess what data has been accessed or exfiltrated, and because of this, we are concerned that some entities may not be reporting all eligible data breaches involving ransomware,” says Australian Information Commissioner and Privacy Commissioner Angelene Falk.
“We expect entities to have appropriate internal practices, procedures and systems in place to assess and respond to data breaches involving ransomware, including a clear understanding of how and where personal information is stored across their network,” she says.
The advice comes as the OAIC released its six-month roundup of reported data breaches from January through June. The number of total reported breaches fell from 530 notifications to 446 compared to the previous reporting period, which ran from July to December 2020.
Ransomware incidents, however, increased 24%, from 37 to 46. Ransomware attacks fall into a category the OAIC calls malicious or criminal attacks, which were the source of 65% of data breach incidents. Human error caused 30% of the attacks, and 5% were due to system faults.
Most of the incidents, 65%, affected 100 or fewer people, and 91% involved contact information, such as names, addresses, phone numbers or email addresses.
The healthcare industry submitted the most data breach notifications at 19%, followed by the finance sector at 13%; legal, accounting and management services at 8%; the Australian government at 8%; and the insurance industry at 8%.
Better Preparation
It’s common for organizations to say there’s no evidence that data was exfiltrated soon after an intrusion or ransomware incident.
The statement may be true at a point in time. But those statements also don’t shine a light on how hard an organization may have looked or encompass what it may have missed. The statements often become inaccurate with the passage of time if data turns up on the dark web or on a ransomware gang’s leak site.
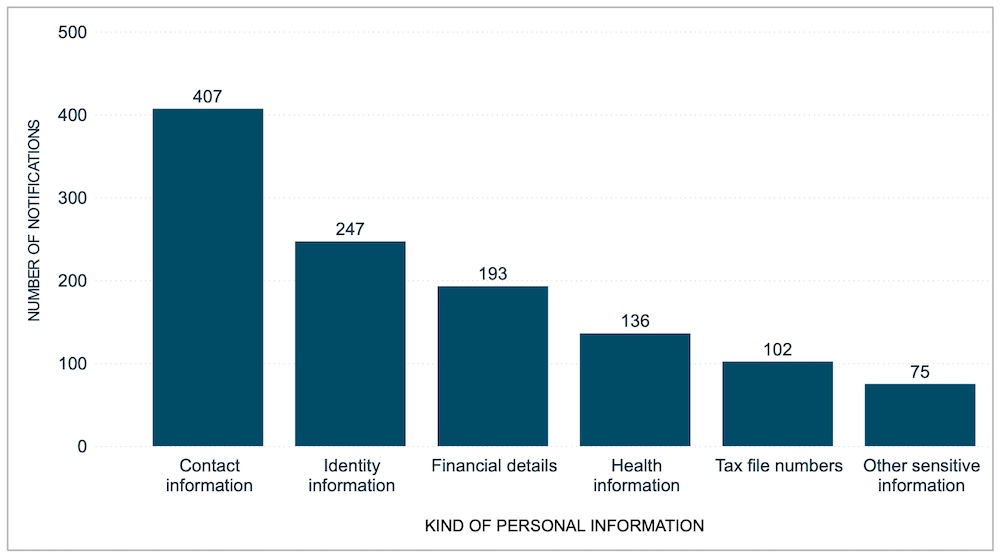
Australia’s Notifiable Data Breach scheme requires organizations that are covered by the Privacy Act to report data breaches that have a risk of causing “serious harm.” The type of data covered by the law includes personal and financial information, IP addresses and even biometric data.
Even suspected breaches trigger requirements under the law. Section 26WH of the Privacy Act requires that organizations undertake a “reasonable and expeditious assessment” of whether their breach or suspected breach may necessitate reporting under the law.
The OAIC phrased it this way in its latest report: “An assessment of a suspected data breach under section 26WH of the Privacy Act is required if there are reasonable grounds to suspect that there may have been an eligible data breach, even if there are insufficient reasonable grounds to believe that an eligible data breach has occurred.”
The law gives organizations 30 days to do the assessment. To perform what the OAIC calls a “meaningful assessment” under section 26WH, it says that organizations should be following best practices.
Those include having appropriate audit and access logs, having a backup system that’s been tested for data integrity and having an appropriate incident response plan. The law also recommends considering “engaging a cybersecurity expert at an early stage to conduct a forensic analysis if a ransomware attack occurs.”
In essence: Be better prepared for a possible data breach, and you may find what you’re looking for – and what is likely inevitable.