DarkSide’s Pipeline Ransomware Hit: Strictly Business?
Cybercrime
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Affiliate-Driven Ransomware-as-a-Service Operations Keep Generating Big Profits
“It’s not personal, Sonny. It’s strictly business.”
See Also: How IT Resilience Gaps Impact Your Business
That immortal line from “The Godfather” encapsulates the mindset of criminals who extort businesses using ransomware and other tools: It’s all about profits.
“If the group behind these attacks does mean to ‘avoid social consequences in the future,’ they should stop carrying out attacks.”
One of the gangs involved in such schemes has created a bigger than usual outcry because of its most recent target: Colonial Pipeline Co., which bills itself as being “the largest U.S. refined products pipeline system,” carrying millions of barrels of petroleum-derived fuels across the U.S. Eastern Seaboard each day.
As a result of the ransomware attack, the company says it was forced to take numerous systems offline, including billing. And it doesn’t want to supply fuel to customers again until it can bill them, which means part of the U.S. could face a temporary shortage.
We are experiencing a temporary service disruption to our corporate website, and unrelated to the ransomware. We continue to make progress on our system restart plan, and will provide an update when our website is restored.
— Colonial Pipeline (@Colpipe) May 11, 2021
President Joe Biden is promising to crack down on ransomware, and U.S. government agencies are announcing probes.
But the incident represents business as usual for ransomware-wielding extortionists. They’re searching for lucrative victims, and any organization they can attack that might result in a payday seems like fair game.
“They literally don’t even think about side effects because they don’t care. It’s a business that processes access to a company’s network into bitcoins,” says the operational security expert known as the Grugq. “The process is streamlined, polished and target-agnostic, so their primary concern is finding rich and vulnerable companies.”
Attackers don’t need nation-state backing or prowess to exploit common vulnerabilities or misconfigurations. Ransomware incident response firms say poorly secured remote desktop protocol credentials continue to be a top infection vector, as do phishing emails.
“It’s imperative that companies responsible for critical infrastructure understand that insecure systems present a juicy ransomware target to the cybercriminal underground, and proactive defenses will go a long way in preventing future incidents like what happened with Colonial Pipeline,” according to security firm Intel 471.
Gangs Seek Victims Who Pay
So long as victims continue to pay, and perpetrators remain free – potentially because they’re operating from Eastern Europe and local authorities look the other way, so long as no domestic targets get hit – why would any criminal refrain from doubling down on what has been an extremely lucrative scheme?
In the case of the Colonial Pipeline attack, the FBI reports that perpetrators used a ransomware strain called DarkSide. The gang behind DarkSide appeared in the latter half of 2020, announcing the launch of its ransomware-as-a-service affiliate program last November.
“Darkside is aiming for big targets,” Victoria Kivilevich, a threat intelligence analyst at Israeli threat intelligence firm Kela, said at the time.
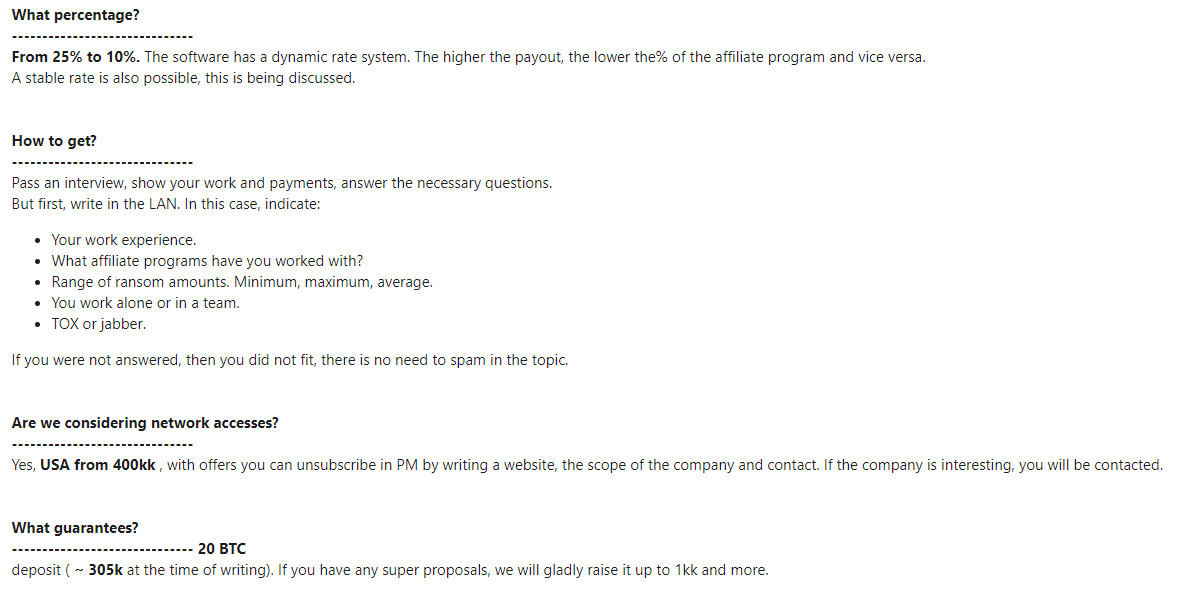
RaaS programs involve operators developing and updating crypto-locking malware and providing it to vetted affiliates who infect targets. Every time a victim pays, the affiliate shares profits with the operator. Last November, Kivilevich reported that DarkSide affiliates were paid 10% to 25% of every haul, “depending on the size of the ransom.”
The downside of affiliate programs, however, is that if an affiliate does something bad, then it can affect the gang’s reputation.
The Upsides of Affiliates
But many gangs – including those that specialize in “big game hunting,” meaning taking down bigger targets to earn bigger payoffs – continue to embrace the affiliate model because it has been very lucrative, allowing both operators and attackers to specialize in what they do best. Many operators also give affiliates the ability to automatically upload stolen data to a dedicated data leak site as proof that the victim got hit. Some criminals threaten to leak mass quantities of data unless a ransom is paid. And some ransomware operators also provide dedicated “customer support” teams to negotiate with victims, help them acquire cryptocurrency and generally smooth the way for victims to pay a ransom.
The DarkSide gang has continued to refine the affiliate model, including debuting a fresh version in March with a range of new features. Among those: the ability to target both Windows and Linux systems, improved encryption, on-demand distributed denial-of-service attacks against targets as well as a “management panel that enabled affiliates to arrange calls meant to pressure victims into paying ransoms,” Intel 471 says.
“They have taken the ‘service’ part of their affiliate program to a new level,” says Andrey Yakovlev, a security researcher at threat intelligence firm IntSights. “They have service phone numbers, a ticketing system and they actively ask press and recovery companies to engage with them.”
Some ransomware-wielding gangs have apologized for hitting hospitals during the ongoing COVID-19 pandemic and promised free decryptors to help undo the damage – but that’s just spin.
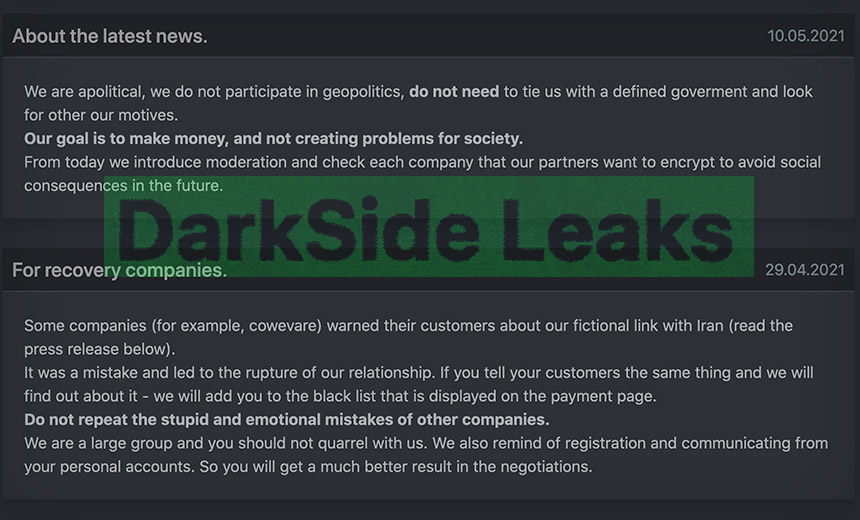
Here’s what the DarkSide gang said about its hit against Colonial Pipeline: “We are apolitical, we do not participate in geopolitics.” The gang said this in a statement released via its data leak site on Monday. It also decried any attempts “to tie us with a defined government and look for our other motives,” noting that “our goal is to make money, and not creating problems for society.” Accordingly, the gang claimed that it would vet all future victims to avoid critical infrastructure getting hit in the future.
“This is not the first time DarkSide operators have tried to put a PR spin on their actions,” notes cybersecurity firm Intel 471. Last year, for example, the gang promised to donate a percentage of the ransom payments it received to two charities – Children International and The Water Project. Whether this came to pass remains unclear (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
Gangs’ Talk Is Cheap
If they’re so concerned with not disrupting healthcare, there’s an obvious course of action for these individuals to pursue – don’t wield ransomware, says cybersecurity expert Brian Honan, who heads consultancy BH Consulting in Dublin.
“I would not put much stock into this statement by those allegedly behind this attack,” he says. “Those behind these type of attacks have indiscriminately impacted many other organizations such as hospitals, universities, town councils and other organizations who because of their nature may not have a lot of money to spend on security.”
Honan adds: “If the group behind these attacks does mean to ‘avoid social consequences in the future,’ they should stop carrying out attacks.”
Opportunists at Work
If this had been the latest installment in the venerable “Die Hard” franchise, anti-American, ransomware-wielding attackers would have focused on a major U.S. pipeline to wreak havoc.
But ransomware gangs don’t work that way. While many ransomware gangs may have no love for the West, criminals’ MO is to find the quickest and easiest way to safely steal as much as possible.
“Ransomware is really a business model,” says Sam Curry, CSO at Cybereason. “The reason it’s growing is because people make money at it, and they make a lot of money. They’re targeting the sectors that are most likely to pay.”
Attackers need not be overly choosey about who they hit. “I’d not even be surprised if the majority of ransomware operators … even know what it is the company they’re ransoming does,” says security expert Marcus Hutchins, aka MalwareTech. “It’d be a lot easier if they did in fact set out to hold an oil pipeline hostage, because that’d open up more options to respond.”
Some supposed ransomware attacks have been tied to nation-state attackers. WannaCry, for example, appears to have been developed by North Korea, but it got out of control. NotPetya, meanwhile, was pseudo-ransomware, in that the destructive malware pretended to give victims the ability to pay to restore their data, when in fact the malware wiped every system it touched. But those attacks are outliers.
They literally don’t even think about side effects because they don’t care. It’s a business that processes access to a company’s network into bitcoins. The process is streamlined, polished and target agnostic, so their primary concern is finding rich and vulnerable companies. https://t.co/OF34EsGvBt
— thaddeus e. grugq (@thegrugq) May 11, 2021
But with the DarkSide hit against Colonial Pipeline, rather than the Russian government controlling target selection, “whoops is more likely,” the Grugq says. “Do you know that the billing system is critical to normal operating of 45% of the East Coast’s oil and gas critical national infrastructure? Because I doubt some idiots with an RDP scanner in Siberia knew it.”
Managing Editor Scott Ferguson contributed to this blog.