Cyber Extortion Thriving Thanks to Accellion FTA Hits
Cybercrime
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Coveware: Average Ransom Payment Hits $220,298, Presaging More Supply Chain Attacks
The zero-day attacks against Accellion File Transfer Appliance users have rewritten the rules of the cyber extortion game, adding a new supply chain trick to ransomware gangs’ arsenal that they’re sure to repeat.
See Also: Live Webinar | Empowering Financial Services with a Secure Data Path From Endpoint to Cloud
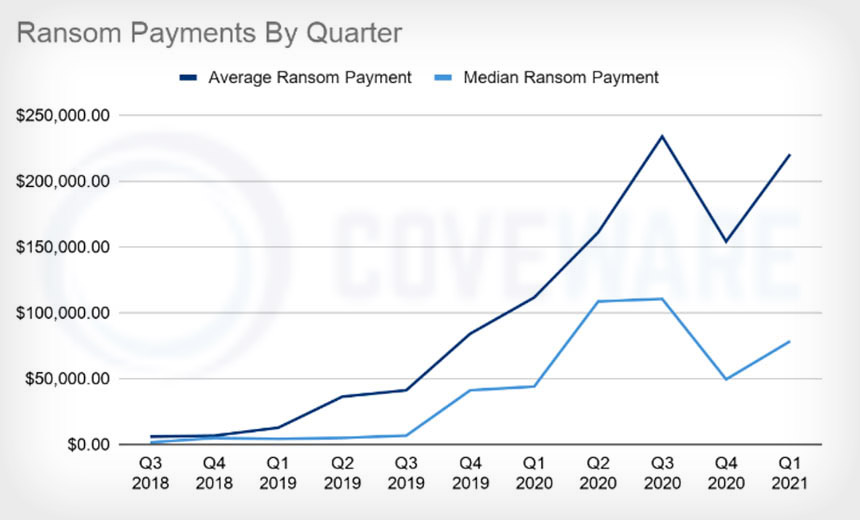
Proof of success comes in the form of illicit revenue. In the first quarter of this year, the average cyber extortion payoff reached $220,298, a 43% increase from the previous quarter, ransomware incident response firm Coveware reports, based on thousands of cases it’s helped investigate.
“We have yet to encounter an example where paying a cybercriminal to suppress stolen data helped the victim mitigate liability or avoid business or brand damage.”
That marks an unwelcome reversal: From Q3 to Q4 of last year, the average ransom paid by victims declined (see: Ransomware: Average Ransom Payment Declines to $154,108).
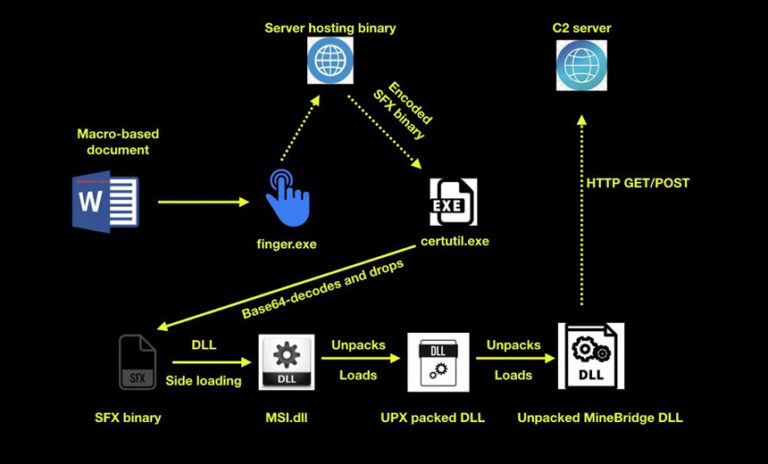
Coveware says the recent increase is largely due to the Clop gang getting its hands on data stolen via the Accellion FTA zero-day attacks in January and last December (see: Accellion Holdouts Get Legacy File Transfer Appliance Blues).
In those attacks, someone dedicated time and resources to reverse-engineer the nearly 20-year-old FTA code, through which they discovered two sets of vulnerabilities. Attackers then ran two campaigns that stole data being stored on FTA appliances. Victims included security firm Qualys, Flagstar Bank, Australia’s Transport for New South Wales, Canada’s Bombardier, the Reserve Bank of New Zealand, U.S. grocery chain Kroger, energy giant Shell and several U.S. health plans, among many others.
The relationship between Clop and whoever developed the attacks remains unclear. “The Clop group may have purchased the exploit used in the initial stages of the attack so as to have exclusive use,” Coveware says.
From a ransomware operation standpoint, the attack campaign is somewhat unusual in that Clop only gained the data and the ability to extort victims by threatening to release the data, rather than the ability to crypto-lock systems. In addition, relatively few organizations used FTA.
But the FTA attacks appear to have been a massive criminal success. “Clop’s confidence that such a small number of targets would yield a positive financial return must have been high, and, unfortunately, they were correct. Dozens of Clop victims were extorted for tens of millions of dollars even though the majority of the victims opted not to pay and were subsequently doxed on the Clop leak site,” Coveware says.
Clop’s shakedown of Accellion victims appeared to end earlier this month, with the gang returning to more conventional tactics.
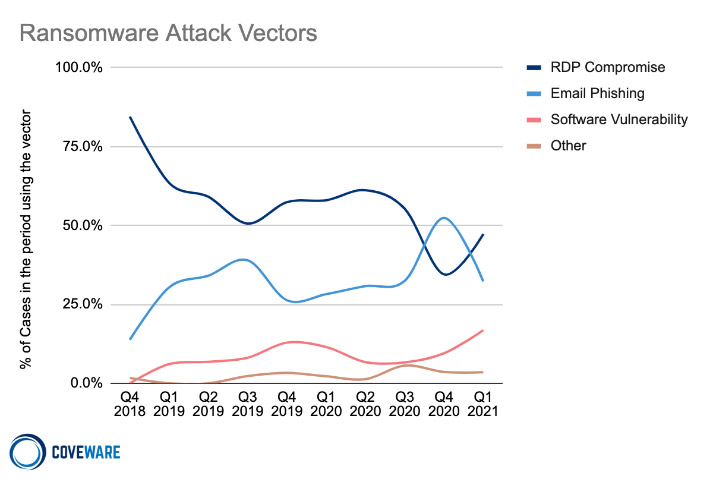
Top Attack Vectors: RDP and Phishing
Meanwhile, exploiting weak or poorly secured remote desktop protocol credentials and phishing remain the two most common tactics that gangs use to get crypto-locking code onto victims’ systems, Coveware says.
“RDP remains a frustratingly common vulnerability despite well-known, secure remote connection best practices,” Coveware notes (see: Ransomware Gangs’ Not-So-Secret Attack Vector: RDP Exploits). “Phishing emails that install credential-stealing malware or a remote access Trojan also remain a common attack vector.”
In both cases, enforcing least-privilege access controls, as well as using two-factor authentication wherever possible, “can easily limit the ability of an attacker to escalate privileges beyond the initially compromised machine,” Coveware says.
Target: Flaws in Widely Used Software
In recent months, some gangs – including Sodinokibi and Lockbit – have focused more on exploiting software vulnerabilities, including flaws that organizations have not yet patched in Fortinet and Pulse Secure VPN appliances, Coveware says.
The ability of a smaller gang such as Lockbit to carry out those types of attacks demonstrates the evolving cybercrime-as-a-service economy, in which initial access brokers can target known vulnerabilities that organizations have yet to patch, gain initial access to an organization and then resell this access to others (see: Initial Access Brokers: Credential Glut Weakening Prices?).
“It is likely that the actual RaaS operators and affiliates were not the party that achieved network access via these vulnerabilities, but rather specialist actors that harvest network credentials and are specifically trained to mass scan for vulnerable IP addresses,” Coveware says. “These specialists then resell network access to ransomware affiliates who use the access to stage the extortion phase of the attack.”
Competition Intensifies
Some ransomware gangs run their own attacks, but many operations now function using a ransomware-as-a-service model, in which operators develop code and infrastructure and affiliates infect victims. For every victim who pays, the operator and affiliate split the profits, with affiliates often keeping 60% to 70%. Experts say this division of labor has helped RaaS operations maximize profits – especially if they can recruit highly skilled affiliates.
The type of ransomware most encountered by victims assisted by Coveware in Q1 was Sodinokibi, aka REvil, followed by Conti, Lockbit, Clop and Egregor. All are prolific RaaS operations.
But competition remains fierce between RaaS operations as they attempt to recruit top affiliates to maximize their paydays, including via big game hunting, which is hitting larger victims for the prospect of bigger ransom returns.
Seeking fresh avenues for finding new victims, some RaaS operations have begun running campaigns using malware written to crypto-lock Unix and Linux systems. Defray777, Mespinoza, Babuk, Nephilim and Darkside have already deployed such code, and Sodinokibi suggests it will do so, Coveware says. Unfortunately, code quality can be variable, and it’s likely that many early waves of attacks will result in encryptors incorrectly encrypting data, thus leaving it unrecoverable, as well as decryptors failing to restore encrypted data 100% of the time.
Missteps Common
Increased competition has had a number of business repercussions for ransomware enterprises, as have some business decisions, technical missteps and other mishaps.
- Egregor: The gang announced that it was shutting down “only four months after taking the torch from the Maze group.” In February, individuals suspected of providing hacking, logistical and financial support to the RaaS operation were arrested in Ukraine.
- Netwalker: Law enforcement officials disrupted the operation in January, shuttering the infrastructure and arresting suspected affiliates.
- Conti: Coveware says the Conti gang’s decision to outsource chat operations complicated efforts by victims to recover systems or conduct negotiations. The gang also has gained a reputation for re-attacking victims, which remains “at odds with a RaaS organization interested in maintaining a reputation that compels victims to pay a ransom.”
- Lockbit: Like Conti, Lockbit has a reputation for repeat attacks against victims, and recently, flaws in its crypto-locking code left some victims’ data unrecoverable (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
- Sodinokibi: In some of the RaaS operation’s attacks, “technical flaws resulted in victims unable to match encryption keys, resulting in total data loss,” Coveware reports.
- Black Kingdom: Operators attempted to install web shells on numerous Exchange servers, “but flaws in their encryption led to permanent data loss,” Coveware says.
Stealing Data: De Rigueur Tactic
Gangs have been seeing their profits increase thanks, in part, to ongoing innovation. In November 2019, for example, the now-defunct Maze gang pioneered the practice of stealing data before crypto-locking systems and threatening to leak the stolen data if victims didn’t pay. By leaking the data if they didn’t receive a ransom, the gang also demonstrated the threat posed to future victims.
Numerous ransomware gangs have now launched dedicated data leak sites, where they attempt to name and shame victims and post extracts of stolen data.
Coveware says that 77% of all ransomware attacks now include a threat to leak stolen data, up from 67% in Q4 of 2020. But while such threats might have become the typical boilerplate included by gangs in their ransom notes, not all gangs steal data – or at least not in every attack. When they do, furthermore, the data may have little or no value because gangs don’t appear to have the time or inclination to go hunting for anyone’s crown jewels.
“Most RaaS affiliates purchase network access and use stolen data solely as additional leverage against the victim,” Coveware says. “This means that despite the threats, threat actors rarely take the time to steal data that any other criminals or interested parties would want to purchase. The stolen data is just proof that the attack occurred and sometimes creates legal obligations for the victim.”
Don’t Pay for Promise to Delete Data
Security experts and law enforcement agencies recommend that victims never pay a ransom, because doing so validates ransomware as a criminal profit-making enterprise.
Even when some organizations have full backups, allowing for complete data restoration without having to pay a ransom, they still pay in exchange for a promise from the gang that it will delete stolen data.
Trusting such promises, however, is a fool’s errand. “Over hundreds of cases, we have yet to encounter an example where paying a cybercriminal to suppress stolen data helped the victim mitigate liability or avoid business or brand damage,” Coveware says. “On the contrary, paying creates a false sense of security, unintended consequences and future liabilities.”