Crypto malware LemonDuck targeting Windows, Linux devices | #microsoft | #hacking | #cybersecurity | #cybersecurity | #infosecurity | #hacker | National Cyber Security
LemonDuck was first discovered in China in 2019 as a cryptocurrency botnet that used affected systems for Monero mining.
According to a new report from Microsoft 365 Defender Threat Intelligence Team, a revamped version of LemonDuck crypto-mining malware is now targeting Windows and Linux devices.
The malware lets threat actors insert backdoors, steal credentials, and conduct a range of malicious activities on the infected systems. This malware is spread via exploits, phishing emails, USB devices, and brute force attacks in different countries.
“LemonDuck’s threat to enterprises is also in the fact that it’s a cross-platform threat. It’s one of a few documented bot malware families that target Linux systems as well as Windows devices,” warned Microsoft.
Malware Can Use New Exploits
According to researchers, the threat actors behind LemonDuck malware can take advantage of new exploits almost immediately and effectively run scam campaigns. For instance, they used COVID-19 themed lures in email-based attacks in 2020. This year, they are keen on exploiting MS Exchange Server flaws to access unpatched systems.
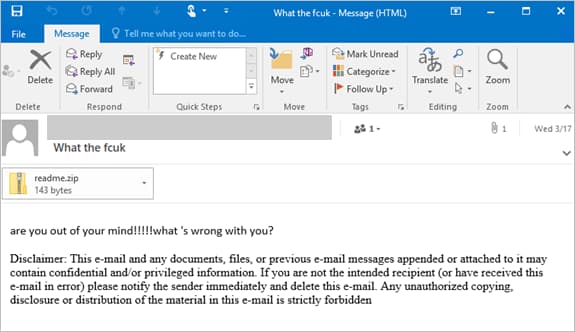
Lemonduck’s email sample (Image: Microsoft)
SEE: ElectroRat crypto-stealing malware hits MacOS, Windows, Linux devices
LemonDuck is currently targeting users in China, but it is quickly expanding its malicious activities to the USA, Germany, the UK, France, Russia, India, Korea, Vietnam, and Canada.
Evolution of LemonDuck
LemonDuck was first discovered in China in 2019 as a cryptocurrency botnet that used affected systems for Monero mining. However, it has considerably evolved and has become a highly sophisticated malware strain, Microsoft researchers said in a blog post.
Furthermore, the malware activities aren’t limited to crypto mining anymore as it can effortlessly carry out serious security breaches on vulnerable systems. Some of the new features added to LemonDuck over time include backdooring, key credentials theft, disabling security controls, spreading through phishing emails, and making computers vulnerable to new attacks.
Its capability of targeting both Windows and Linux machines has made it more dangerous than other malware strains out there.
Lemonduck’s attack chain (Image: Microsoft)
LemonDuck also exploits old vulnerabilities
Interestingly, apart from using new exploits, LemonDuck can successfully exploit old flaws and helps attackers remain undetected. Microsoft has observed that LemonDuck is regularly exploiting the following security vulnerabilities.
CVE-2019-0708 (BlueKeep)
CVE-2017-0144 (EternalBlue)
CVE-2020-0796 (SMBGhost)
CVE-2017-8464 (LNK RCE)
CVE-2021-27065 (ProxyLogon)
CVE-2021-26855 (ProxyLogon)
CVE-2021-26857 (ProxyLogon)
CVE-2021-26858 (ProxyLogon)
“Notably, LemonDuck removes other attackers from a compromised device by getting rid of competing malware and preventing any new infections by patching the same vulnerabilities it used to gain access,” researchers wrote.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.