‘Black Kingdom’ Ransomware Hits Unpatched Exchange Servers
Email Security & Protection
,
Endpoint Security
,
Fraud Management & Cybercrime
Attack Code ‘Rudimentary and Amateurish’ but Still a Threat
Attackers gunning for an easy payday are continuing to target Microsoft Exchange servers that have not yet been updated with critical patches.
See Also: Top 50 Security Threats
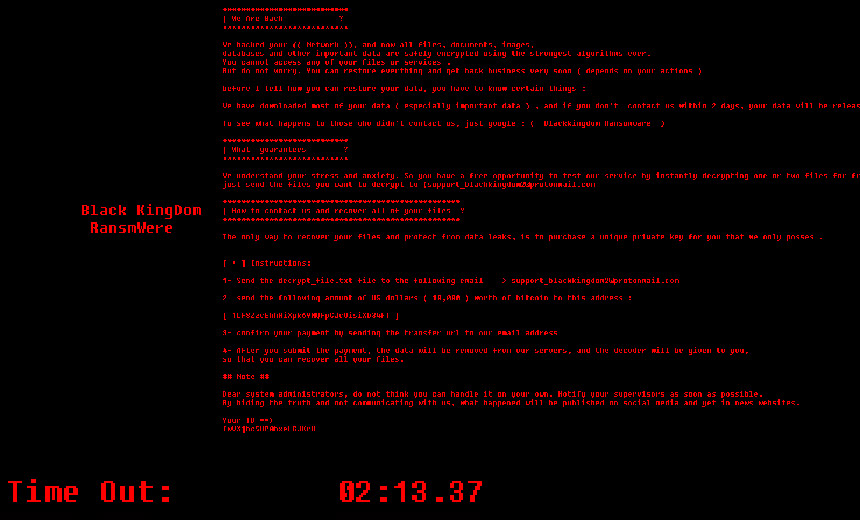
On March 18, security experts began warning that a new strain of ransomware had begun targeting Exchange email servers that have not yet been updated with the patch Microsoft issued on March 2 for a ProxyLogon flaw in Exchange.
The new crypto-locking malware, called Black Kingdom, has been branded “rudimentary and amateurish” by Mark Loman, director of engineering at security firm Sophos, who says it appears to have been dashed off by a “motivated script-kiddie.”
Black Kingdom may rank as a minor problem facing organizations that have yet to install the security patches to fix four critical flaws, issued by Microsoft early this month, for all on-premises versions of Exchange.
Security firms have warned of a surge in attack attempts – and thousands of victims – as more than a dozen groups have already been targeting the flaws, with some doing so as early as January – before the vulnerabilities were public knowledge. As a result, even once organizations have patched the flaws, they must still review their infrastructure for signs that they had already been compromised (see: Microsoft Exchange: Server Attack Attempts Skyrocket).
Last week, security firm RiskIQ estimated that more than 450,000 on-premises Exchange servers remained unpatched, and the majority were located in the U.S.
Referencing more recent scans by RiskIQ, Microsoft says more organizations have installed the Exchange security updates over the past week, although as of Sunday, at least 29,000 on-premises Exchange mail servers remained unpatched.
After proof-of-concept exploits for the flaws were released beginning on March 13, security firm F-Secure reported that the number of attackers attempting to use them to plant web shells on unpatched Exchange systems soared.
Enter Black Kingdom
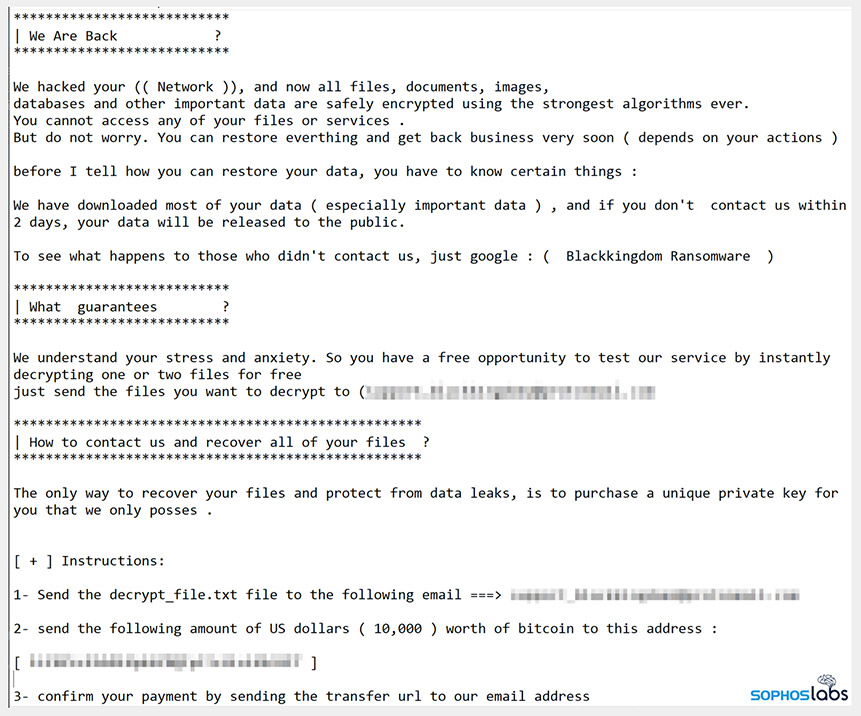
Black Kingdom is the latest attempt by attackers to target the Exchange flaws – and in particular, the ProxyLogon flaw designated CVE-2021-26855, which can be used to remotely execute code.
While the ransomware didn’t seem to work correctly when it first appeared, in recent days, several security firms – including Arete, Sophos and SpearTip – report that the developer has continued to refine the code, which can now crypto-lock systems.
The attack campaign appears to have notched up at least one victim, who on Thursday paid a ransom in bitcoins worth about $9,400.
Threat intelligence vendor Recorded Future’s news site The Record also reports that at least one automotive supplier appears to have fallen victim to a Black Kingdom infection and is remediating the attack.
“The encryption tools and techniques are imperfect but the ransom of $10,000 in bitcoins is low enough to be successful,” Loman says. “Every threat should be taken seriously, even seemingly low-quality ones.”
We have recovered and analyzed the source code from the Black Kingdom ransomware! Since last Thursday, this has hit many Exchange servers still vulnerable to #ProxyLogon exploits. The ransomware has the hallmarks of a motivated script-kiddie: https://t.co/9DNMWUhEtb #blackkingdom pic.twitter.com/7QAOTjkC7X
— Mark Loman @ (@markloman) March 24, 2021
Loman recently described another low-quality attack attempt called DearCry, noting that numerous aspects of that ransomware “suggest that DearCry may be a prototype, possibly rushed into use to seize the opportunity presented by the Microsoft Exchange Server vulnerabilities, or created by less experienced developers.” (See: Rushed to Market: DearCry Ransomware Targeting Exchange Bug)
Loman notes in a detailed technical teardown of Black Kingdom based on the attack chain seen by Sophos that if the attack successfully exploited the ProxyLogon flaw to gain access to the server, “the adversary delivered a webshell,” which “offers remote access to the server and allows the execution of arbitrary commands,” After that, the attacker used PowerShell to download a ransomware executable – written in Python – from an external address and then ran a script.
“The script executes the ransomware by invoking Win32_Process via WMI – the Windows Management Interface. The script includes the ability to upload the ransomware to other computers on the network and execute it,” Loman says.
The ransomware makes a number of mistakes, Loman says, including failing to check if a system has already been crypto-locked before attempting to encrypt it.
“As a result, the encrypted files can become encrypted multiple times over, even by the same ransomware, making decryption extremely complicated,” he says. “This oversight is probably unintentional, but could have been anticipated.”
Ransomware Revised in Recent Days
In fact, malware researcher Marcus Hutchins, aka MalwareTech, says that as of Sunday, coding errors meant that Black Kingdom wasn’t able to crypto-lock systems, but only to drop a ransom note. As a result, it previously functioned not as ransomware, but just as scareware.
Hutchins says the attacker attempted to execute a Python script, which, if executed, claimed that files had been stolen, when they had not. “Seems to be total skidware and it’s unclear how many systems it successfully ran on, if any,” he tweeted.
The executable is py2exe, and if run successfully looks like this. Seems to be total skidware and it’s unclear how many systems it successfully ran on, if any. pic.twitter.com/CcvRsBjbbf
— MalwareTech (@MalwareTechBlog) March 21, 2021
But in recent days, Black Kingdom’s developer appears to have added working crypto-locking functionality – albeit imperfectly.
Kevin Beaumont, a security researcher at Microsoft, reported Tuesday that a newer version of Black Kingdom had begun inexpertly crypto-locking too many file types – such as storage drivers, which can leave infected systems unable to reboot. As a result, victims wouldn’t be able to access any ransom note, meaning there would be no possibility of a payday for attackers.
BlackKingdom ransomware on my personal servers. It does indeed encrypt files. They exclude c:windows, however my storage drivers were in a different folder and it encrypted those… meaning the server doesn’t boot any more. If you’re reading BlackKingdom, exclude *.sys files pic.twitter.com/nUVUJTbcGO
— Kevin Beaumont (@GossiTheDog) March 23, 2021
Previous Black Kingdom Targeted Pulse Secure
An earlier version of ransomware called Black Kingdom was spotted in June 2020 by Poland-based cybersecurity firm Redteam.PL, which said it had discovered the malicious code was targeting Pulse Secure VPNs that hadn’t been patched to fix an arbitrary file-reading vulnerability, designated CVE-2019-11510 (see: Ransomware: Beware of 13 Tactics, Tools and Procedures).
The attackers were demanding about $10,000 worth of bitcoins and claimed they’d leave a victim’s data unrecoverable if the ransomware wasn’t paid within 600 minutes, SecurityWeek reported at the time.
Other attack groups had already been targeting the Pulse Secure flaw long before Black Kingdom debuted, beginning in August 2019, before expanding in January 2020 to include the notorious Sodinokibi – aka REvil – ransomware-as-a-service operation (see: Patch or Perish: VPN Servers Hit by Ransomware Attackers).
Security firm SpearPoint notes that the previous ransomware named Black Kingdom also packaged the malicious executable in a Python script.
Experts Urge: Patch or Disconnect Servers
Sophos’ Loman says the two strains of ransomware sharing the same name may, of course, be related.
For all organizations running Microsoft Exchange servers on-premises, however, the immediate imperative isn’t attribution, but rather to patch the four critical flaws and then continuously monitor the infrastructure for signs it was already compromised.
“Defenders should take urgent steps to install Microsoft’s patches to prevent exploitation of their Exchange server,” Loman says. “In addition, the Exchange server should be scanned for web shells that allow attackers to run commands on the server. If this is not possible, the server should be disconnected from the internet or closely monitored by a threat response team.”
Our work continues, but we are seeing strong momentum for on-premises Exchange Server updates:
• 92% of worldwide Exchange IPs are now patched or mitigated.
• 43% improvement worldwide in the last week. pic.twitter.com/YhgpnMdlOX— Security Response (@msftsecresponse) March 22, 2021





