Beware Phishing Attacks with Open Redirect Links | #emailsecurity | #phishing | #ransomware | #cybersecurity | #infosecurity | #hacker | National Cyber Security
Microsoft is warning of a “widespread” phishing campaign in which fraudsters use open redirect links to lure users to malicious websites to harvest Office 365 and other credentials, according to a recent research report published by the software company.
See Also: Automating Security Operations
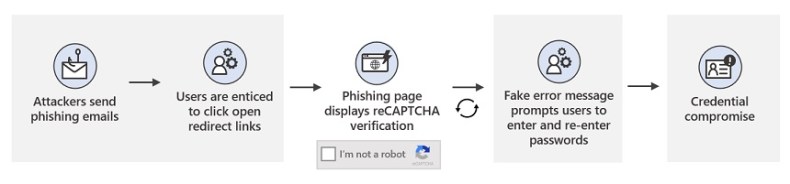
Besides using social engineering techniques that impersonate well-known productivity tools and services to lure users into clicking, the fraudsters will sometimes deploy a malicious CAPTCHA verification page that helps lure users to a phishing site that will harvest their credentials, according to Microsoft.
The main feature of this campaign, however, is the use of open redirect links that can trick users into clicking a malicious link and help the fraudsters avoid certain security tools, such as email gateways, the Microsoft researchers say.
Open redirects are a common feature in sales and marketing email campaigns that can direct customers to specific landing pages while tracking click rates and other metrics. In this case, however, the fraudsters use the links to dupe users into visiting a phishing page, Microsoft notes.
“Attackers could abuse open redirects to link to a URL in a trusted domain and embed the eventual final malicious URL as a parameter. Such abuse may prevent users and security solutions from quickly recognizing possible malicious intent,” according to Microsoft. “For instance, users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it.”
And while Microsoft notes that this particular campaign is widespread, the company did not specify how many attacks it has detected. Examples from the research show that some of the phishing emails date to January, and Microsoft says that the campaign was still active as of this month.
Phishing Emails
As part of this attack, Microsoft’s researchers found that the fraudsters use a wide variety of sender domains to avoid detection. The report notes the attackers have used over 350 unique domains to date, including free email domains from numerous country code top-level domains, compromised legitimate domains and attacker-owned, domain-generated algorithm domains.
The fraudsters also use various subject lines in the phishing emails as part of their social engineering techniques. These include notifications to reset passwords or alerts for a Zoom meeting, according to the report.
Embedded in the emails is a malicious link that is designed to take the user to a landing page controlled by the fraudsters and designed to harvest credentials. In this case, however, the attackers use the open redirect links to disguise the lure, Microsoft notes.
“Since the actors set up open redirect links using a legitimate service, users see a legitimate domain name that is likely associated with a company they know and trust. We believe that attackers abuse this open and reputable platform to attempt evading detection while redirecting potential victims to phishing sites,” according to the Microsoft researchers.
Layers of Legitimacy
In some cases during this campaign, a user will click the redirect link, which opens a fake CAPTCHA site that they must fill out. This request helps give the campaign an added layer of legitimacy, according to Microsoft.
Once the victim completes the fake CAPTCHA page, the user is then sent to a malicious domain designed to look like a legitimate Office 365 or another login website.
“The site is prepopulated with the recipient’s email address to add legitimacy to the request. This technique leverages familiar single sign-on (SSO) behavior to trick users into keying incorporate credentials or other credentials associated with the email address,” according to the report.
The phishing domain will also ask users to input their credentials twice, ensuring that the fraudsters collect the right username and password combinations. Once the user enters their password a second time, the page directs to a legitimate Sophos website that claims the email message has been released, adding yet another layer of legitimacy to the attack, Microsoft notes.
Other Attacks
Earlier this month, Microsoft warned of a yearlong phishing campaign that used various techniques, including deploying Morse code in some cases, to help evade security tools while attempting to harvest the credentials of Office 365 users (see: Microsoft Details Yearlong Office 365 Phishing Campaign).
In addition, security firms such as Proofpoint and INKY have warned of an uptick in phishing emails that use information about COVID-19 and the Delta variant as a potential lure (see: Phishing Attack Used Spoofed COVID-19 Vaccination Forms).