Behind the Scenes of a BEC Attack
Business Email Compromise (BEC)
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Microsoft 365 Defender Research Team Describes Flow of Attack
The Microsoft 365 Defender research team says it has “disrupted a large-scale BEC infrastructure hosted in multiple web services.”
See Also: Live Webinar: Seeking Success by Adopting a SASE Architecture: en el idioma Español
In a Monday blog post, the team describes in detail the business email compromise attack flow, from the initial credential theft to stealing data, including financial transaction details, using email forwarding rules.
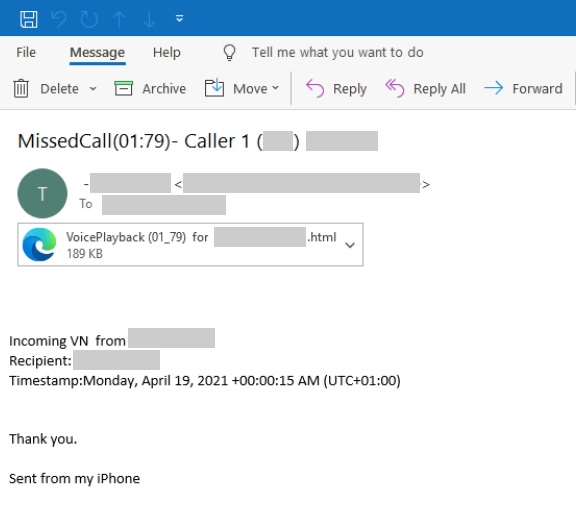
The attackers’ campaign started with phishing emails, which originated from a cloud provider’s address and contained a voice message lure and an HTML attachment.
The HTML attachment contained JavaScript that imitated the Microsoft sign-in page, with the username already populated. When a victim entered a password, they were shown a “file not found” message, while in the background, JavaScript transmitted the credentials to the attackers via a redirector, which was also hosted by a cloud provider, the researchers found.
The attackers then added forwarding rules and gained access to the victims’ emails about financial transactions, the researchers add.
The attackers used the cloud-based infrastructure to automate their operations at scale, including adding rules, watching and monitoring compromised mailboxes, identifying which victims to target and dealing with the forwarded emails, the Microsoft research report says.
“The attackers performed discrete activities for different IPs and timeframes, making it harder for researchers to correlate seemingly disparate activities as a single operation,” according to the report.
“The use of multiple IP addresses simultaneously was an attempt to hide the attack from automated tools,” says Evgeny Gnedin, head of information security analytics at Positive Technologies, a Moscow-based cybersecurity firm. “Such tricks are used not only in BEC attacks, but also in others, including attacks on web applications.”
To help mitigate the risk of such attacks, Gnedin recommends using sandboxes to check for suspicious attachments. Even in the absence of a signature at the time of a scan by antivirus software, sandboxes can help identify malicious activity, he adds.
Microsoft recommends Office 365 users deploy advanced pre-breach and post-breach protection tools with capabilities such as a multilayered email filtering stack with edge protection, sender intelligence, content filtering and post-delivery protection. Plus, it says external email forwarding should be kept as disabled – the default – and users should reduce or disable the use of legacy protocols such as POP3/IMAP. Microsoft also recommends enabling multifactor authentication for all Office 365 users.
Blending In
The attackers set up DNS records that were similar to company domains, which allowed their activities to blend into existing email conversations, the Microsoft researchers say.
Although multifactor authentication can block malicious actors from signing into email accounts, the attackers in this case used legacy protocols, such as IMAP/POP3, to circumvent MFA and exfiltrate emails, the Microsoft researchers say.
Microsoft researchers say that while the attackers took steps to avoid analysts connecting their activities to one operation, there were common elements. For example, the attacks all used “credentials checks with user agent ‘BAV2ROPC’, which is likely a code base using legacy protocols like IMAP/POP3, against Exchange Online. This results in an ROPC OAuth flow, which returns an ‘invalid_grant’ in case MFA is enabled, so no MFA notification is sent,” the researchers say. Microsoft advises against using Resource Owner Password Credentials, or ROPCs, which allow an application to sign in the user by directly handling their password.
Cloud Services Alerted
Microsoft did not respond to Information Security Media Group’s request for details on the identity of the attackers, extent of damage and losses incurred.
But the researchers note in their report that they worked with the Microsoft Threat Intelligence Center to report the findings to the security teams at the cloud services the attackers leveraged, who suspended the offending accounts, resulting in the takedown of the infrastructure (see: Microsoft Exchange Flaw: Attacks Surge After Code Published).
The monetary losses from BEC surged to about $1.8 billion in 2020, according to IC3, the FBI’s central repository for the collection of internet crime complaints.
Gartner predicts that losses due to BEC attacks will continue to double each year, hitting over $5 billion by 2023.





