Azure Cosmos DB remote takeover bug affects thousands of organisations – Security
Security researchers have found a long-standing vulnerability in the Azure Cosmos DB fully managed non-structured query language database, which allows attackers to remotely take over the information store with a trivial exploit.
Named ChaosDB, the vulnerability gives any Azure user full administrative access to other customers’ Cosmos DB instances, security vendor Wiz Research Team said.
This includes the ability to read, write and delete data in the NoSQL information store, with no authorisation required.
Wiz said the vulnerability impacts thousands of organisations, including several large Fortune 500 companies.
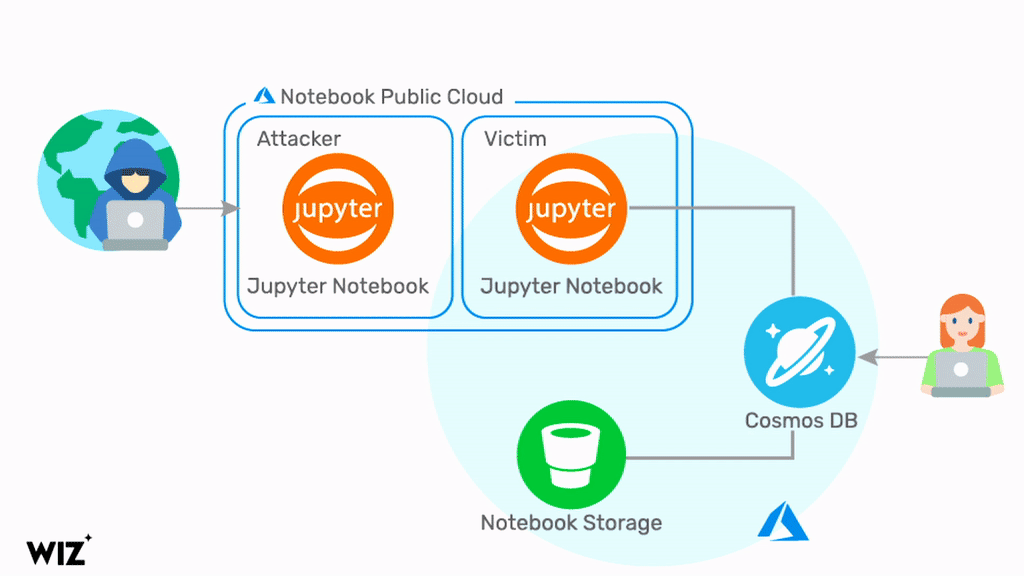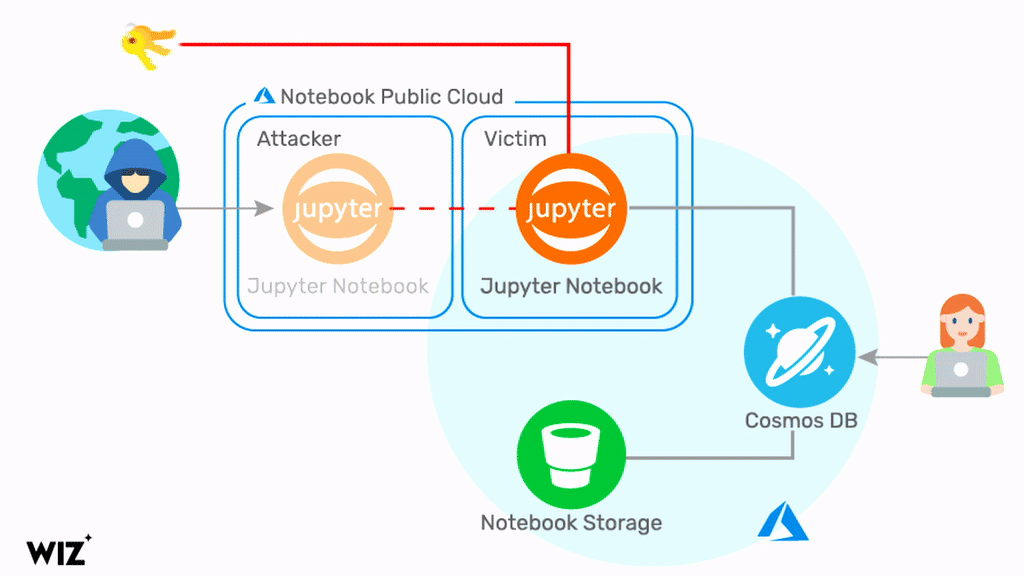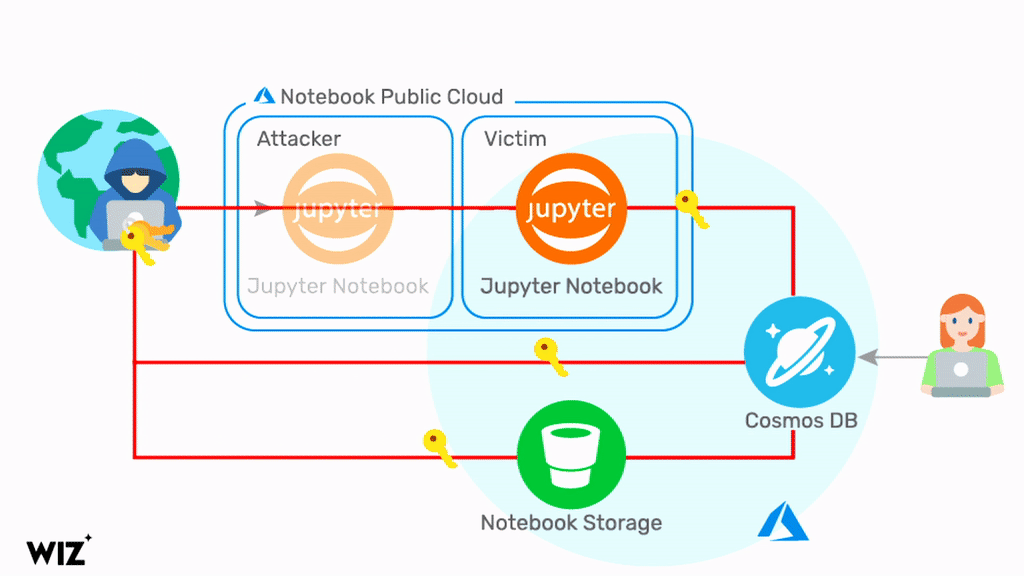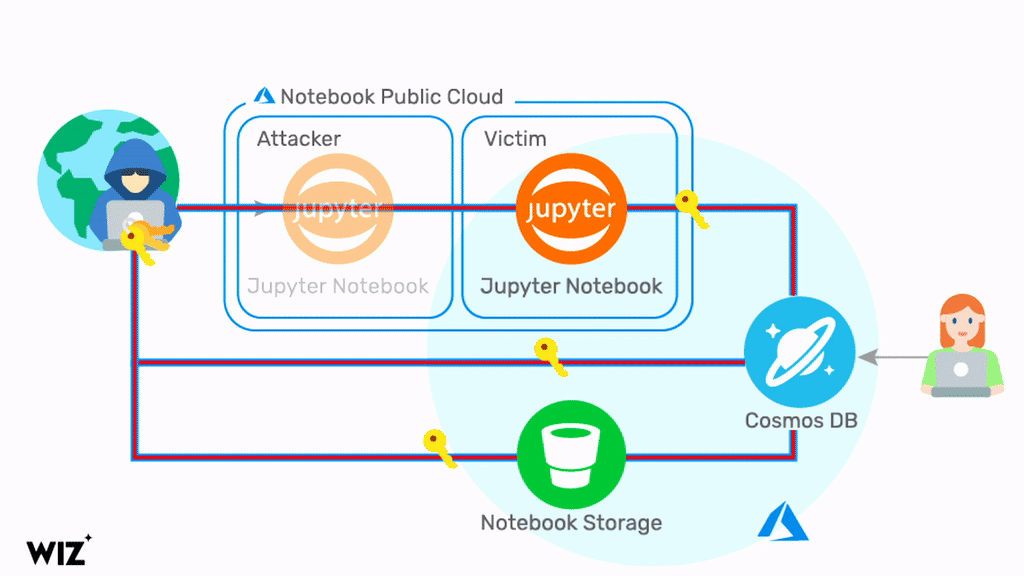
The vulnerability stems from the Jupyter Notebook web application that developers can use for a range of tasks including data visualisation, live code documenets and statistical modelling.
Jupyter Notebooks are a feature of Cosmos DB, and a threat actor can exploit a chain of vulnerabilities to obtain credentials to the NoSQL database system.
No previous access to victim environments is required, and Wiz said the chain of vulnerabilities is trivial to exploit.
Microsoft has acknowledged the vulnerability and disabled the feature within 48 hours after Wiz reported it.
Wiz said the vulnerability has been exploitable for months, and said every Cosmos DB customer should assume they have been compromised.
Microsoft has notified around a third of Cosmos DB customers about the security breach, advising them to regenerate the primary keys to mitigate against the vulnerability.
There is no indication at the this stage that the ChaosDB vulnerability has been exploited, Microsoft advised.