Attackers Were Inside SolarWinds in January 2019
Forensics
,
Next-Generation Technologies & Secure Development
,
Security Operations
CEO Sudhakar Ramakrishna Says Clues Come From Analysis of Virtual Builds

Network management software company SolarWinds, which was the victim of a supply chain attack that had a massive impact, has uncovered evidence that the intruders were in its systems eight months earlier than previously believed.
See Also: Threat Hunting Report: Beyond Supply Chain Attacks
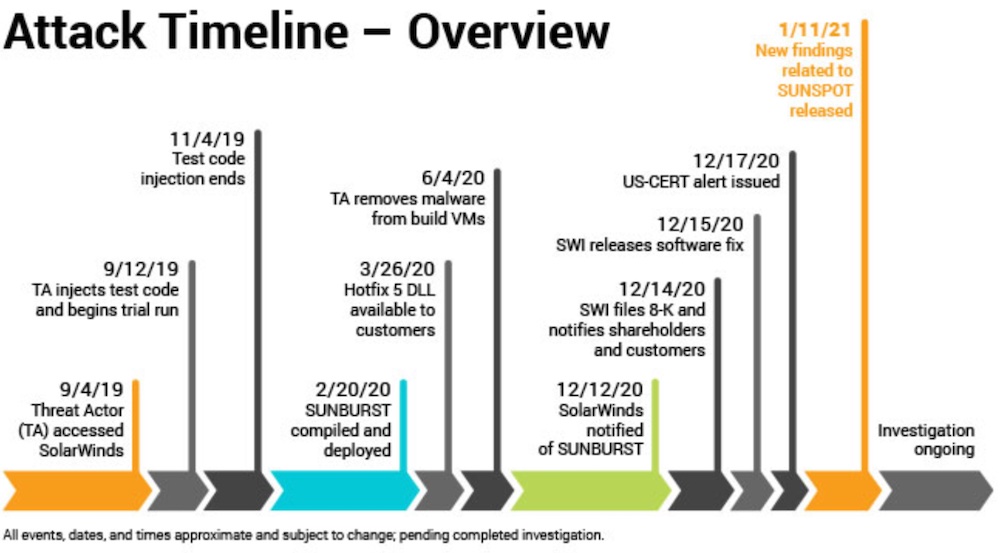
SolarWinds’ original timeline put the first signs of infiltration at about September 2019. But the company has since analyzed hundreds of terabytes of data related to thousands of its virtual build systems, according to CEO Sudhakar Ramakrishna. And that data shows reconnaissance activity started in January 2019, he says.
“They [the attackers] were doing very early recon activities in January of 2019, which explains, I would say, what they were able to do in September, October 2019 as well,” Ramakrishna says.
Ramakrishna was interviewed via a video link on Wednesday at the RSA Conference by Forrester analyst Laura Koetzle.
SolarWinds’ popular Orion network management software was seeded with malware in a software update, the result of a meticulous cyberespionage effort U.S. authorities have blamed on Russia.
Attackers managed to get inside SolarWinds’ build environment and place a backdoor, which was then wrapped into its legitimate software without detection. The updated software was distributed to as many as 18,000 organizations. That led to follow-on attacks on about 100 companies and nine government agencies.
The operation began to unwind, however, in December 2020. FireEye came forward first on Dec. 8, saying its red team tools had been stolen. Shortly thereafter, the intrusion was traced to the backdoored Orion software.
The White House blamed Russia’s Foreign Intelligence Service, also known as the SVR, for carrying out the attacks as part of a cyberespionage campaign. Last month, President Joe Biden ordered sanctions against Russia for the SolarWinds attack and for actions related to the election (see: US Sanctions Russia Over SolarWinds Attack, Election Meddling).
Blaming the Intern ‘Not Appropriate’
The timing of the SolarWinds attack couldn’t have been worse for Ramakrishna. On Dec. 9 – just a day after FireEye’s announcement that it had been hacked – SolarWinds announced that he would take over as CEO on Jan. 4, succeeding Kevin Thompson.
As details of the attack continued to unfold, Ramakrishna didn’t bail on the job and took Thompson’s position. But if the hack wasn’t enough, a joint appearance with Thompson at a congressional hearing in February certainly didn’t help the company’s image (see: Senators Grill Cybersecurity Execs on SolarWinds Attack).
A security researcher had warned SolarWinds that he’d found a password – “solarwinds123” – on a GitHub site for a company file-sharing system. An intern had posted the password on a private GitHub account.
It turned out that the weak password had nothing to do with the supply chain attack, but it did come up at the hearing. Thompson and Ramakrishna said an intern had set the password, and the two were then accused of blaming the intern for the company’s cybersecurity woes.
Ramakrishna says the issue wasn’t handled well at the hearing. SolarWinds employees, including interns, should be able to make mistakes and improve, and failures shouldn’t be highlighted, he says.
“What happened at the congressional hearings where we attributed it to an intern was not appropriate and was not what we are about or is not what we are about,” Ramakrishna says. “We have learned from that, and I want to reset it here by saying that we are a very safe environment, and we want to attract and retain the best talent.”






