Attackers Target Unpatched SAP Applications
Fraud Management & Cybercrime
,
Fraud Risk Management
,
Governance & Risk Management
Exploits Could Lead to System Hijacking, Data Theft, Ransomware Attacks

Attackers are targeting unpatched SAP applications, and the exploits could lead to the hijacking of the vulnerable systems, data theft and ransomware attacks, SAP and Onapsis Research Labs report. They note that patches for most of the flaws have been available for several years.
See Also: Top 50 Security Threats
Onapsis, which monitored SAP applications for attack activities using its honeypots, notes it detected thousands of exploitation attempts using automated tools as well as manual techniques. Of these, about 300 were successful, but they did not result in customer breaches or compromise of SAP applications.
“Given the level of observed threat actors’ capabilities and widespread nature of the ongoing threat activity, SAP and Onapsis are proactively alerting organizations to take immediate action, including swift application of the relevant SAP security patches and performing a compromise assessment and forensic investigation of at-risk environments and a thorough review of security configuration of their SAP landscapes,” the joint report notes.
An Onapsis spokesperson tells Information Security Media Group that it has “not identified the hackers or attributed the exploit attempts to specific threat actors.”
On Tuesday, the U.S. Cybersecurity and Infrastructure Security Agency alerted organizations to immediately apply patches to prevent malicious activities.
Vulnerabilities
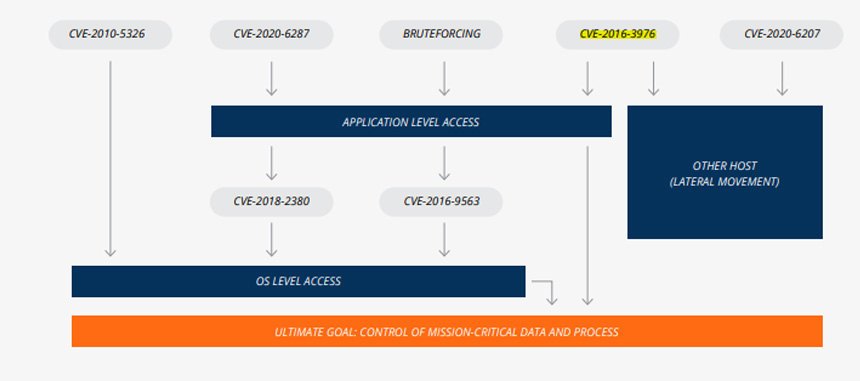
The exploitation activities are mostly related to six CVEs and an unsecured configuration, Onapsis reports.
- CVE-2010-5326 is a critical vulnerability in SAP’s NetWeaver Application Server Java platforms that allows unauthenticated remote attackers to execute arbitrary code via an HTTP or HTTPS request. The report identified 206 exploitation attempts from 10 IP addresses against this vulnerability. The attackers were attempting to execute OS commands in the underlying operating system. A patch was released in May 2016.
- CVE-2018-2380 is a vulnerability found in SAP CRM platform versions that allows attacker to exploit insufficient validation of path information. The report notes the attackers are using this vulnerability to drop SAP web shells using the admin account, which then allows them to gain access to the SAP application resources, such as database information, as well as achieve ownership for critical files and gain the ability to shut down. SAP patched this vulnerability in March 2018.
- CVE-2016-3976 is a highly critical vulnerability found in SAP NetWeaver AS Java platform versions 7.1 to 7.5. Exploiting the flaw allows remote attackers to read arbitrary files in the fileName parameter to CrashFileDownloadServlet, aka SAP Security Note 2234971. This vulnerability could also allow privilege escalation and a potential full-system compromise, the report notes. A patch for this flaw was released in March 2016.
- CVE-2016-9563 is a remote authentication vulnerability that affects SAP NetWeaver AS JAVA 7.5. Onapsis notes exploitation of this vulnerability can result in denial-of-service attacks. An exploit allows attackers to gain unauthorized access, resulting in a loss of confidentiality. This vulnerability was patched in August 2016.
- CVE-2016-3976 is a directory traversal vulnerability in SAP NetWeaver AS Java that affects versions 7.1 to 7.5 and allows remote attackers to read arbitrary files. Onapsis notes the vulnerability can also lead to privilege escalation. SAP issued patches in March 2016.
- CVE-2020-6207 is a critical vulnerability – with a CVSS score of 10 – that affects SAP Solution Manager, or SolMan, which is a central component of every SAP installation. Once this application is compromised, attackers can gain complete control over all interconnected SAP applications in the environment. Onapsis notes that in January, after an exploit was released, it detected a significant increase in exploit activity. The vulnerability was patched by SAP in March (see: Researchers Identify SAP Flaw Exploit).
In addition to exploiting these vulnerabilities individually, attackers have been chaining the flaws together for wider impact, Onapsis notes.
The Scale of Threat
Given SAP’s huge customer base, successful exploitation of vulnerable devices could have a big impact, says Setu Kulkarni, vice president of strategy at WhiteHat Security.
“Our reporting has found that independent security vendors and technology companies have an inordinately high window of exposure,” Kulkarni, says. “We are seeing that ISVs [independent software vendors] and technology companies are lacking in their security rigor as they ultimately may pass on the security responsibilities to the companies that use the ISV to build products for their customers.”
Kevin Dunne, president at security firm Pathlock, notes: “Most federal agencies are running on SAP, as it has become the industry standard for government entities. However, these SAP implementations are often on-premises and managed by the government entities themselves due to security concerns. These systems then become increasingly vulnerable when updates and patches are not applied in a timely fashion, leaving them wide open for interested hackers.”
Scott Caveza, research engineering manager at Tenable, adds: “Despite patches being available for months and even years, attackers are still finding and exploiting unpatched SAP systems. This serves as a reminder to administrators of sensitive data and applications that applying patches, mitigations or workarounds are paramount to thwarting malicious actors looking to exploit well-known vulnerabilities.”
Wider Impact?
Exploits of vulnerabilities in SAP technologies that are in widespread use could potentially be leveraged for wider-scale attacks, along the lines of the SolarWinds supply chain attack, Kulkarni of WhiteHat Security says.
“There is a broader risk here and arguably a bigger one. Connected systems are an underlying condition for a supply chain type attack. In the case of packaged apps like SAP, they usually end up being connected to other systems – like CRMs, cash systems and a myriad of other critical business applications – all of which, by the way, are packaged applications themselves.”
Dunne notes, however, that the majority of the SAP vulnerabilities do not pertain to software releases.
“The vulnerabilities are not emanating from software releases provided by SAP or typically being used as a backdoor to get into other systems” Dunne says. “They are simply vulnerabilities which were typically unknown by SAP during development and then were found by security researchers or bad actors after the SAP release. Because the majority of SAP customers are still hosting their own instances on-premises, it must fall to the customers themselves to be on the lookout for patches and apply them to their instance quickly.”






