Attackers’ Dwell Time Plummets as Ransomware Hits Continue
Fraud Management & Cybercrime
,
Fraud Risk Management
,
Incident & Breach Response
Faster Detection Is Good News, But More Speed Still Needed, Mandiant Reports
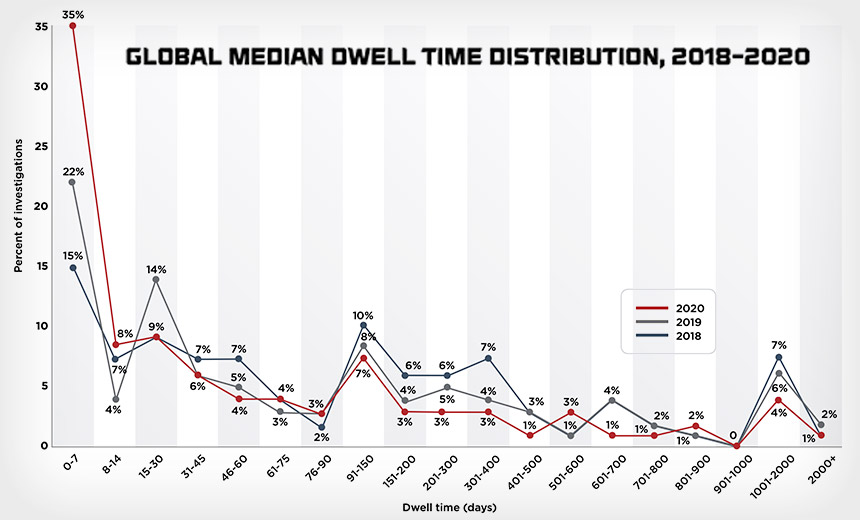
“Dwell time,” which refers to how long hackers hang out in an organization’s network before being discovered, has historically been a key metric for expressing whether hack-attack victims are getting better at detecting intruders.
See Also: Live Webinar | Empowering Financial Services with a Secure Data Path From Endpoint to Cloud
The longer attackers can spend in an organization’s network, the more chance they have to jump to systems, crack passwords, find and exfiltrate valuable data and maybe leave crypto-locking malware on systems.
The good news is that the average dwell time continues to decline, according to FireEye’s Mandiant incident response group. The bad news is that it declined, in part, due to ransomware attackers often quickly revealing themselves when corporate networks become crypto-locked and inaccessible.
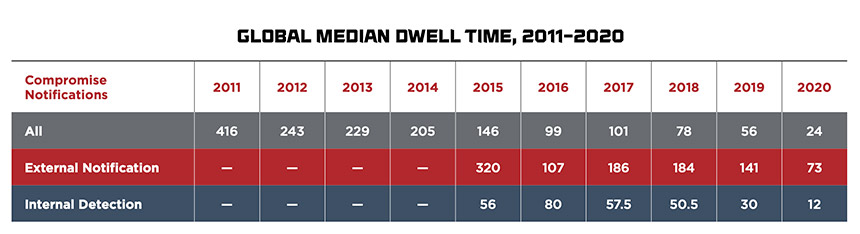
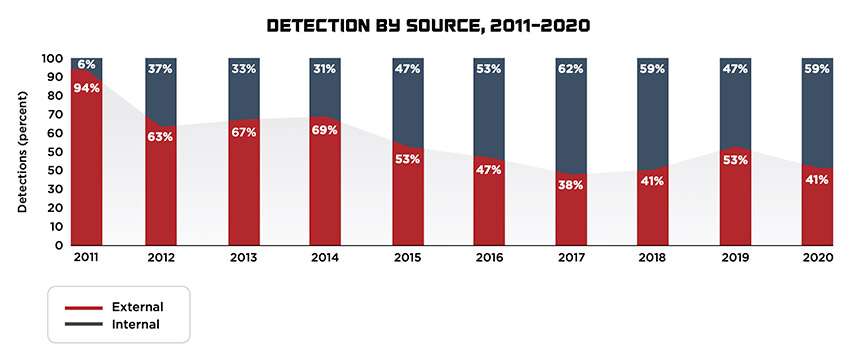
Mandiant keeps a running tally of how long organizations that it assists take to detect a breach, as well as whether they self-detected the attack – thanks to internal teams independently finding it – or if they were alerted to the breach by an external event or third party, such as the FBI or another law enforcement agency.
For cases Mandiant investigated from October 2019 through September 2020 – “59% of the security incidents … were initially detected by the organizations themselves – an improvement of 12% from the prior year,” the company says in its M-Trends 2021 report.
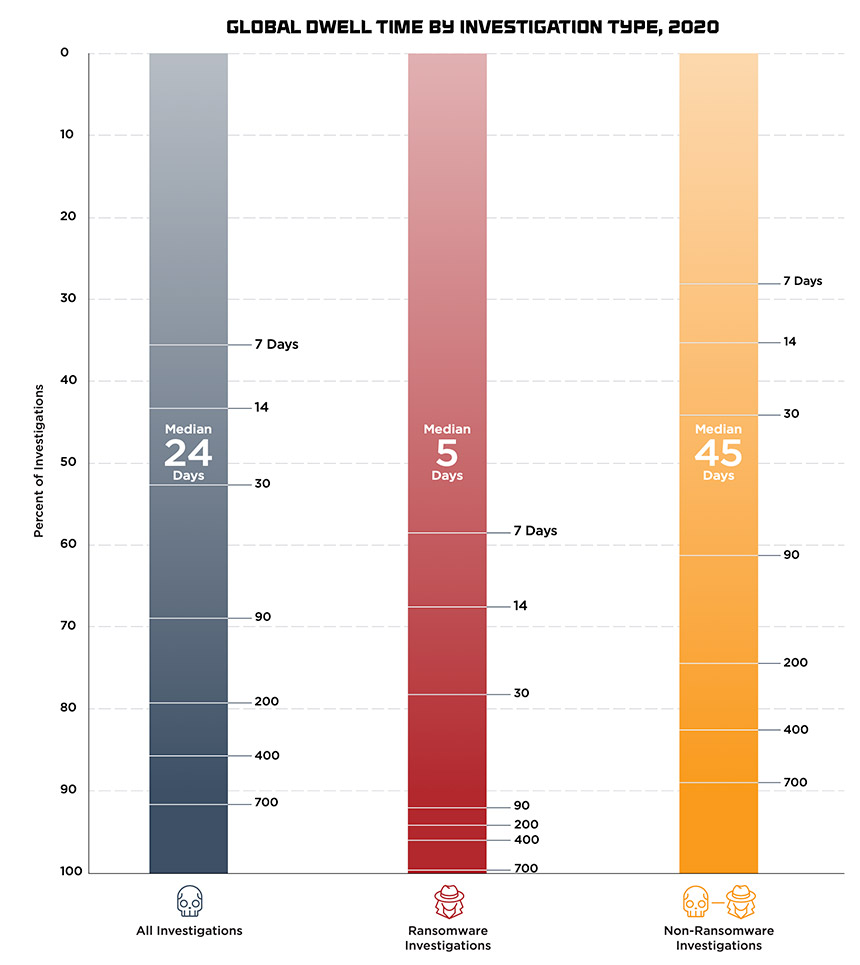
Ransomware was involved in 25% of those cases – up from 14% in the prior 12 months – and “of these ransomware intrusions, 78% had dwell times of 30 days or fewer compared to 44% of non-ransomware intrusions,” it says. At the other end of the spectrum, 11% of all breaches lasted more than 700 days, compared to just 1% of cases involving ransomware.
“Organizations are getting better and better at detecting threat actors in their environment,” says Stuart McKenzie, who heads FireEye’s Mandiant services group in Europe, the Middle East and Africa (see: Mitigating Risks as Ransomware Tactics Change). “Over time, we’ve really seen that dwell time drop. In the Americas, the internal notification is now down to … nine days, which is fantastic. If you think about the amount of time it takes an attacker to accomplish their action or objectives, nine days really means you’re having a good, fighting chance of being able to detect them and stop them in their tracks.”
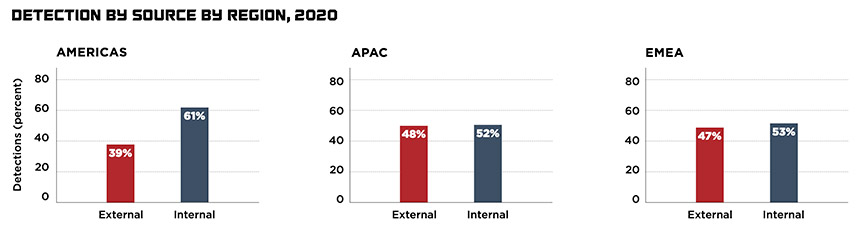
But many organizations still aren’t rapidly detecting attackers inside their networks, and the longer attackers lurk, the more entrenched they can become.
“Global dwell time is 24 days,” McKenzie says. “That’s too long for an attacker to be in the environment. They’re able to laterally move; they’re able to change from using malware to the kind of tools that you’d have in your network for administration. So it becomes harder and harder to spot them.”
Quicker Detection Always Better
How can more organizations self-detect breaches?
The answer is to invest in better logging and monitoring tools, backed by the right practices and procedures, Mandiant says. Organizations also must maintain a baseline of what looks normal.
Ideally, they also should practice penetration testing, to see if they’re susceptible to the types of real-world exploits being used by attackers. And more advanced firms might also run their own threat intelligence programs to understand the biggest risks they face, deploy threat hunting teams to better ascertain when and if they might already have been hacked and continually tighten defenses.
Attackers Hit Software Flaws, RDP
Too many organizations still fail to lock down common attack vectors.
Ransomware incident response firm Coveware, for example, notes that of the thousands of cases it investigated in the first three months of this year, “compromised remote desktop protocol connections” were the most common attack vector, when the initial access vector could be ascertained.
“RDP remains a frustratingly common vulnerability despite well-known secure remote connection best practices,” Coveware said.
Mandiant says that when its investigators were able to identify how attackers breached a victim’s network, exploits of software flaws were most common – occurring in 29% of cases – followed by phishing attacks in 23% of cases. “Adversaries used stolen credentials or brute forcing as the initial attack vector in 19% of the investigations” while “gaining access to a network that was previously compromised occurred in 12% of cases,” it says.
Mandiant reports that 25% of all intrusions it investigated involved attackers gaining access to an organization’s remote desktop protocol connections at some stage in the attack.
Data Theft Increasingly Common
In 32% of all cases it investigated in the 12-month period, attackers also stole data, and in 9% of all cases, “the data theft likely supported intellectual property or espionage end goals,” Mandiant says (see: Ransomware + Exfiltration + Leaks = Data Breach).
That’s an important distinction, because many ransomware-wielding gangs try to steal data from the easiest possible source, simply to be able to tell a victim that they’ve stolen data and are holding it to ransom in the hopes that it will pressure more victims to immediately pay.
“Despite the threats, threat actors rarely take the time to steal data that any other criminals or interested parties would want to purchase,” Coveware says. “The stolen data is just proof that the attack occurred and sometimes creates legal obligations for the victim.”
As such data theft highlights, so-called ransomware gangs are rapidly evolving into what Mandiant terms “multifaceted extortion operators” who don’t always wield ransomware.
The Clop gang, for example, got its hands on data that was being stored on Accellion File Transfer Appliances and used it to pressure users to pay for a promise that the stolen data wouldn’t get leaked. Those shakedowns involved no ransomware (see: Cyber Extortion Thriving Thanks to Accellion FTA Hits).
Meanwhile, the Babuk gang – after hitting the Metropolitan Police Department of Washington, D.C. – on Friday announced that it was stopping ransomware attacks altogether. Instead, Bleeping Computer reports, the gang will devote itself to stealing data and extorting companies for a promise to not dump it.
The Need for Speed
To help mitigate attack threats, Mandiant’s McKenzie says all organizations should strive to independently detect any network intrusion within less than 10 days. Attackers, however, will no doubt devote increasing resources to trying to stay undetected longer.

“Attackers are always going to get more sophisticated. It’s their objective; it’s what they’re here for. They’re trying to compromise organizations,” he says. “So if we do get faster at detecting, they’ll get faster at exploiting.”
ISMG Director of Productions Anna Delaney contributed to this report.