Android stalkerware threatens victims further and exposes snoopers themselves
ESET research reveals that common Android stalkerware apps are riddled with vulnerabilities that further jeopardize victims and expose the privacy and security of the snoopers themselves
Mobile stalkerware, also known as spouseware, is monitoring software silently installed by a stalker onto a victim’s device without the victim’s knowledge. Generally, the stalker needs to have physical access to a victim’s device so as to side-load the stalkerware. Because of this, stalkers are usually someone from the close family, social or work circles of their victims.
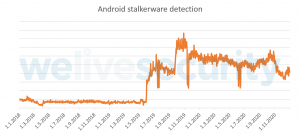
Based on our telemetry, stalkerware apps have become more and more popular in the last couple of years. In 2019 we saw almost five times more Android stalkerware detections than in 2018, and in 2020 there were 48% more than in 2019. Stalkerware can track the GPS location of a victim’s device, conversations, images, browser history and more. It also stores and transmits all this data, which is why we decided to forensically analyze how these apps handle the protection of the data.
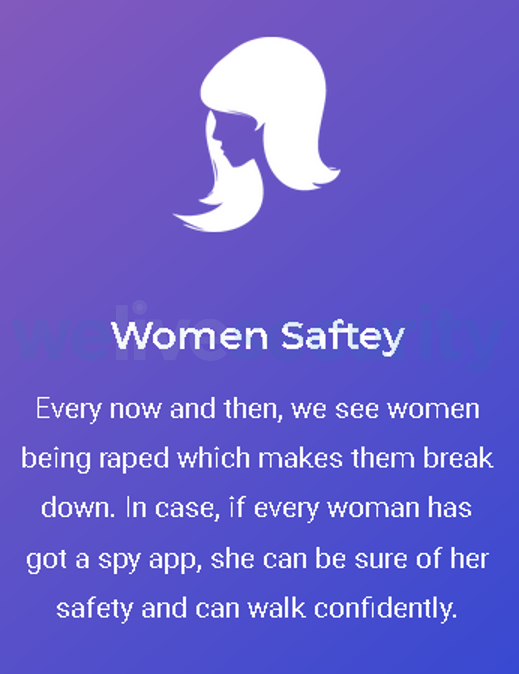
For stalkerware vendors, to stay under the radar and avoid being flagged as stalkerware, their apps are in many cases promoted as providing protection to children, employees, or women, yet the word “spy” is used many times on their websites. Searching for these tools online isn’t difficult at all; you don’t have to browse underground websites. The screenshot below depicts perhaps the most unsavory example of a claim these apps monitor women for their safety.
More than 150 security issues in 58 Android stalkerware apps
If nothing else, stalkerware apps encourage clearly ethically questionable behavior, leading most mobile security solutions to flag them as undesirable or harmful. However, given that these apps access, gather, store, and transmit more information than any other app their victims have installed, we were interested in how well these apps protected that amount of especially sensitive data.
Hence, we manually analyzed 86 stalkerware apps for the Android platform, provided by 86 different vendors. In this analysis we define a person who installs and remotely monitors or controls stalkerware as a stalker. A victim is a targeted person that a stalker spies on via the stalkerware. Finally, an attacker is a third party whom the stalker and the victim are not usually aware of. An attacker can carry out actions such as exploiting security issues or privacy flaws in stalkerware or in its associated monitoring services.
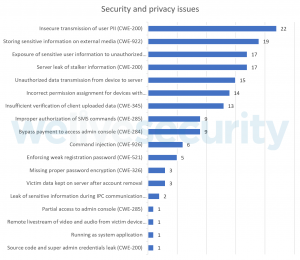
This analysis identified many serious security and privacy issues that could result in an attacker taking control of a victim’s device, taking over a stalker’s account, intercepting the victim’s data, framing the victim by uploading fabricated evidence, or achieving remote code execution on the victim’s smartphone. Across 58 of these Android applications we discovered a total of 158 security and privacy issues that can have a serious impact on a victim; indeed, even the stalker or the app’s vendor may be at some risk.
Following our 90-day coordinated disclosure policy, we repeatedly reported these issues to the affected vendors. Unfortunately, to this day, only six vendors have fixed the issues we reported in their apps. Forty-four vendors haven’t replied and seven promised to fix their problems in an upcoming update, but still have not released patched updates as of this writing. One vendor decided not to fix the reported issues.
Discovered security and privacy issues
The 158 security and privacy issues in 58 stalkerware apps are ordered based on the prevalence of occurrences found in the analyzed stalkerware.
Takeaway
The research should serve as a warning to potential future clients of stalkerware to reconsider using software against their spouses and loved ones, since not only is it unethical, but also might result in revealing the private and intimate information of their spouses and leave them at risk of cyberattacks and fraud. Since there could be a close relationship between stalker and victim, the stalker’s private information could also be exposed. During our research, we identified that some stalkerware keeps information about the stalkers using the app and gathered their victims’ data on a server, even after the stalkers requested the data’s deletion.
This is just a snapshot of what we found during our research and so we invite you to read the whole paper.