Advisory Describes Chinese Attackers’ Tactics
Governance & Risk Management
,
IT Risk Management
,
Next-Generation Technologies & Secure Development
Report Offers Risk Mitigation Advice, Stressing Prompt Patching
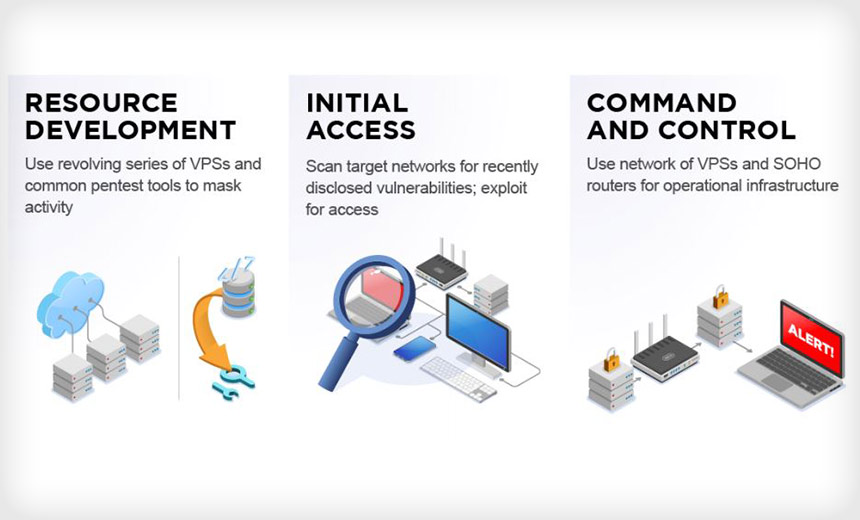
Three federal agencies released a 31-page Joint Cybersecurity Advisory Monday that describes 50 tactics, techniques and procedures that Chinese state-sponsored cyberattackers are using to target organizations in the U.S. and allied nations.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
The Chinese attack techniques outlined in the report include exploiting well-known vulnerabilities in widely used applications, such as Pulse Secure, Apache, F5 Big-IP and Microsoft products.
“The Chinese are patient, creative and relentless adversaries. If they want to get to a victim, they will keep hunting tirelessly until they find a crack in the armor,” says Adam Flatley, director of threat intelligence at the security firm Redacted Inc., who worked as a subject matter expert on the federal Ransomware Task Force.
The risk mitigation steps suggested in the advisory cover basic cyber hygiene tasks, such as timely patching; enhanced monitoring of network traffic, email and endpoint systems; and the use of protection capabilities, such as antivirus programs and strong authentication.
Series of Announcements
The advisory, which the National Security Agency, U.S. Cybersecurity and Infrastructure Security Agency and FBI issued jointly, came as the Biden administration on Monday accused an attack group working for China’s Ministry of State Security, or MSS, of carrying out a series of attacks against vulnerable Microsoft Exchange email servers earlier this year as well as ransomware attacks. The MSS is China’s civilian intelligence, security and secret police agency.
“Chinese state-sponsored cyber activity poses a major threat to U.S. and allied systems,” the advisory says. “These actors aggressively target political, economic, military, educational and critical infrastructure personnel and organizations to access valuable, sensitive data. These cyber operations support China’s long-term economic and military objectives.”
And on Friday, the Justice Department unsealed an indictment of four Chinese nationals working with the MSS in connection with an alleged hacking campaign conducted from 2011 to 2018 that targeted universities and government entities to obtain trade secrets, medical research and other intellectual property.
Experts Weigh In
Defending against the cyberthreats posed by attackers working on behalf of the Chinese government “requires a true end-to-end security mindset,” Flatley says. “You have to accept that you are a target and examine yourself just like the adversary would in order to truly prepare for, prevent, detect and respond to cyber intrusions.”
Mike Hamilton, co-founder of CI Security and the former CISO of the city of Seattle, highlights a critical mitigation step: “When a vulnerability is announced, there is immediate scanning looking for exposures. Monitoring would tip off the fact that you may have been identified as a target and allow mitigating measures to be taken prior to application of a patch.”
Staying protected from Chinese cyberattacks first and foremost involves getting patches deployed quickly and mitigating exposures for those applications that that cannot be patched, he says.
Monitoring for aberrational use of penetration and administrative tools, such as Powershell and Cobalt Strike, can help identify persistent actors, he adds.
Scott Shackelford, chair of Indiana University’s cybersecurity program, believes any adversary with enough resources and time will break through the defensive measures listed in the federal advisory. Instead, he calls for a more holistic approach.
“A better approach than trying to keep such adversaries out is to take a ‘zero trust’ strategy and then take a ‘public health’ approach to building resilience and protecting your crown jewels, such as through air gapping vital information including trade secrets,” he says. “The Biden administration recently called for such an approach in its executive order.”
Attack and Defense
The advisory describes Chinese attacker’s general practices and offers detailed lists of recon, initial access and execution activities.
The attackers take the time to understand cybersecurity best practices, exploit known vulnerabilities and use virtual private servers as an encrypted proxy. They use the VPS and small office and home office devices as operational nodes to evade detection, the advisory notes.
The Chinese threat actors often begin an attack sequence by conducting a thorough reconnaissance, conducting scans of Microsoft 365, the agencies note. This is designed to gain information about a targeted network. The process is often automated using Python scripts to locate specific files, paths or vulnerabilities.
“The cyber actors can gain valuable information on the victim network, such as the allocated resources, an organization’s fully qualified domain name, IP address space and open ports to target or exploit,” the advisory says.
To counter these recon efforts, the advisory suggests scrubbing user email addresses and contact lists from public websites, sharing only the minimum necessary data and information with third parties and monitoring and limiting third-party access to networks.
The advisory also recommends monitoring network traffic for sources associated with botnets, adversaries and known bad IPs based on threat intelligence.
Attackers’ Tactics
The attackers often gain initial access to a network through conducting watering hole and typo-squatting campaigns, finding zero-day vulnerabilities to exploit or taking advantage of known vulnerabilities in internet-facing systems.
The advisory notes Chinese-supported attackers routinely target on-premises Microsoft Exchange and Outlook Web Access to plant webshells.
The attackers also frequently target on-premises identity and access management services in hybrid cloud environments to gain access to cloud resources.
Chinese attackers also routinely use spear-phishing campaigns and mass phishing campaigns with well-developed social engineering lures, the advisory points out.
Some defensive measures suggested by the advisory include ensuring all browsers and plugins are up to date, restricting access to unneeded websites and blocking unneeded downloads/attachments and JavaScript.
Some Chinese attacks are executed using cmd.exe in operating systems, PowerShell to conduct further recon, Python scripts to exploit vulnerable servers and Unix shell to conduct discovery, enumeration and lateral movement on Linux servers in the victim network, the advisory says.
Organizations can help thwart these moves by turning on PowerShell logging and then pushing those logs to a SIEM tool – as well as putting an antivirus program in place, the agencies recommend.
Attackers maintain persistence by using benign executables, which use DLL loadorder hijacking to activate the malware installation process and implant webshells. Additionally, the attackers often bypass multifactor authentication by creating a new sign-in policy, the advisory says.
As a result, organizations should disallow loading of remote DLLs, monitor for policy changes to authentication mechanisms used by the domain controller, and look for suspicious account behavior across systems that share accounts, the advisory notes.






