The Business of Ransomware: Specialists Help Boost Profits
Business Continuity Management / Disaster Recovery
,
Cybercrime
,
Cybercrime as-a-service
Ransomware-as-a-Service Operations Tap Expert Intrusion Specialists and Negotiators
As ransomware attacks become more prolific, their success is being driven by the increasing use of specialists.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
Hollywood’s vision of criminal hackers might be heavy on solo keyboard superheroes in black hoodies who chain-consume overcaffeinated soft drinks, are wise in the ways of leet-speak and gaze deep into green CRTs as they speed-type their way past any “access denied.” But like all types of cybercrime, the reality is more mundane and business-driven.
“Each stage includes various malicious activities that different actors specialize in.”
Cybercriminals are seeking an illicit payday, and their aim is to maximize profits in the minimum amount of time – because work isn’t everything. “Most of us have families, kids, lovers, parents, pets, hobbies, problems, etc.,” an individual known as “A,” who appears to run the MountLocker ransomware-as-a-service – aka RaaS – operation, told French technology news site Zataz earlier this year (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
Refinements Continue
As criminals seek new ways to earn more money more quickly using ransomware, they’ve hit on numerous new tactics for success, including using crowdsourced approaches.
Ransomware has already come a long way. In the old days, such malware might simply lock a PC screen and demand a payoff to unlock it. Later, of course, attackers began forcibly encrypting PCs, servers and backups and charging victims for a decryption key.
By the mid-2010s, the ransomware-as-a-service approach began to emerge. In this model, a developer retains a share of every ransom paid in return for an affiliate getting to use their malware.
By 2020, a more refined affiliate-driven approach was surging in popularity, with pure-play operations – meaning a single group that handled every aspect of an attack – becoming less common, seemingly because the RaaS model allows for greater specialization, leading to more successful attacks against larger victims, delivering higher profits.
Increased Specialization
Back to Hollywood, this time for a heist film analogy: Just as experts get brought in to meet the demands of a given scenario – say, a lock-picker able to handle a rare type of safe in a bank – using specialists enables RaaS operations to fine-tune their approach to amassing and shaking down victims.
In the ransomware ecosystem, such specialization has become increasingly refined. Broadly speaking, specialists work in one of these four areas, as described in a new report from Israeli cybersecurity firm Kela:
- Code: Develop or acquire malware with required capabilities;
- Spread: Gain access to victims’ systems and networks and deploy the malware;
- Extract: Maintain access to infected machines, perhaps also exfiltrating data and processing it;
- Monetize: Realize a profit from the attack, potentially by receiving a ransom payment as well as selling stolen data or credentials to others.
“Each stage includes various malicious activities that different actors specialize in,” and the increasing popularity of ransomware has been attracting more individuals who want to supply such services, says Victoria Kivilevich, a threat intelligence analyst at Kela who wrote the new report.
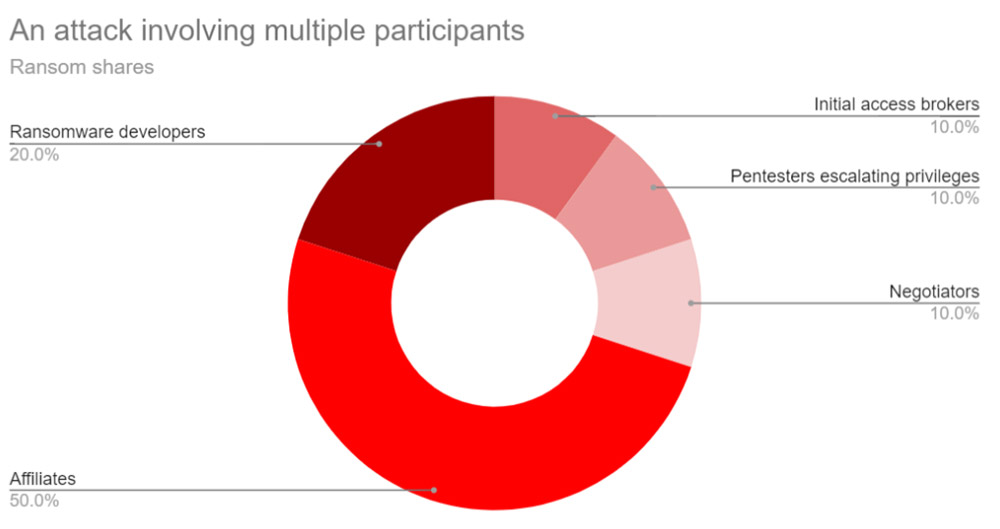
“When looking specifically into the ransomware supply chain, we can see many actors piling up in the ‘extract’ niche, where actors focus on escalating privileges within a compromised network, and the ‘monetize’ niche,” which involves attackers trying to intimidate victims into paying, for example via distributed denial-of-service attacks and spam telephone calls, Kivilevich says.
Extraction: Intrusion Specialists
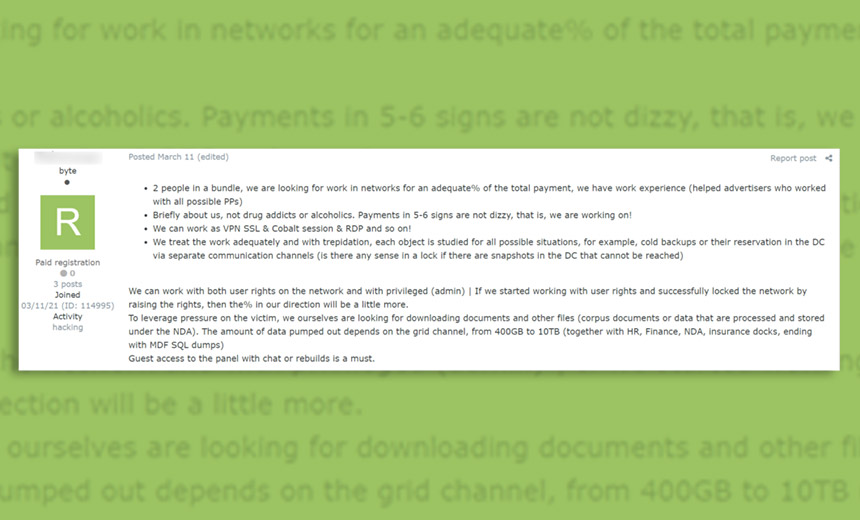
Known as “pentesters” on Russian-language cybercrime forums, RaaS operations regularly advertise for these types of individuals, seeking help with obtaining domain-level access on victims’ networks and often offering them 10% to 30% of every ransom paid by a victim, according to Kela’s report.
How these specialists get used by a RaaS operation varies. “Bots from a botnet, European corporations,” one advertisement seen by Kela reads, referring to PCs that have been infected with malware via a botnet – to which a RaaS operation will have outsourced obtaining initial access to systems – via which ransomware could now be deployed onto each system.
The advertisement also states: “This is teamwork, we pay a percentage of the profit. We are looking for one person to work out 2-3 bots per day. Constant flow until the end of the year is guaranteed. A little about teamwork: we already have specialists, you can count on fixed bonuses in USD and about 10% from the financial profit.”
Some specialists, meanwhile, advertise their services to RaaS operations. “For example, in a thread titled ‘Will escalate admin rights, will gain domain administrator,’ an author offers to perform the whole ransomware encryption process: to bypass antivirus solutions, steal data, delete backups and shadow copies and even encrypt a network,” Kivilevich says. “There are other users ready to do the whole job once they’re provided with initial access. Another example shows an initial access broker who usually sells VPN access listings also ready to escalate privileges – for a fee.”
But not all want to work with ransomware operators or affiliates. Some, instead, prefer to focus on hacking payment processing systems and stealing payment card data, among other areas. “For example, one offer Kela discovered specifically mentions ‘we do not work with crypto lockers,’ meaning ransomware,” Kivilevich says.
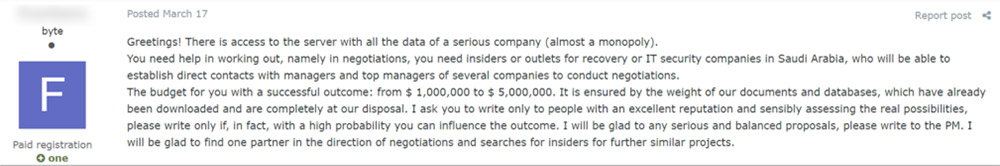
Monetization: Negotiators, Intimidators
The business of working with a ransomware operation’s “customers” – meaning victims – also continues to evolve.
In sales-speak, the aim is to handle prospects – aka “victims” – and convert as many of them as possible into paying “customers,” sometimes by allowing ransoms to be negotiated down. Support teams also assist victims with the process of procuring cryptocurrency – typically bitcoin or monero – to pay the ransom.
Since 2020, more RaaS operators have used dedicated data leak sites to name and shame victims or post extracts of stolen data, with a promise that the leaks will be removed, and stolen data deleted, if a victim pays.
Some RaaS operations outsource intimidation. Tactics include employing call centers to cold-call victims, hiring well-connected negotiators on a per-contract basis and using DDoS attacks to disrupt a business’s operations.
In the case of DDoS shakedowns, for example, the notorious REvil – aka Sodinokibi – RaaS operation “was observed seeking to hire a team or a person with a botnet that could DDoS a targeted company and its clients as an additional measure,” Kivilevich says. “The REvil representative stated: ‘Estimate your potential – we can ask to shut down even Microsoft for a couple of days.'”
Ongoing Success Stories
Obviously, larger RaaS operators, such as REvil, are setting their sights high, as evidenced by their getting an $11 million payoff from JBS, the world’s biggest meat processor; demanding $50 million from laptop manufacturer Acer and using software vendor Kaseya’s own software to infect thousands of managed service providers and their clients (see: Kaseya Attack: REvil Offers $70 Million ‘Universal Decryptor’).
With ransomware continuing to be a lucrative moneymaker, big names continuing to fall victim and innovative new refinements in the business model helping to push profits even higher, is it any surprise that the criminals running these operations should have so much swagger?






