List of Victims of Kaseya Ransomware Attack Grows
Business Continuity Management / Disaster Recovery
,
Fraud Management & Cybercrime
,
Governance & Risk Management
2 Maryland Towns Report Malware on Their Networks
Two small Maryland towns are among the latest victims to come to light almost a week after the REvil ransomware supply chain attack that targeted Kaseya’s VSA remote IT management software. The company says the attack on on-premises VSA installations affected about 60 of its managed service provider customers and up to 1,500 of their clients.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
North Beach and Leonardtown both said Kaseya’s software installed on their networks by their MSPs was targeted by ransomware attacks on July 2. Among others identified as victims of the ransomware attack on VSA are the Swedish grocery chain Coop and 100 kindergartens and 11 schools in New Zealand.
North Beach and Leonardtown, both southeast of Washington, say their computer systems went down at 12:30 p.m. on July 2, the day the Kaseya attack was revealed.
The ransomware reached Leonardtown through its MSP, JustTech, The Washington Post reports. North Beach officials also confirmed in a statement that VSA software was present on its network, but they did not specify the MSP involved.
Leonardtown officials say the town’s entire network was encrypted, and the attackers demanded an unstated ransom for the decryptor key, but the town refused to pay and was able to restore its system through backups. North Beach did not comment on whether its attackers demanded a ransom.
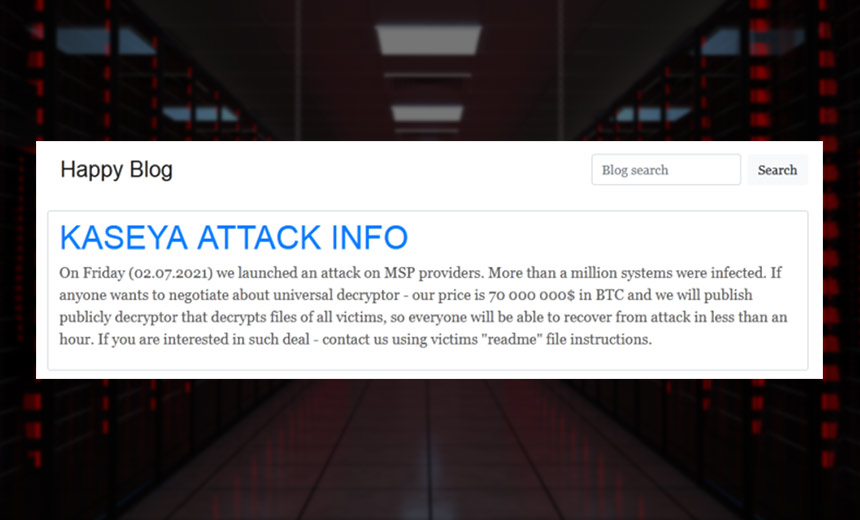
REvil initially demanded a $70 million ransom for a universal decryptor for use by all victims, but the demand was quickly lowered to $50 million.
The Downstream Impact
Cybersecurity analysts say it’s likely that a substantial number of additional victims will come to light in the coming days, pointing to similar revelations after other recent supply chain attacks, such as those affecting SolarWinds and Accellion.
”We are slowly collecting victim data from open-source reporting; right now we have about a dozen, but we expect that number will grow over the next few days,” says Allan Liska, an intelligence analyst at Recorded Future.
Mark Loman, the director of engineering at Sophos who has been immersed in studying the scope and impact of the Kaseya supply chain attack, says it’s the largest ransomware incident he’s seen, likely affecting organizations worldwide.
The SolarWinds attack ultimately affected 18,000 users of the Orion network monitoring platform and resulted in follow-on attacks on nine government agencies and 100 companies.
Months after the December 2020 cyberattack on Accellion’s File Transfer Appliance, the identities of more organizations affected are still being revealed.
For example, on July 2, Morgan Stanley informed the New Hampshire attorney general of a data breach caused by the Accellion FTA vulnerability.





