Avaddon Ransomware Attacks on The Rise
The ransomware campaign in question is targeting organizations from an extensive array of sectors in the US and worldwide, with the FBI declaring in a TLP:GREEN flash alert published last week that Avaddon affiliates are trying to breach the networks of manufacturing, healthcare, and other private sector organizations around the world.
Whilst the FBI offered this information the ACSC expanded on this topic as well, saying that the ransomware gang’s affiliates are targeting entities from a wide range of sectors, and are including sectors like government, finance, law enforcement, energy, information technology, and health.
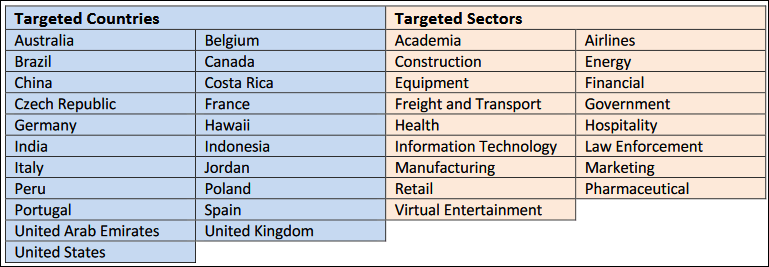
The FBI is only mentioning the ongoing attacks, but the officials from the ACSC are providing a list of countries that are under attack, including the US, UK, Germany, China, Brazil, India, UAE, France, and Spain.
The Australian Cyber Security Centre (ACSC) is aware of an ongoing ransomware campaign utilizing the Avaddon Ransomware malware [..] actively targeting Australian organizations in a variety of sectors.
The ACSC is aware of several instances where the Avaddon ransomware has directly impacted organizations within Australia.
The ACSC also mentioned that the Avaddon threat actors are threatening with denial-of-service (DDoS) attacks in an attempt to persuade victims into paying ransoms, this threat coming as an addition to leaking stolen data and encrypting their system, but at this time no evidence has been found of DDoS attacks following any Avaddon ransomware attacks.
The Avaddon gang declared in January 2021 that they will launch DDoS attacks to take down victims’ sites or networks until they reach out and begin negotiating to pay the ransom.
It’s not at all surprising to see threat actors combining ransomware and DDoS attacks: DDoS is cheap, easy, and in some cases may help convince some companies that speedy payment is the least painful option. The more pressure the criminals can put companies under, the better their chances of extracting payment.
Avaddon ransomware samples were first found and identified in February 2019, with Avaddon starting the recruitment of affiliates in June 2020 after the launch of a massive spam campaign that was targeting users worldwide.
The affiliates joining this RaaS operation are responsible for compromising networks in order to deploy payloads or distribute the malware via spam or exploit kits.
RaaS is different from the ‘traditional’ malware-dispersal model in which the roles were well-defined, the RaaS ‘business’ model relying on an aggregator, that can be a person or a group that sells or rents malware to interested parties, which are called ransomware operators.
Avaddon is a RaaS operation that asks affiliates to follow certain rules and pays each one of them with 65% of the ransom payments they bring in, with the operators getting a 35% share, with the average ransom payment demanded by Avaddon affiliates being roughly 0.73 for a decryption tool.
Neutralize ransomware before it can hit.
Heimdal™ Ransomware Encryption Protection
Specifically engineered to counter the number one security risk to any business – ransomware.
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
The Avaddon affiliates are also known for stealing data from their victims’ networks before encrypting systems for double-extortion.







