Attackers Using Malicious Doc Builder Called ‘EtterSilent’
Report: Builder Allows Cybercriminals to Create Specialized Office Documents
Researchers at Intel 471 report cybercriminal gangs are using a newly discovered malicious document builder called “EtterSilent” to create differentiated, hard-to-discover, malicious documents that can be deployed in phishing attacks.
See Also: Top 50 Security Threats
EtterSilent is being used by several cybercrime groups, which Intel 471 did not name, to create malicious documents used to deliver a wide variety of malware, including the Trickbot banking Trojan. Researchers say they first spotted EtterSilent in December 2020.
The primary capability of EtterSilent lets attackers customize the package used to deliver the malicious document and affects what attackers can do post-exploit, says Brandon Hoffman, CISO of Intel 471.
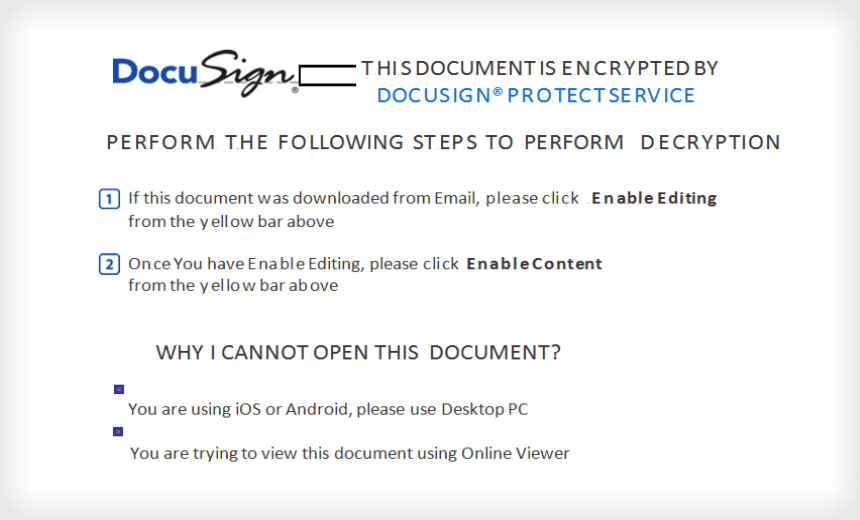
Intel 471 notes that the builder creates two basic types of malicious Microsoft Office documents. One takes advantage of a remote code execution vulnerability tracked as CVE-2017-8570, and the other uses a malicious macro. In both cases, the fake Office product is disguised as a DocuSign document – a business tool used to sign documents electronically.
“The maldoc then leverages Excel 4.0 macros stored in a hidden sheet, which allow an externally hosted payload to be downloaded, written to disk and executed using regsvr32 or rundll32. From there, attackers can follow up and drop other assorted malware,” the report notes.
“Used in conjunction with other forms of malware, it’s a prime example of how ease of use and a concentration of skill sets leads to a commoditization of the cybercrime economy,” Intel 471 says.
In a separate report Heimdal Security says the remote code execution vulnerabilities CVE-2017-11882 and CVE-2018-0802 are also commonly used in conjunction with a malicious document created by EtterSilent.
Recent EtterSilent Campaigns
EtterSilent is sold through darknet ads posted on Russian-language forums and was most recently deployed in a March 21 attack in which attackers used it as part of a BazarLoader campaign. BazarLoader is a backdoor loader used to deliver a variety of malware types.
The attackers put a slight twist in this attack by only using the DocuSign name instead of loading the email with a malicious Excel file.
“The analyzed maldoc did not use a DocuSign template, but the main Excel sheet was named ‘DocuSign.’ The maldoc downloads the Bazar payload, which in turn connects to another URL that downloads the related Bazar backdoor,” the Intel 471 report says.
In a December 2020 attack, a malicious DocuSign document was created with EtterSilent and sent in a phishing email pretending to be from a large appliance manufacturer. In actuality, the malicious document dropped the Trickbot banking Trojan onto the victim’s computer.
Cybercriminal gangs deploying BokBot, Gozi ISFB and QBot banking Trojans have also used EtterSilent, but with the added twist of using a well-known bulletproof hosting service, the Intel 471 report says. In each case, the EtterSilent malicious document contained numerous embedded URLs.
All of those domains resolved to one particular IP address. That address is tied to bulletproof infrastructure provided by Yalishanda.
Intel 471 considers Yalishanda one of the most prolific bulletproof hosting services now operating. The use of bulletproof hosting services helps keep the malicious infrastructure used by cybercriminal groups and fraudsters hidden from law enforcement agencies, RiskIQ recently reported (see: Magecart Groups Hide Behind ‘Bulletproof’ Hosting Service).
The Big Picture
While the continually updated malicious document builder EtterSilent alone poses a threat, Intel 471 says the ecosystem in which it operates is a bigger danger. The fact that many groups use the document builder shows how these attackers use darknet marketplaces to find tools and combine them.
“When a product takes off in the marketplace, users will rush to obtain it and find unique ways to use it in order to fit their needs,” Intel 471 says. “Different players specialize in their respective area, whether that be robust hosting, spam infrastructure, maldoc builders, or malware as a service, and find ways to leverage each other’s products in services by working together.”