$7 Million Digital Advertising Scam: Russian Man Convicted
Cybercrime
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Self-Professed ‘King of Fraud’ Aleksandr Zhukov Ran Ads on Fake Sites

A Russian man has been convicted of bilking advertisers out of more than $7 million in payments for online ads that were never viewed by real humans.
See Also: Live Webinar | The Role of Passwords in the Hybrid Workforce
On Friday, Aleksandr Zhukov, 41, was convicted by a federal jury of four charges – including wire fraud and money laundering – as part of the so-called Methbot scheme.
The gang allegedly referred to its scheme as “Metan” – the Russian word for methane – although it’s also been referred to as Methbot by the FBI and prosecutors, and later as Media Methane, which was the name of the company owned by Zhukov, with offices in Russia and Bulgaria.
Zhukov and other members of his operation secured agreements with advertising networks to display their ads on sites, then earned a commission for every ad that someone viewed.
But according to court documents, from September 2014 through December 2016, Zhukov and his associates instead created fake sites, and programmed data centers to create fake users, to make it appear that real individuals were viewing the advertising.
“Zhukov represented to others that he ran a legitimate ad network that delivered advertisements to real human internet users accessing real internet web pages,” according to a superseding indictment filed on Feb. 12, 2020.
“In fact, Zhukov faked both the users and the webpages: he and his co-conspirators programmed computers that they had rented from commercial data centers in the United States and elsewhere to load advertisements on fabricated webpages, via an automated program, in order to fraudulently obtain digital advertising revenue,” it says.
Methbot Scheme
Prosecutors said Methbot generated billions of fake ad views – aka impressions – before it was shut down.
Victims of the scheme “included The New York Times, The New York Post, Comcast, Nestle Purina, the Texas Scottish Rite Hospital for Children and Time Warner Cable,” the Department of Justice says in a news release. “Discussing the scheme with a co-conspirator, Zhukov boasted about the money he would earn and referred to himself as the ‘king of fraud.'”
Zhukov was arrested in Bulgaria in November 2018 on a provisional U.S. arrest warrant. He was extradited to the United States in January 2019, and entered a plea of not guilty to the charges against him. The three-week trial against him concluded on Friday.
“After evaluating the evidence and wading through the complexities of digital advertising on the internet, the jury recognized the defendant for who he is – a fraudster who used computer code to steal millions from U.S. companies,” says Mark J. Lesko, the acting U.S. Attorney for the Eastern District of New York.
“Zhukov may have thought that he could get away with his fraud by carrying it out from halfway around the world, but this verdict sends a powerful message that U.S. law enforcement will bring such cybercriminals to justice, wherever they are,” Lesko says.
Methbot: Data Center Scheme
Zhukov was first publicly outed in a 13-count indictment, unsealed in November 2018, charging him and four other Russian nationals – Boris Timokhin, Mikhail Andreev, Denis Avdeev, Dmitry Novikov – with running Media Methane, assisted by Kazakhstan national Sergey Ovsyannikov.
Methbot earned money by creating fake users to interact with online advertising – generating so-called advertising impressions – to fraudulently receive payment from legitimate advertising networks, according to court documents.
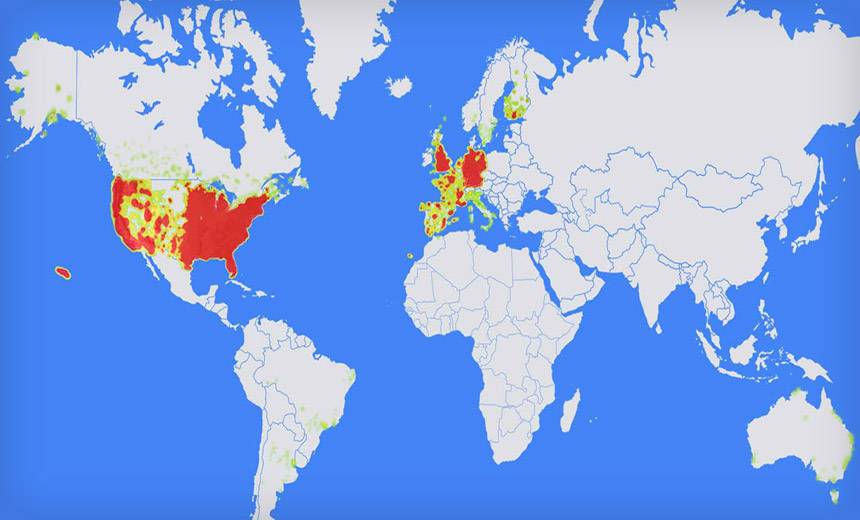
Prosecutors say Methbot’s operators rented more than 2,000 computer servers and spoofed more than 6,000 real domains as part of their scheme, and also leased more than 650,000 IP addresses, to make it appear that end users were coming from actual internet service providers.
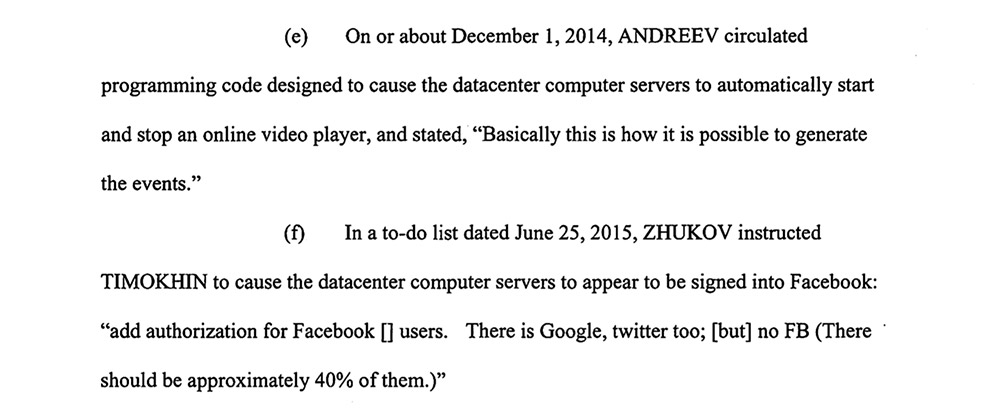
“To create the illusion that real human internet users were viewing the advertisements loaded onto these fabricated websites, the defendants programmed the data center servers to simulate the internet activity of human internet users: browsing the internet through a fake browser, using a fake mouse to move around and scroll down a webpage, starting and stopping a video player midway, and falsely appearing to be signed into Facebook,” the Justice Department says.
The scheme was disrupted in December 2016 after cybersecurity firm White Ops – now known as Human – published a report analyzing the operation and listing IP addresses used by attackers, which security firms quickly moved to block. White Ops said it had seen the operation scale up dramatically in October 2016, “reaching as many as 137 million impressions per day.”
After Media Methane, 3ve Launched
The aforementioned six suspects, as well as Russian national Aleksandr Isaev and Kazakhstan national Yevgeniy Timchenko, were also charged in the indictment with running another digital ad fraud scheme called 3ve, that has been tied to at least $29 million in fraud.
Pronounced “Eve,” the suspects allegedly began the scheme in December 2015, after Methbot was disrupted.
In 2017, a working group comprised of 17 firms – including Google, Facebook, Verizon subsidiary Oath and White Ops – banded together to attempt to secretly track 3ve, then shared their findings with law enforcement.
The scheme ran until October 2018, when Ovsyannikov was arrested in Malaysia. In November 2018, Zhukov was arrested in Bulgaria and Timchenko in Estonia, all based on provisional U.S. arrest warrants.
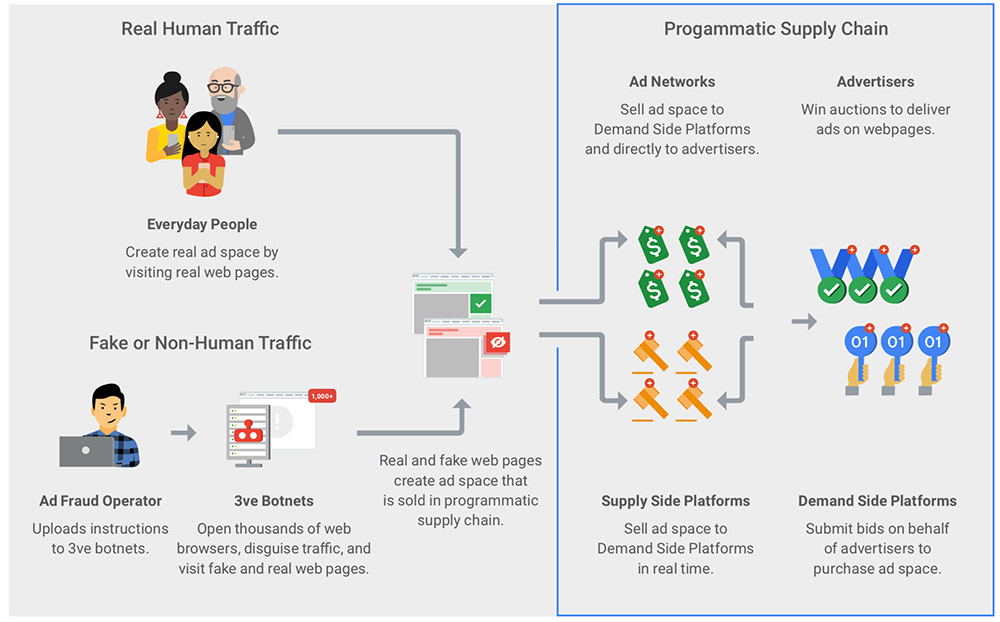
Prosecutors said 3ve used a botnet composed of more than 1.7 million PCs on which attackers had surreptitiously installed 3ve.2 botnet malware. According to the court documents, the malicious code surreptitiously “used hidden browsers … to download fabricated webpages and load ads onto those fabricated webpages,” generating fake advertising impressions to earn attackers fraudulent compensation from legitimate advertising networks.
2 Guilty Pleas
In September 2019, Ovsyannikov and Timchenko pleaded guilty in U.S. federal court to multiple charges.
In February, Timchenko agreed to forfeit funds held in Swiss, Romanian and Kazakhstani bank accounts worth more than $4.5 million, and was sentenced to time served. He was released on a year’s probation – unless he was “voluntarily or involuntarily deported” – and ordered to pay a fine of $35,000.
Ovsyannikov has yet to be sentenced.
Of the eight men named in the superseding indictment, only three have appeared in a U.S. courtroom. The others, all Russian nationals, remain at large.